Audio Watermarking - JIIT noida 2013-14 by Vaibhav Arora and Isha Garg
•Als PPT, PDF herunterladen•
1 gefällt mir•512 views
Melden
Teilen
Melden
Teilen
Weitere ähnliche Inhalte
Andere mochten auch
Andere mochten auch (15)
DIGITAL AUDIO WATERMARKING ALGORITHM BASED ON NEURAL NETWORKS

DIGITAL AUDIO WATERMARKING ALGORITHM BASED ON NEURAL NETWORKS
Ähnlich wie Audio Watermarking - JIIT noida 2013-14 by Vaibhav Arora and Isha Garg
Ähnlich wie Audio Watermarking - JIIT noida 2013-14 by Vaibhav Arora and Isha Garg (20)
Black Hat '15: Spread Spectrum Satcom Hacking: Attacking The GlobalStar Simpl...

Black Hat '15: Spread Spectrum Satcom Hacking: Attacking The GlobalStar Simpl...
DEF CON 23: Spread Spectrum Satcom Hacking: Attacking The GlobalStar Simplex ...

DEF CON 23: Spread Spectrum Satcom Hacking: Attacking The GlobalStar Simplex ...
FutureComm 2010: Making Real-Time Video Work Over the Internet

FutureComm 2010: Making Real-Time Video Work Over the Internet
Mobile communication and computing gsm-radio-interface-140720014203-phpapp02.pdf

Mobile communication and computing gsm-radio-interface-140720014203-phpapp02.pdf
Kürzlich hochgeladen
Mehran University Newsletter Vol-X, Issue-I, 2024

Mehran University Newsletter Vol-X, Issue-I, 2024Mehran University of Engineering & Technology, Jamshoro
Explore beautiful and ugly buildings. Mathematics helps us create beautiful d...

Explore beautiful and ugly buildings. Mathematics helps us create beautiful d...christianmathematics
Kürzlich hochgeladen (20)
Web & Social Media Analytics Previous Year Question Paper.pdf

Web & Social Media Analytics Previous Year Question Paper.pdf
Measures of Central Tendency: Mean, Median and Mode

Measures of Central Tendency: Mean, Median and Mode
Explore beautiful and ugly buildings. Mathematics helps us create beautiful d...

Explore beautiful and ugly buildings. Mathematics helps us create beautiful d...
Beyond the EU: DORA and NIS 2 Directive's Global Impact

Beyond the EU: DORA and NIS 2 Directive's Global Impact
SECOND SEMESTER TOPIC COVERAGE SY 2023-2024 Trends, Networks, and Critical Th...

SECOND SEMESTER TOPIC COVERAGE SY 2023-2024 Trends, Networks, and Critical Th...
Seal of Good Local Governance (SGLG) 2024Final.pptx

Seal of Good Local Governance (SGLG) 2024Final.pptx
Unit-IV; Professional Sales Representative (PSR).pptx

Unit-IV; Professional Sales Representative (PSR).pptx
Audio Watermarking - JIIT noida 2013-14 by Vaibhav Arora and Isha Garg
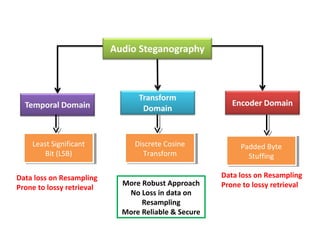
- 1. Least Significant Bit (LSB) Least Significant Bit (LSB) Discrete Cosine Transform Discrete Cosine Transform Padded Byte Stuffing Padded Byte Stuffing Data loss on Resampling Prone to lossy retrieval Data loss on Resampling Prone to lossy retrievalMore Robust Approach No Loss in data on Resampling More Reliable & Secure
- 2. DCT- Discrete Cosine Transform DCT- Discrete Cosine Transform
- 3. Embedding in Dual Channel – More SecurityEmbedding in Dual Channel – More Security Audio Sample Right Channel Left Channel Synchronization Code Selects the Channel Watermarked Audio Track Watermarked Audio Track
- 4. Inverse Discrete Cosine Transform Audio DataAudio Data Block 1 Block 1 Block 2 Block 2 Block 3 Block 3 Block n Block n Discrete Cosine Transform DCT Data DCT Data DCT Data DCT Data DCT Data DCT Data DCT Data DCT Data DCT’ Data DCT’ Data DCT’ Data DCT’ Data Watermark Embedded in AudioWatermark Embedded in Audio Selecting Mid-Range of DCT BlockSelecting Mid-Range of DCT Block … Mid Range … …
- 5. 5 6 7 8 1 2 3 4 13 14 15 16 9 10 11 12 8 5 6 7 4 1 2 3 16 13 14 15 12 9 10 11 1 2 3 4 13 14 15 16 9 10 11 12 5 6 77 8 Original Watermark Circular Shifted Watermark- Type 1 Circular Shifted Watermark- Type 2 Circular Shifting of Original Watermark Circular Shifting of Original Watermark
- 6. Application of Detecting Distributor of unauthorized copy of Audio file based on the Algorithm Application of Detecting Distributor of unauthorized copy of Audio file based on the Algorithm APPLICATION
- 7. Watermark generation for client (unique key) Upload Audio Add Client for Audio Watermarked Audio is sent to client Unique Watermark stored in database for theft detection Login Panel Enter Client Details PUBLISHER MODULE
- 8. Watermark Extraction from audioUpload Audio Client Information DisplayedClient Information Displayed Fetching from Database [ FOUND ] DETECTION & TRACKING MODULE Login Panel KEY BASEDKEY BASED
