TCP Fairness for Uplink and Downlink Flows in WLANs
•
0 gefällt mir•311 views
TCP Fairness for Uplink and Downlink Flows in WLANs
Melden
Teilen
Melden
Teilen
Empfohlen
To Get any Project for CSE, IT ECE, EEE Contact Me @ 09849539085, 09966235788 or mail us - ieeefinalsemprojects@gmail.com-Visit Our Website: www.finalyearprojects.orgDOTNET 2013 IEEE MOBILECOMPUTING PROJECT Delay optimal broadcast for multihop...

DOTNET 2013 IEEE MOBILECOMPUTING PROJECT Delay optimal broadcast for multihop...IEEEGLOBALSOFTTECHNOLOGIES
Empfohlen
To Get any Project for CSE, IT ECE, EEE Contact Me @ 09849539085, 09966235788 or mail us - ieeefinalsemprojects@gmail.com-Visit Our Website: www.finalyearprojects.orgDOTNET 2013 IEEE MOBILECOMPUTING PROJECT Delay optimal broadcast for multihop...

DOTNET 2013 IEEE MOBILECOMPUTING PROJECT Delay optimal broadcast for multihop...IEEEGLOBALSOFTTECHNOLOGIES
Weitere ähnliche Inhalte
Was ist angesagt?
Was ist angesagt? (20)
Multi-Channel Multi-Interface Wireless Network Architecture

Multi-Channel Multi-Interface Wireless Network Architecture
Andere mochten auch
Andere mochten auch (17)
On Multihop Distances in Wireless Sensor Networks with Random Node Locations

On Multihop Distances in Wireless Sensor Networks with Random Node Locations
Energy efficient cluster-based service discovery in wireless sensor networks

Energy efficient cluster-based service discovery in wireless sensor networks
An efficient hybrid peer to-peersystemfordistributeddatasharing

An efficient hybrid peer to-peersystemfordistributeddatasharing
Admission control and routing in multi hop wireless networks

Admission control and routing in multi hop wireless networks
Stichting van Jacques van Ypersele kreeg geld van rijke Amerikanen

Stichting van Jacques van Ypersele kreeg geld van rijke Amerikanen
A novel pause count backoff algorithm for channel access

A novel pause count backoff algorithm for channel access
Vorstelijk Vermogen - interview Thierry Debels - P-Magazine

Vorstelijk Vermogen - interview Thierry Debels - P-Magazine
Waarom proces van Delphine wellicht met sisser afloopt

Waarom proces van Delphine wellicht met sisser afloopt
Ähnlich wie TCP Fairness for Uplink and Downlink Flows in WLANs
Ähnlich wie TCP Fairness for Uplink and Downlink Flows in WLANs (20)
Efficient and Fair Bandwidth Allocation AQM Scheme for Wireless Networks

Efficient and Fair Bandwidth Allocation AQM Scheme for Wireless Networks
Comparative Analysis of Different TCP Variants in Mobile Ad-Hoc Network 

Comparative Analysis of Different TCP Variants in Mobile Ad-Hoc Network
Iaetsd an effective approach to eliminate tcp incast

Iaetsd an effective approach to eliminate tcp incast
4..[26 36]signal strength based congestion control in manet![4..[26 36]signal strength based congestion control in manet](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![4..[26 36]signal strength based congestion control in manet](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
4..[26 36]signal strength based congestion control in manet
11.signal strength based congestion control in manet

11.signal strength based congestion control in manet
Performance Evaluation of TCP with Adaptive Pacing and LRED in Multihop Wirel...

Performance Evaluation of TCP with Adaptive Pacing and LRED in Multihop Wirel...
Performance Evaluation of a Layered WSN Using AODV and MCF Protocols in NS-2

Performance Evaluation of a Layered WSN Using AODV and MCF Protocols in NS-2
Research Inventy : International Journal of Engineering and Science

Research Inventy : International Journal of Engineering and Science
Predictable Packet Lossand Proportional Buffer Scaling Mechanism

Predictable Packet Lossand Proportional Buffer Scaling Mechanism
Mehr von ambitlick
Mehr von ambitlick (20)
DCIM: Distributed Cache Invalidation Method for Maintaining Cache Consistency...

DCIM: Distributed Cache Invalidation Method for Maintaining Cache Consistency...
Moderated group authoring system for campus wide workgroups

Moderated group authoring system for campus wide workgroups
Efficient spread spectrum communication without pre shared secrets

Efficient spread spectrum communication without pre shared secrets
Adaptive weight factor estimation from user review 1

Adaptive weight factor estimation from user review 1
Moderated group authoring system for campus wide workgroups

Moderated group authoring system for campus wide workgroups
Efficient spread spectrum communication without pre shared secrets

Efficient spread spectrum communication without pre shared secrets
Comments on “mabs multicast authentication based on batch signature”

Comments on “mabs multicast authentication based on batch signature”
Energy-Efficient Protocol for Deterministic and Probabilistic Coverage In Sen...

Energy-Efficient Protocol for Deterministic and Probabilistic Coverage In Sen...
Estimating Parameters of Multiple Heterogeneous Target Objects Using Composit...

Estimating Parameters of Multiple Heterogeneous Target Objects Using Composit...
A Privacy-Preserving Location Monitoring System for Wireless Sensor Networks

A Privacy-Preserving Location Monitoring System for Wireless Sensor Networks
Kürzlich hochgeladen
Mehran University Newsletter is a Quarterly Publication from Public Relations OfficeMehran University Newsletter Vol-X, Issue-I, 2024

Mehran University Newsletter Vol-X, Issue-I, 2024Mehran University of Engineering & Technology, Jamshoro
Making communications land - Are they received and understood as intended? webinar
Thursday 2 May 2024
A joint webinar created by the APM Enabling Change and APM People Interest Networks, this is the third of our three part series on Making Communications Land.
presented by
Ian Cribbes, Director, IMC&T Ltd
@cribbesheet
The link to the write up page and resources of this webinar:
https://www.apm.org.uk/news/making-communications-land-are-they-received-and-understood-as-intended-webinar/
Content description:
How do we ensure that what we have communicated was received and understood as we intended and how do we course correct if it has not.Making communications land - Are they received and understood as intended? we...

Making communications land - Are they received and understood as intended? we...Association for Project Management
Kürzlich hochgeladen (20)
ICT role in 21st century education and it's challenges.

ICT role in 21st century education and it's challenges.
General Principles of Intellectual Property: Concepts of Intellectual Proper...

General Principles of Intellectual Property: Concepts of Intellectual Proper...
On National Teacher Day, meet the 2024-25 Kenan Fellows

On National Teacher Day, meet the 2024-25 Kenan Fellows
UGC NET Paper 1 Mathematical Reasoning & Aptitude.pdf

UGC NET Paper 1 Mathematical Reasoning & Aptitude.pdf
Food safety_Challenges food safety laboratories_.pdf

Food safety_Challenges food safety laboratories_.pdf
Making communications land - Are they received and understood as intended? we...

Making communications land - Are they received and understood as intended? we...
Python Notes for mca i year students osmania university.docx

Python Notes for mca i year students osmania university.docx
Salient Features of India constitution especially power and functions

Salient Features of India constitution especially power and functions
Kodo Millet PPT made by Ghanshyam bairwa college of Agriculture kumher bhara...

Kodo Millet PPT made by Ghanshyam bairwa college of Agriculture kumher bhara...
Unit-IV; Professional Sales Representative (PSR).pptx

Unit-IV; Professional Sales Representative (PSR).pptx
Micro-Scholarship, What it is, How can it help me.pdf

Micro-Scholarship, What it is, How can it help me.pdf
TCP Fairness for Uplink and Downlink Flows in WLANs
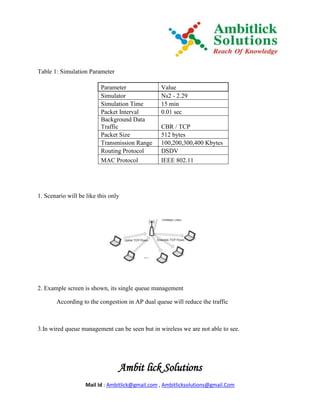
- 1. Table 1: Simulation Parameter Parameter Value Simulator Ns2 - 2.29 Simulation Time 15 min Packet Interval 0.01 sec Background Data Traffic CBR / TCP Packet Size 512 bytes Transmission Range 100,200,300,400 Kbytes Routing Protocol DSDV MAC Protocol IEEE 802.11 1. Scenario will be like this only 2. Example screen is shown, its single queue management According to the congestion in AP dual queue will reduce the traffic 3.In wired queue management can be seen but in wireless we are not able to see. Ambit lick Solutions Mail Id : Ambitlick@gmail.com , Ambitlicksolutions@gmail.Com
- 2. NETWORK MODULE Client-server computing or networking is a distributed application architecture that partitions tasks or workloads between service providers (servers) and service requesters, called clients. Often clients and servers operate over a computer network on separate hardware. A server machine is a high- performance host that is running one or more server programs which share its resources with clients. A client also shares any of its resources; Clients therefore initiate communication sessions with servers which await (listen to) incoming requests. PACKET SCHEDULING This packet scheduling policy is simple to implement, and yields good performance in the common case that node schedules are known, and information about node availability is accurate. A potential drawback is that a node crash (or other failure event) can lead to a number of wasted RTSs to the failed node. When added across channels, the number may exceed the limit of 7 retransmission attempts allowed for a single channel in the IEEE 802.11 Ambit lick Solutions Mail Id : Ambitlick@gmail.com , Ambitlicksolutions@gmail.Com
- 3. BANDWIDTH SHARING Approach where each node requests and grants as much bandwidth as possible at each turn. Additionally, we compare the RENO algorithm for packet scheduling to a First-In-First-Out (FIFO) scheduler where all the SDUs with the same next-hop are enqueued into the same buffer. For this purpose we simulate a network with an increasing number of nodes, from 2 to 10, arranged in a chain topology. Each node has one traffic flow directed to the chain end-point node, carried with a constant bit-rate stream of 1000 bytes packets emulating infinite bandwidth demands. Congestion control has been extensively studied for networks running a single protocol. However, when sources sharing the same network react to different congestion signals, the existing duality model no longer explains the behavior of bandwidth allocation. The existence and uniqueness properties of equilibrium in heterogeneous protocol case are examined. BURSTY TRAFFIC The end-to-end throughput (or throughput, for short), which is defined as the number of bits received by the destination node per second for a given traffic flow, without any MAC overhead. As it can be seen, the throughput steeply decreases as the number of nodes increases, regardless of the scheme adopted. This is because an increasing fraction of the channel capacity is employed to relay packets at intermediate nodes. For instance, with three nodes the end-to-end Ambit lick Solutions Mail Id : Ambitlick@gmail.com , Ambitlicksolutions@gmail.Com
- 4. throughput is about 2/3 of the available raw bandwidth: 1/3 is consumed by the traffic flow that is one hop from the destination, and 2/3 is consumed by the other one that has a length of two hops. Ambit lick Solutions Mail Id : Ambitlick@gmail.com , Ambitlicksolutions@gmail.Com
