Manage Risk By Protecting the Apps and Data Infographic
•
1 gefällt mir•2,399 views
In today's security landscape, protecting apps and data should be top of mind for businesses. Our experts share their best practices for ensuring the protection of sensitive company information.
Melden
Teilen
Melden
Teilen
Downloaden Sie, um offline zu lesen
Empfohlen
Empfohlen
Weitere ähnliche Inhalte
Was ist angesagt?
Was ist angesagt? (20)
Citrix & Canalys: Northern European Channel Partners in a State of Transforma...

Citrix & Canalys: Northern European Channel Partners in a State of Transforma...
Empowering agencies using Elastic as a Service inside Government

Empowering agencies using Elastic as a Service inside Government
ePlus Enabling a Total Healthcare IT Transformation to Deliver the Future of ...

ePlus Enabling a Total Healthcare IT Transformation to Deliver the Future of ...
NetScaler: One Device, Every Need Guiding Enterprise IT to New Heights

NetScaler: One Device, Every Need Guiding Enterprise IT to New Heights
Citrix Customer Story: Franciscan Missionaries of Our Lady Health System

Citrix Customer Story: Franciscan Missionaries of Our Lady Health System
From Brainstorm to Build: How leading law firm, Minter Ellison, built a highl...

From Brainstorm to Build: How leading law firm, Minter Ellison, built a highl...
Andere mochten auch
Andere mochten auch (20)
Compliance program requirements for the Volcker Rule of the Dodd-Frank Act

Compliance program requirements for the Volcker Rule of the Dodd-Frank Act
Intranet: un modelo para la transformación digital de la organización

Intranet: un modelo para la transformación digital de la organización
PSBJ - Accelerating Sales Without a Marketing Budget

PSBJ - Accelerating Sales Without a Marketing Budget
2015 South By Southwest Sports: #SXSports Insights

2015 South By Southwest Sports: #SXSports Insights
Share point 2013 for intranets and the digital workplace (1)

Share point 2013 for intranets and the digital workplace (1)
Wanderlust- Photo Contest 2016: Winners and Commended

Wanderlust- Photo Contest 2016: Winners and Commended
Presentación webinar “Los 12 mejores trucos de velocidad para WordPress”

Presentación webinar “Los 12 mejores trucos de velocidad para WordPress”
Ähnlich wie Manage Risk By Protecting the Apps and Data Infographic
Ähnlich wie Manage Risk By Protecting the Apps and Data Infographic (20)
Manage Risk by Protecting the Apps and Data That Drive Business Productivity

Manage Risk by Protecting the Apps and Data That Drive Business Productivity
10 Reasons to Strengthen Security with App & Desktop Virtualization

10 Reasons to Strengthen Security with App & Desktop Virtualization
Top Cloud Infrastructure Practices And Strategies For Maximum Security.pdf

Top Cloud Infrastructure Practices And Strategies For Maximum Security.pdf
Chapter 6 Security of Information and Cyber Security(FASS)

Chapter 6 Security of Information and Cyber Security(FASS)
Why Cloud Security Matters in Today's Business World

Why Cloud Security Matters in Today's Business World
ISACA New York Metro, Developing, Deploying and Managing a Risk-Adjusted Data...

ISACA New York Metro, Developing, Deploying and Managing a Risk-Adjusted Data...
Cloud Security - Types, Common Threats & Tips To Mitigate.pdf

Cloud Security - Types, Common Threats & Tips To Mitigate.pdf
Crucial Layers_ Exploring the Depth of Enterprise Cyber Security.pdf

Crucial Layers_ Exploring the Depth of Enterprise Cyber Security.pdf
Mehr von Citrix
Mehr von Citrix (20)
Maximize your Investment in Microsoft Office 365 with Citrix Workspace 

Maximize your Investment in Microsoft Office 365 with Citrix Workspace
Deploying Citrix XenApp & XenDesktop Service on Google Cloud Platform

Deploying Citrix XenApp & XenDesktop Service on Google Cloud Platform
Workforce Flexibility Can Drive Greater Engagement & Productivity

Workforce Flexibility Can Drive Greater Engagement & Productivity
Citrix Cloud Services: Total Economic Benefits Assessment Guide

Citrix Cloud Services: Total Economic Benefits Assessment Guide
Citrix Cloud Services: Total Economic Benefits Assessment Guide

Citrix Cloud Services: Total Economic Benefits Assessment Guide
Citrix Synergy 2017: Technology Keynote Sketch Notes

Citrix Synergy 2017: Technology Keynote Sketch Notes
Citrix Synergy 2017: Malcolm Gladwell Innovation Super Session Sketch Notes

Citrix Synergy 2017: Malcolm Gladwell Innovation Super Session Sketch Notes
Synergy 2017: Colin Powell Innovation Super Session Sketch Notes

Synergy 2017: Colin Powell Innovation Super Session Sketch Notes
Enterprise Case Study: Enabling a More Mobile Way of Working 

Enterprise Case Study: Enabling a More Mobile Way of Working
Comparing traditional workspaces to digital workspaces

Comparing traditional workspaces to digital workspaces
The Security Compliance Countdown: How to Get Ahead of the GDPR [Infographic]![The Security Compliance Countdown: How to Get Ahead of the GDPR [Infographic]](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![The Security Compliance Countdown: How to Get Ahead of the GDPR [Infographic]](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
The Security Compliance Countdown: How to Get Ahead of the GDPR [Infographic]
Transforming Business with Citrix: Customers Share Their Stories.

Transforming Business with Citrix: Customers Share Their Stories.
Unified Endpoint Management: Security & Productivity for the Mobile Enterprise

Unified Endpoint Management: Security & Productivity for the Mobile Enterprise
Digital or die? British boardrooms divided on digital transformation

Digital or die? British boardrooms divided on digital transformation
Kürzlich hochgeladen
Kürzlich hochgeladen (20)
Strategies for Landing an Oracle DBA Job as a Fresher

Strategies for Landing an Oracle DBA Job as a Fresher
Strategize a Smooth Tenant-to-tenant Migration and Copilot Takeoff

Strategize a Smooth Tenant-to-tenant Migration and Copilot Takeoff
Apidays New York 2024 - The Good, the Bad and the Governed by David O'Neill, ...

Apidays New York 2024 - The Good, the Bad and the Governed by David O'Neill, ...
Cloud Frontiers: A Deep Dive into Serverless Spatial Data and FME

Cloud Frontiers: A Deep Dive into Serverless Spatial Data and FME
Navigating the Deluge_ Dubai Floods and the Resilience of Dubai International...

Navigating the Deluge_ Dubai Floods and the Resilience of Dubai International...
Biography Of Angeliki Cooney | Senior Vice President Life Sciences | Albany, ...

Biography Of Angeliki Cooney | Senior Vice President Life Sciences | Albany, ...
DEV meet-up UiPath Document Understanding May 7 2024 Amsterdam

DEV meet-up UiPath Document Understanding May 7 2024 Amsterdam
Repurposing LNG terminals for Hydrogen Ammonia: Feasibility and Cost Saving

Repurposing LNG terminals for Hydrogen Ammonia: Feasibility and Cost Saving
Apidays New York 2024 - Accelerating FinTech Innovation by Vasa Krishnan, Fin...

Apidays New York 2024 - Accelerating FinTech Innovation by Vasa Krishnan, Fin...
Mcleodganj Call Girls 🥰 8617370543 Service Offer VIP Hot Model

Mcleodganj Call Girls 🥰 8617370543 Service Offer VIP Hot Model
Six Myths about Ontologies: The Basics of Formal Ontology

Six Myths about Ontologies: The Basics of Formal Ontology
"I see eyes in my soup": How Delivery Hero implemented the safety system for ...

"I see eyes in my soup": How Delivery Hero implemented the safety system for ...
How to Troubleshoot Apps for the Modern Connected Worker

How to Troubleshoot Apps for the Modern Connected Worker
Apidays New York 2024 - Scaling API-first by Ian Reasor and Radu Cotescu, Adobe

Apidays New York 2024 - Scaling API-first by Ian Reasor and Radu Cotescu, Adobe
Boost Fertility New Invention Ups Success Rates.pdf

Boost Fertility New Invention Ups Success Rates.pdf
AWS Community Day CPH - Three problems of Terraform

AWS Community Day CPH - Three problems of Terraform
Vector Search -An Introduction in Oracle Database 23ai.pptx

Vector Search -An Introduction in Oracle Database 23ai.pptx
Manage Risk By Protecting the Apps and Data Infographic
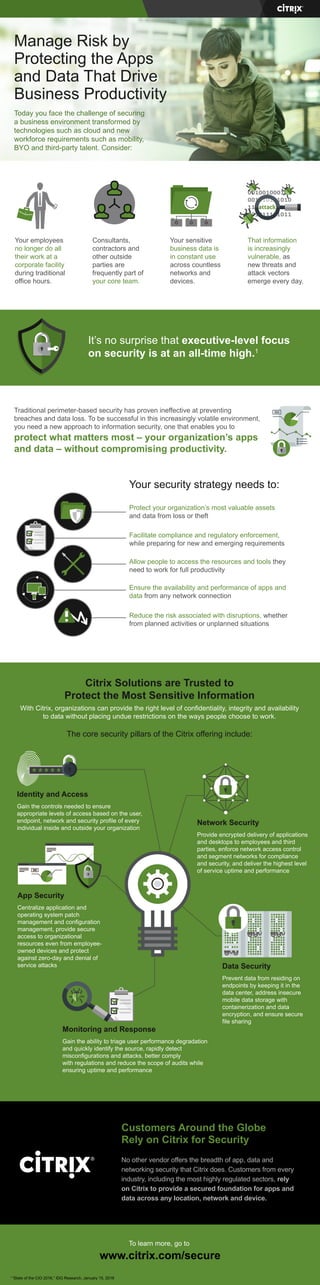
- 1. Manage Risk by Protecting the Apps and Data That Drive Business Productivity Today you face the challenge of securing a business environment transformed by technologies such as cloud and new workforce requirements such as mobility, BYO and third-party talent. Consider: Your employees no longer do all their work at a corporate facility during traditional office hours. Consultants, contractors and other outside parties are frequently part of your core team. Your sensitive business data is in constant use across countless networks and devices. That information is increasingly vulnerable, as new threats and attack vectors emerge every day. It’s no surprise that executive-level focus on security is at an all-time high.1 Traditional perimeter-based security has proven ineffective at preventing breaches and data loss. To be successful in this increasingly volatile environment, you need a new approach to information security, one that enables you to protect what matters most – your organization’s apps and data – without compromising productivity. Your security strategy needs to: Protect your organization’s most valuable assets and data from loss or theft Facilitate compliance and regulatory enforcement, while preparing for new and emerging requirements Allow people to access the resources and tools they need to work for full productivity Ensure the availability and performance of apps and data from any network connection Reduce the risk associated with disruptions, whether from planned activities or unplanned situations Citrix Solutions are Trusted to Protect the Most Sensitive Information With Citrix, organizations can provide the right level of confidentiality, integrity and availability to data without placing undue restrictions on the ways people choose to work. The core security pillars of the Citrix offering include: Identity and Access Gain the controls needed to ensure appropriate levels of access based on the user, endpoint, network and security profile of every individual inside and outside your organization Network Security Provide encrypted delivery of applications and desktops to employees and third parties, enforce network access control and segment networks for compliance and security, and deliver the highest level of service uptime and performance Data Security Prevent data from residing on endpoints by keeping it in the data center, address insecure mobile data storage with containerization and data encryption, and ensure secure file sharing Monitoring and Response Gain the ability to triage user performance degradation and quickly identify the source, rapidly detect misconfigurations and attacks, better comply with regulations and reduce the scope of audits while ensuring uptime and performance Customers Around the Globe Rely on Citrix for Security No other vendor offers the breadth of app, data and networking security that Citrix does. Customers from every industry, including the most highly regulated sectors, rely on Citrix to provide a secured foundation for apps and data across any location, network and device. To learn more, go to www.citrix.com/secure 1 “State of the CIO 2016,” IDG Research, January 15, 2016 App Security Centralize application and operating system patch management and configuration management, provide secure access to organizational resources even from employee- owned devices and protect against zero-day and denial of service attacks
