MC0087 Internal Assignment (SMU)
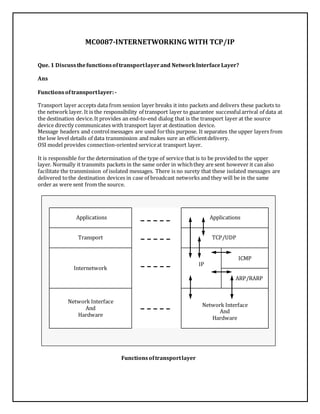
- 1. MC0087-INTERNETWORKING WITH TCP/IP Que. 1 Discuss the functions of transport layer and Network Interface Layer? Ans Functions of transport layer: - Transport layer accepts data from session layer breaks it into packets and delivers these packets to the network layer. It is the responsibility of transport layer to guarantee successful arrival of data at the destination device. It provides an end-to-end dialog that is the transport layer at the source device directly communicates with transport layer at destination device. Message headers and control messages are used for this purpose. It separates the upper layers from the low level details of data transmission and makes sure an efficient delivery. OSI model provides connection-oriented service at transport layer. It is responsible for the determination of the type of service that is to be provided to the upper layer. Normally it transmits packets in the same order in which they are sent however it can also facilitate the transmission of isolated messages. There is no surety that these isolated messages are delivered to the destination devices in case of broadcast networks and they will be in the same order as were sent from the source. Applications Applications Transport TCP/UDP Internetwork IP ICMP ARP/RARP Network Interface And Hardware Network Interface And Hardware Functions of transport layer
- 2. Network Interface Layer: - The Network Interface Layer (also called the Network Access Layer) sends TCP/IP packets on the network medium and receives TCP/IP packets off the network medium. TCP/IP was designed to be independent of the network access method, frame format, and medium. Therefore, you can use TCP/IP to communicate across differing network types that use LAN technologies – such as Ethernet and 802.11 wireless LAN – and WAN technologies –such as Frame Relay and Asynchronous Transfer Mode (ATM). By being independent of any specific network technology, TCP/IP can be adapted to new technologies. The Network Interface layer of the DARPA model encompasses the Data Link and Physical layers of the OSI model. The Internet layer of DARPA model does not take advantage of sequencing and acknowledgment services that might be present in the Data Link layer of the OSI model. The Internet layer assumes an unreliable Network Interface layer and that reliable communication through session establishment and the sequencing and acknowledgment of packets is the responsibility of either the Transport layer or the Application layer.
- 3. Que. 2 Brief the following a) ISDN b) X.25 Ans a) ISDN The ISDN Basic Rate Interface (BRI) usually supports two B-channels with a capacity of 64 kbps each, and a 16 kbps D-channel for control information. B-channels can be used for voice or data or just for data in a combined way. The ISDN Primary Rate Interface (PRI) can support many concurrent B-channel links and one 64 kbps D-channel. The PPP, LCP and NCP mechanisms are particularly useful in this situation in reducing or eliminating manual configuration and facilitating ease of communication between diverse implementations. The ISDN D-channel can also be use for sending PPP packets when suitably framed, but is limited in bandwidth and often restricts communication links to a local switch. PPP treats ISDN channels as bit- or octet-oriented synchronous links. These links must be full duplex, but can be either dedicated or circuit-switched. PPP presents an octet interface to the physical layer. There is no provision for sub-octets to be supplied or accepted. PPP does not impose any restrictions regarding transmission rate other than that of the particular ISDN channel interface. PPP does not require the use of control signals. When available, using such signals can allow greater functionality and performance. The D-channel interface requires NRZ encoding. b) X.25 This topic describes the encapsulation of IP over X.25 networks, in accordance with ISO/IEC and CCITT standards. IP over X.25 networks is documented by RFC 1356 (which obsoletes RFC 877). RFC 1356 is a Draft Standard with a status of elective. The substantive change to the IP encapsulation over X.25 is an increase in the IP datagram MTU size, the X.25 maximum data packet size, the virtual circuit management, and the interoperable encapsulation over X.25 of protocols other than IP between multi-protocol routers and bridges. One or more X.25 virtual circuits are opened on demand when datagram arrive at the network interface for transmission. Protocol Data Units (PDUs) are sent as X.25 complete packet sequences. That is, PDUs begin on X.25 data packet boundaries and the M bit (more data) is used to fragment PDUs that are larger than one X.25 data packet in length. In the IP encapsulation, the PDU is the IP DATAGRAM. The first octet in the Call User Data (CUD) field (the first data octet in the call Request packet) is used for protocol de-multiplexing in accordance with Subsequent Protocol Identifier (SPI) in ISO/IEC TR 9577.
- 4. Que. 3 What are congestion? Mention two algorithms to overcome congestion? Ans. TCP is the popular transport protocol for best-effort traffic in Internet. However, TCP is not well-suited for many applications such as streaming multimedia, because TCP congestion control algorithms introduce large variations in the congestion window size (and corresponding large variations in the sending rate). Such variability in the sending rate is not acceptable to many multimedia applications. Hence, many multimedia applications are built over UDP and use no congestion control at all. The absence of congestion control in applications built over UDP may lead to congestion collapse on the Internet. In addition, the UDP flows may starve any competing TCP flows. To overcome these adverse effects, congestion control needs to be incorporated into all applications using the Internet, whether at the transport layer or provided by the application itself. Furthermore, the congestion control algorithms must be TCP-friendly, i.e. the TCP-friendly flows should not gain more throughput than competing TCP flows in the long run. Thus, in recent years, many researchers have focused on developing “TCP-friendly” transport protocols which are suitable for many applications that currently use UDP. The first step in answering these questions is to study the short-term and long-term behavior of these algorithms. Although the goal of all TCP-friendly algorithms is to emulate the behavior of TCP in the long term, these algorithms may have an adverse impact in the short-term on competing TCP flows. Since TCP-friendly algorithms are designed for smoother sending rates than TCP, these algorithms may react slowly to new connections that share a common bottleneck link. Such a slower response may have a deleterious effect on TCP flows. For example, a TCP connection suffering losses in its slow start phase may enter the congestion avoidance phase with a small window, and consequently obtain lesser throughput than other competing flows. In this paper, we analyze the reasons for this unfairness, and validate the analysis by simulations. The rest of the paper is organized as follows. In Section II, we briefly overview the various TCP-friendly congestion control algorithms proposed in literature. In Section III, we define the transient behaviors studied in this paper, and analyze the expected transient behaviors of the various TCP-friendly congestion control algorithms. Few algorithms to overcome congestion 1) Transient behaviors evaluated in the paper 2) Equation-Based Congestion Control Algorithm 3) General AIMD-Based Congestion Control Algorithms 4) Binomial Congestion Control Algorithm
- 5. Que. 4 Differentiate between permanent and transient host groups? Ans IP multicasting is defined as the transmission of an IP datagram to a "host group", a set of zero or more hosts identified by a single IP destination address. A multicast datagram is delivered to all members of its destination host group with the same "best-efforts" reliability as regular uncast IP datagram’s, i.e. the datagram is not guaranteed to arrive at all members of the destination group or in the same order relative to other datagram’s The membership of a host group is dynamic; that is, hosts may join and leave groups at any time. There is no restriction on the location or number of members in a host group, but membership in a group may be restricted to only those hosts possessing a private access key. A host may be a member of more than one group at a time. A host need not be a member of a group to send datagram’s to it. A host group may be permanent or transient. A permanent group has a well-known, administratively assigned IP address. It is the address, not the membership of the group that is permanent; at any time a permanent group may have any number of members, even zero. A transient group, on the other hand, is assigned an address dynamically when the group is created, at the request of a host. A transient group ceases to exist, and its address becomes eligible for reassignment, when its membership drops to zero. The creation of transient groups and the maintenance of group membership information is the responsibility of "multicast agents", entities that reside in internet gateways or other special-purpose hosts. There is at least one multicast agent directly attached to every IP network or sub network that supports IP multicasting. A host requests the creation of new groups, and joins or leaves existing groups, by exchanging messages with a neighboring agent. Multicast agents are also responsible for internetwork delivery of multicast IP datagram’s. When sending a multicast IP datagram, a host transmits it to a local network multicast address which identifies all neighboring members of the destination host group. If the group has members on other networks, a multicast agent becomes an additional recipient of the local multicast and relays the datagram to agents on each of those other networks, via the internet gateway system.
- 6. Que. 5 What is domain name resolution? Discuss the domain name resolution process? Ans Domain Name System: - DNS is a way to resolve meaningful and easy-to-remember names to IP addresses. Because millions of sites are connected to the Internet, maintaining one central list of the name to- IP-address relationships across the Internet is unrealistic. The DNS system was designed to coordinate and distribute the resolution load. The two major tasks that DNS provides are: - 1) IP address resolution to hosts on the Internet, for local hosts 2) IP address resolution to hosts on the local network, for other hosts on the Internet The domain name resolution process as under like: - 1) A user program issues a request such as the get host by name () system call (this particular call asks for the IP address of a host by passing the host name) or the get host name () system call (which asks for a host name of a host by passing the IP address). 2) The resolver formulates a query to the name server. (Full resolvers have a local name cache to consult first; stub revolvers do not. 3) The name server checks to see if the answer is in its local authoritative database or cache, and if so, returns it to the client. Otherwise, it queries other available name servers, starting down from the root of the DNS tree or as high up the tree as possible. 4) The user program is finally given a corresponding IP address (or host name, depending on the query) or an error if the query could not be answered. Normally, the program will not be given a list of all the name servers that have been consulted to process the query. Domain name resolution is a client/server process .The client function (called the resolver or name resolver) is transparent to the user and is called by an application to resolve symbolic high-level names into real IP addresses or vice versa. The name server (also called a domain name server) is the server application providing the translation between high- level machine names and the IP addresses. The query/reply messages can be transported by either UDP or TCP.
- 7. Que. 6 Differentiate between Simple Mail Transfer Protocol and Post Office Protocol? Ans Simple Mail Transfer Protocol: - SMTP is a core Internet protocol used to transfer e-mail messages between servers (first defined in RFC 821 in 1982) This contrasts with protocols such as POP3 and IMAP, which are used by messaging clients to retrieve e-mail. SMTP servers look at the destination address of a message and contact the target mail server directly. Of course, this means the Domain Name Service (DNS) has to be configured correctly otherwise mail could be handed to the wrong server - potentially a big problem because, unless you have encrypted your messages, your e-mail will be in plain text! SMTP was designed to be a reliable message delivery system. Reliable in this case means that a message handled by SMTP is intended to get to its destination or generate an error message accordingly. This is not the same as a guaranteed delivery service, it just does its best. To guarantee delivery requires all sorts of data exchanges that would add considerable communications overhead that would be pointless for everyday purposes. SMTP communications are transported by TCP to ensure reliable end-to-end transport. RFC 822 defines the format of SMTP messages. Post Office Protocol: - POP is short for Post Office Protocol, a protocol used to retrieve e-mail from a mail server. Most e-mail applications (sometimes called an e-mail client) use the POP protocol, although some can use the newer IMAP (Internet Message Access Protocol). There are two versions of POP. The first called POP and second became a standard in the mid-80 s and requires SMTP to send messages. The newer version, POP3, can be used with or without SMTP. Pop is short for point of presence, an access point to the Internet. ISPs have typically multiple POPs. A point of presence is a physical location, either part of the facilities of a telecommunications provider that the ISP rents or a separate location from the telecommunications provider that houses servers, routers, ATM switches and digital/analog call aggregators. Pop is short for Programmed Operator (POP), a pseudo-opcode in a virtual machine language executed by an interpretive program. The Programmed Operator instructions provide the ability to define an instruction set for efficient encoding by calling subprograms into primary memory. POP is short for picture-outside-picture POP is a feature found on some televisions that allows the user to divide the screen into two same-size pictures, enabling you to view a second program. Compare with picture-in-picture (PIP).
