Introduction to Data Communication and Network Topology
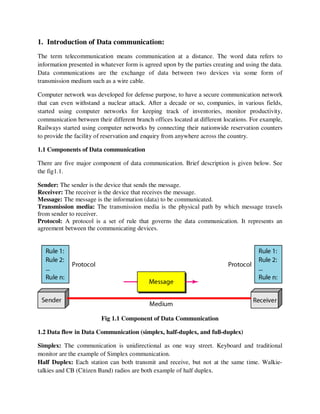
- 1. 1. Introduction of Data communication: The term telecommunication means communication at a distance. The word data refers to information presented in whatever form is agreed upon by the parties creating and using the data. Data communications are the exchange of data between two devices via some form of transmission medium such as a wire cable. Computer network was developed for defense purpose, to have a secure communication network that can even withstand a nuclear attack. After a decade or so, companies, in various fields, started using computer networks for keeping track of inventories, monitor productivity, communication between their different branch offices located at different locations. For example, Railways started using computer networks by connecting their nationwide reservation counters to provide the facility of reservation and enquiry from anywhere across the country. 1.1 Components of Data communication There are five major component of data communication. Brief description is given below. See the fig1.1. Sender: The sender is the device that sends the message. Receiver: The receiver is the device that receives the message. Message: The message is the information (data) to be communicated. Transmission media: The transmission media is the physical path by which message travels from sender to receiver. Protocol: A protocol is a set of rule that governs the data communication. It represents an agreement between the communicating devices. Fig 1.1 Component of Data Communication 1.2 Data flow in Data Communication (simplex, half-duplex, and full-duplex) Simplex: The communication is unidirectional as one way street. Keyboard and traditional monitor are the example of Simplex communication. Half Duplex: Each station can both transmit and receive, but not at the same time. Walkie- talkies and CB (Citizen Band) radios are both example of half duplex.
- 2. Full Duplex: In full duplex both station can transmit and receive simultaneously. Modern telephone network is the full duplex communication. Fig1.2 Data flow in Data Communication 1.3 Data Representation In Different format data can be represented like • Text: Most of the text is in format of ASCII (American Code of Information Exchange) • Number: Number is represented by bit patterns • Images: There is several method of representing color images. One popular method is RGB. • Audio: This refers to the recording or broadcasting of sound or music. 2. Network A network is a set of devices (often referred to as nodes) connected by communication links. A node can be a computer, printer, or any other device capable of sending and/or receiving data generated by other nodes on the network. Real network is the combination of hardware and software. 2.1 Types of network connection There are two types of connection network connection. Point-to-point and multipoint. See the fig2.1 Point-to-point: A point-to point connection provides a dedicated links between to devices. The entire capacity of the link is reserved for transmission between those two devices. Communication between to PC using cross Ethernet cable is point-to-point connection. Multipoint: In multi point connection, more that two devices share the single link. Like hub connection.
- 3. Fig2.1 Types of network connection 2.2 Physical topology of network The term physical topology refers to the way in which a network is laid out physically. The Topology of a network is the geometric representation of all the links and Linking devices (usually called nodes) to one other. There are four major types of topology available (Fig2.2). Fig2.2 Topology of Network 2.2.1 Fully connected mesh topology In mesh topology every devices has dedicated point to point link to every other devices (Fig2.3). A mesh network having n no.s of node require n*(n-1)/2 physical link to connect n devices. So every device will have (n-1) input/output ports. Fig2.3 Mesh topology
- 4. Advantage: 1. Dedicated link ensure that each connection carry its own data load, eliminating the traffic problem. 2. Mesh topology is robust 3. Privacy and security 4. Fault identification and isolation is easy Disadvantage: 1. Huge amount of cabling and I/O ports required. 2. Installation and reconnection is difficult 3. Required hardware to connect each link will be expensive. 2.2.2 Star topology In star topology each devices has point to point link only to a central controller, usually called a hub (fig2.4). Fig.2.4 Star topology Advantage: 1. Less expensive than star topology 2. Easy to install and reconfiguration 3. Robustness Disadvantage: 1. Failure of central hub will affect the entire network 2.2.3 Bus topology The bus topology is multipoint. One long cable act as backbone to link all the devices in a network (Fig2.5). A drop line is a connector running between the device and main cable. As Signal travels along the back bone, some of its energy transform into heat and signal become weaker and weaker. Fig2.5 Bus Topology Advantage: 1. Ease to install 2. Less caballing than mesh or star. Disadvantage: 1. Difficult reconnection and fault isolation
- 5. 2. Difficult to add new node 3. Fault or break in the bus cable stops all the transmission Tree Topology: Sometimes extension of bus topology is called tree topology. Tree topology is commonly used in cascading equipments. For example, you have a repeater box with 8-port, as far as you have eight stations, this can be used in a normal fashion. But if you need to add more stations then you can connect two or more repeaters in a hierarchical format (tree format) and can add more stations (Fig2.6). Fig2.6 Tree Topology 2.2.4 Ring topology A ring network is a network topology in which each node connects to exactly two other nodes, forming a single continuous pathway for signals through each node - a ring(Fig2.7). Data travels from node to node, with each node along the way handling every packet. FDDI (Fiber Distributed Data Interface) network is an example of ring topology. Fig2.7 Ring Topology Advantage: 1. Very orderly network where every device has access to the token and the opportunity to transmit 2. Performs better than a bus topology under heavy network load
- 6. 3. Does not require a central node to manage the connectivity between the computers 4. Due to the point to point line configuration of devices with a device on either side (each device is connected to its immediate neighbor), it is quite easy to install and reconfigure since adding or removing a device requires moving just two connections. 5. Point to point line configuration makes it easy to identify and isolate faults. Disadvantage: 1. One malfunctioning workstation can create problems for the entire network. This can be solved by using a dual ring or a switch that closes off the break. 2. Moving, adding and changing the devices can affect the network 3. Communication delay is directly proportional to number of nodes in the network 4. Bandwidth is shared on all links between devices 5. More difficult to configure than a Star: node adjunction ⇨ Ring shutdown and reconfiguration 2.2.5 Some example of Hybrid network Hybrid network is the combination of different physical topology of connection to form single network. A star backbone with three bus networks LAN connecting 12 computers to a hub in a closet Fig2.8a Fig2.8b 3. Classification based on Scale of Network Alternative criteria for classifying networks are their scale. They are divided into Local Area (LAN), Metropolitan Area Network (MAN) and Wide Area Networks (WAN). 3.1 Local Area Network (LAN) LAN is usually privately owned and links the devices in a single office, building or campus of up to few kilometers in size. These are used to share resources (may be hardware or software resources) and to exchange information. LANs are distinguished from other kinds of networks by three categories: their size, transmission technology and topology. LANs are restricted in size, which means that their worst-case transmission time is bounded and known in advance. Hence this is more reliable as compared to MAN and WAN. Knowing this bound makes it possible to use certain kinds of design that would not otherwise be possible. It also simplifies network management. LAN typically used transmission technology consisting of single cable to which all machines are connected. Traditional LANs run at speeds of 10 to 100 Mbps (but now much higher speeds can
- 7. be achieved). The most common LAN topologies are bus, ring and star. A typical LAN is shown in fig 3.1 Fig 3.1 LAN 3.2 Metropolitan Area Networks (MAN) MAN is designed to extend over the entire city. It may be a single network as a cable TV network or it may be means of connecting a number of LANs into a larger network so that resources may be shared as shown in Fig. 3.2. For example, a company can use a MAN to connect the LANs in all its offices in a city. MAN is wholly owned and operated by a private company or may be a service provided by a public company. Fig. 3.2 MAN
- 8. The main reason for distinguishing MANs as a special category is that a standard has been adopted for them. It is DQDB (Distributed Queue Dual Bus) or IEEE 802.6. 3.3 Wide Area Network (WAN) WAN provides long-distance transmission of data, voice, image and information over large geographical areas that may comprise a country, continent or even the whole world. In contrast to LANs, WANs may utilize public, leased or private communication devices, usually in combinations, and can therefore span an unlimited number of miles as shown in Fig. 3.3. A WAN that is wholly owned and used by a single company is often referred to as enterprise network. Fig. 3.3 WAN 4. The Internet The Internet has revolutionized many aspects of our daily lives. It has affected the way we do business as well as the way we spend our leisure time. The Internet is a communication system that has brought a wealth of information to our fingertips and organized it for our use. Internet is a collection of networks or network of networks. Various networks such as LAN and WAN connected through suitable hardware and software to work in a seamless manner. Schematic diagram of the Internet is shown in Fig. 4.1. It allows various applications such as e- mail, file transfer, remote log-in, World Wide Web, Multimedia, etc run across the internet. The basic difference between WAN and Internet is that WAN is owned by a single organization while internet is not so. But with the time the line between WAN and Internet is shrinking, and
- 9. these terms are sometimes used interchangeably. Also Fig 4.2 has shown the Aircel Network in India connection as Internet service provider. Fig.4.1 Internet(Network of Networks) Fig. 4.2 Aircel Network
- 10. 5. Protocols and Standard Protocol is set of rules that govern data communication. For communication the entities must agreed upon a protocol. A protocol defines what is communicated, how it is communicated and when it is communicated. The key elements of protocol are syntax, semantics and timing. Syntax: The term syntax refers to the structure or format of the data, meaning the order in which they are presented. Semantics: The word semantics refers to the meaning of each section of bits. How is a particular pattern to be interpreted, and what action is to be taken based on that interpretation? Timing: the term timing refers to two characteristics: when data should be sent and how fast they can be sent. Standards: Standards provide guidelines to manufacturers, vendors, government agencies and other service providers to ensure the kind of interconnectivity necessary in today’s marketplace and in international communications. Data communication standards fall in two categories: de facto (meaning “by fact” or “by convention”) and de jure (meaning “by law” or “by regulation”). Standard Organizations: • International Organization for Standardization (ISO) • International Telecom Unit (ITU) • American National Standards Institute (ANSI) • Institute of Electrical and Electronics Engineers (IEEE) • Electronic Industries Association(EIA) 6. Reference Model: Network architectures define the standards and techniques for designing and building communication systems for computers and other devices. Network architectures are defined by two basic reference model: OSI (Open Systems Interconnection) and TCP/IP(Transmission Control Protocol/Internet Protocol). To reduce the design complexity, most of the networks are organized as a series of layers or levels, each one build upon one below it. The basic idea of a layered architecture is to divide the design into small pieces. Each layer adds to the services provided by the lower layers in such a manner that the highest layer is provided a full set of services to manage communications and run the applications. The benefits of the layered models are modularity and clear interfaces, i.e. open architecture and comparability between the different providers' components. The basic elements of a layered model are services, protocols and interfaces. A service is a set of actions that a layer offers to another (higher) layer. Protocol is a set of rules that a layer uses to exchange information with a peer entity. These rules concern both the contents and the order of the messages used. Between the layers service interfaces are defined. The messages from one layer to another are sent through those interfaces. 6.1 Open System Interconnection Reference Model The Open System Interconnection (OSI) reference model describes how information from a software application in one computer moves through a network medium to a software application in another computer. The OSI reference model is a conceptual model composed of seven layers(Fig 6.1), each specifying particular network functions. The model was developed by the International Organization for Standardization (ISO) in 1984, and it is now considered the
- 11. primary architectural model for inter-computer communications. A task or group of tasks is then assigned to each of the seven OSI layers. LAYERS IN THE OSI MODEL: • Physical Layer • Data Link Layer • Network Layer • Transport Layer • Session Layer • Presentation Layer • Application Layer Fig 6.1 Interaction between layers in the OSI model Fig 6.2 An exchange using the OSI model
- 12. 1. Physical Layer: Controls the transmission of the actual data onto the network cable(Fig 6.3). It defines the electrical signals, line states and encoding of the data and the connector types used. An example is 10BaseT. The Physical layer is responsible for transmitting individual bits from one node to the nest. It deals with the mechanical and electrical specification of the interface and transmission media. Fig. 6.3 Physical layer Job of Physical Layer: 1. Physical Characteristics of interface and media 2. Representation of bit 3. Data rate 4. Synchronization of bits 2. Data-Link Layer: This layer takes the data frames or messages from the Network Layer and provides for their actual transmission. At the receiving computer, this layer receives the incoming data and sends it to the network layer for handling. The Data-Link Layer also provides error-free delivery of data between the two computers by using the physical layer. It does this by packaging the data from the Network Layer into a frame, which includes error detection information. At the receiving computer, the Data-Link Layer reads the incoming frame, and generates its own error detection information based on the received frames data. After receiving the entire frame, it then compares its error detection value with that of the incoming frames, and if they match, the frame has been received correctly. Fig. 6.4 Data-Link Layer Data link layer is responsible for transmitting frame from one node to the next node, means hop to hop delivery (Fig. 6.5). Job of Data link layer: 1. Framing 2. Physical addressing
- 13. 3. Flow control 4. Error control 5. Access control Fig. 6.5 Hop-to-hop delivery 3. Network Layer: This is responsible for addressing messages and data so they are sent to the correct destination, and for translating logical addresses and names into physical addresses. This layer is also responsible for finding a path through the network to the destination computer. Fig. 6.6 Network Layer Network layer is responsible for source to destination delivery possible across multiple networks whereas the data link layer oversees the delivery of the packet between two systems on the same network. The network layer is responsible for the delivery of individual packets from the source host to the destination host (Fig.6.7). Job of Network layer: 1. Interface between the host and the network (the network layer is typically the boundary between the host and subnet) 2. Routing
- 14. 3. Congestion and deadlock 4. Internetworking (A path may traverse different network technologies (e.g., Ethernet, point-to-point links, etc.) Fig. 6.7 Source-to-destination delivery 4. Transport Layer: Ensures that data is delivered error free, in sequence and with no loss, duplications or corruption. This layer also repackages data by assembling long messages into lots of smaller messages for sending, and repackaging the smaller messages into the original larger message at the receiving end. The transport layer is responsible for the delivery of a message from one process to another (Fig. 6.8). Fig. 6.8 Process to Process communication 5. Session Layer: Allows two applications to establish, use and disconnect a connection between them called a session. Provides for name recognition and additional functions like security, which are needed to allow applications to communicate over the network. The session layer is responsible for dialog control and synchronization.
- 15. Fig. 6.9 Session Layer 6. Presentation Layer: Determines the format used to exchange data among networked computers. The presentation layer is responsible for translation, compression, and encryption. 1. Encoding data in a standard agreed upon way. 2. It manages the abstract data structures and converts from representation used inside computer to network standard representation and back. Fig. 6.10 Presentation layer 7. Application Layer: Provides Applications with access to network services. The application layer is responsible for providing services to the user. Fig. 6.11 Application Layer
- 16. Fig. 6.12 Summary of OSI Model Layers 6.2 TCP/IP Model The layers in the TCP/IP protocol suite do not exactly match those in the OSI model. The original TCP/IP protocol suite was defined as having four layers: host-to-network, internet, transport, and application. However, when TCP/IP is compared to OSI, we can say that the TCP/IP protocol suite is made of five layers: physical, data link, network, transport, and application. The Fig 6.13 shows how TCP/IP model encapsulate the layers and respective functions of the different layers of OSI model. Fig. 6.13
- 17. 6.2.1 Addresses in TCP/IP Four levels of addresses are used in an internet employing the TCP/IP protocols: physical, logical, port, and specific (Fig. 6.14). Also Fig. 6.15 shows the relationship of layers and addresses in TCP/IP model Fig.6.14 Addresses in TCP/IP Fig. 6.15 Relationship of layers and addresses in TCP/IP Example: How physical address and IP address helps in Data communication (Fig. 6.16) Fig. 6.16 shows a part of an internet with two routers connecting three LANs. Each device (computer or router) has a pair of addresses (logical and physical) for each connection. In this case, each computer is connected to only one link and therefore has only one pair of addresses. Each router, however, is connected to three networks (only two are shown in the figure). So each router has three pairs of addresses, one for each connection. The physical addresses will change from hop to hop, but the logical addresses usually remain the same.
- 18. Fig. 6.16 Example: How Port address is responsible for Process to process communication in Transport layer. Fig. 6.17 shows two computers communicating via the Internet. The sending computer is running three processes at this time with port addresses a, b, and c. The receiving computer is running two processes at this time with port addresses j and k. Process a in the sending computer needs to communicate with process j in the receiving computer. Note that although physical addresses change from hop to hop, logical and port addresses remain the same from the source to destination. Fig. 6.17
- 19. Difference between OSI Model and TCP/IP Model OSI Model TCP/IP Model OSI: Open Systems Interconnection. It was developed by ISO as a first step toward international standardization of the protocol used in various layers. It deals with connecting open system. TCP/IP: Transport Control Protocol/Internet Protocol. TCP is used in connection with IP and operates at the transport layer. IP is the set of convention used to pass packets from one host to another. OSI makes the distinction between services, interfaces, and protocol. TCP/IP does not originally clearly distinguish between services, interface, and protocol. The OSI model was devised before the protocols were invented. It can be made to work in diverse heterogeneous networks. TCP/IP model was just a description of the existing protocols. The model and the protocol fit perfectly. OSI has seven layers. Application, Presentation, Session, Transport, Network, Data link, Physical. TCP/IP has four layers. Application, Transport, Network layer, Data-Link Layer, Physical Layer. OSI emphasis on providing a reliable data transfer service, Each layer of the OSI model detects and handles errors, all data transmitted includes checksums. The transport layer checks source-destination reliability. TCP/IP treats reliability as an end to end Problem. The transport layer handles all error detection and recovery; it was checksums, acknowledgments, and timeouts to control transmissions and provides end-to-end verification. Host on OSI implementations do not handle network operations. TCP/IP hosts participate in most network protocols. A connection-oriented protocol. A connectionless oriented protocol. Virtual circuit approach is used. Data-gram approach is used. Logical connection or virtual circuit is established before any packet are sent i.e. Call Setup phase. Each packet is treated independently. OSI Model accommodates variable-length addresses. IP supports fixed, 32-bit address. Similarity of OSI Model and TCP/IP Model o Both are based on the concept of a stack of independent protocols. o The functionality of the layers is roughly similar.
