#BCMeeting2019: Rethinking Cybersecurity
•Als PPTX, PDF herunterladen•
0 gefällt mir•333 views
Presentation provided at the Annual ICC Banking Commission Meeting by Sukand Ramachandran on 11 April 2019.
Melden
Teilen
Melden
Teilen
Empfohlen
Empfohlen
Weitere ähnliche Inhalte
Was ist angesagt?
Was ist angesagt? (20)
Physical Security Information Management (PSIM) Solution for the Government

Physical Security Information Management (PSIM) Solution for the Government
Data Leak Protection Using Text Mining and Social Network Analysis

Data Leak Protection Using Text Mining and Social Network Analysis
Master Class Cyber Compliance IE Law School IE Busines School

Master Class Cyber Compliance IE Law School IE Busines School
Risk Management and Security in Strategic Planning

Risk Management and Security in Strategic Planning
Ähnlich wie #BCMeeting2019: Rethinking Cybersecurity
Ähnlich wie #BCMeeting2019: Rethinking Cybersecurity (20)
Practical Guide to Managing Incidents Using LLM's and NLP.pdf

Practical Guide to Managing Incidents Using LLM's and NLP.pdf
Legal and Ethical Implications of Cybersecurity.pptx

Legal and Ethical Implications of Cybersecurity.pptx
Healthcare info tech systems cyber threats ABI conference 2016

Healthcare info tech systems cyber threats ABI conference 2016
IT 552 Module Five Assignment Rubric The purpose of t.docx

IT 552 Module Five Assignment Rubric The purpose of t.docx
The 7 Steps to Prevent IT-Caused Outages- A Comprehensive Approach

The 7 Steps to Prevent IT-Caused Outages- A Comprehensive Approach
NIST CSF review - Essential Protections (a K12 perspective)

NIST CSF review - Essential Protections (a K12 perspective)
Cybersecurity Assessment Framework - Slideshare.pptx

Cybersecurity Assessment Framework - Slideshare.pptx
case studies on risk management in IT enabled organisation(vadodara)

case studies on risk management in IT enabled organisation(vadodara)
Project 4 Threat Analysis and ExploitationTranscript (backgroun.docx

Project 4 Threat Analysis and ExploitationTranscript (backgroun.docx
Ch08 8 Information Security Process it-slideshares.blogspot.com

Ch08 8 Information Security Process it-slideshares.blogspot.com
Satori Whitepaper: Threat Intelligence - a path to taming digital threats

Satori Whitepaper: Threat Intelligence - a path to taming digital threats
Forging Partnerships Between Auditors and Security Managers

Forging Partnerships Between Auditors and Security Managers
Reorganizing Federal IT to Address Today's Threats

Reorganizing Federal IT to Address Today's Threats
Mehr von International Chamber of Commerce - ICC
The latest update on ICC products and priorities for actionUpdate on Incoterms® 2020, ICC Marketplace, ICC Digital Library and chambers ...

Update on Incoterms® 2020, ICC Marketplace, ICC Digital Library and chambers ...International Chamber of Commerce - ICC
Report from the Regulatory Advocacy Working group on current objectives. Lead by Henri D’Ambrieres Reports from ICC BC Task Forces - Financial Crime Risk - Henri Dambrieres

Reports from ICC BC Task Forces - Financial Crime Risk - Henri DambrieresInternational Chamber of Commerce - ICC
Report from the Financial Crime Risk and Policy group on achievements to date and strategy for moving forward. Lead by Graham Baldock and Graham Finding.Reports from ICC BC Task Forces - Financial Crime Risk - Graham Baldock

Reports from ICC BC Task Forces - Financial Crime Risk - Graham BaldockInternational Chamber of Commerce - ICC
14h20 Presentation Controversy Guidance - Dave MeynellICC Banking Commission Technical Meeting 17/10/2018 - Outreach initiative 

ICC Banking Commission Technical Meeting 17/10/2018 - Outreach initiative International Chamber of Commerce - ICC
11h00 Presentation Sustainable Trade - Ruediger Geis ICC Banking Commission Technical Meeting 17/10/2018 - Outreach initiative 

ICC Banking Commission Technical Meeting 17/10/2018 - Outreach initiative International Chamber of Commerce - ICC
Annual discussion on the latest developments on trade finance, in Miami on 3-6 April.ICC BANKING COMMISSION MIAMI MEETING 2018: Day 2 @ 16:00 Sustainability and T...

ICC BANKING COMMISSION MIAMI MEETING 2018: Day 2 @ 16:00 Sustainability and T...International Chamber of Commerce - ICC
Mehr von International Chamber of Commerce - ICC (20)
Update on Incoterms® 2020, ICC Marketplace, ICC Digital Library and chambers ...

Update on Incoterms® 2020, ICC Marketplace, ICC Digital Library and chambers ...
Reports from ICC BC Task Forces - Financial Crime Risk - Henri Dambrieres

Reports from ICC BC Task Forces - Financial Crime Risk - Henri Dambrieres
Reports from ICC BC Task Forces - Financial Crime Risk - Graham Baldock

Reports from ICC BC Task Forces - Financial Crime Risk - Graham Baldock
Documentary Credit Practices: Controversy & Guidance

Documentary Credit Practices: Controversy & Guidance
ICC Banking Commission Technical Meeting 17/10/2018 - Outreach initiative 

ICC Banking Commission Technical Meeting 17/10/2018 - Outreach initiative
ICC Banking Commission Technical Meeting 17/10/2018 - Outreach initiative 

ICC Banking Commission Technical Meeting 17/10/2018 - Outreach initiative
ICC BANKING COMMISSION MIAMI MEETING 2018: Day 2 @ 16:00 Sustainability and T...

ICC BANKING COMMISSION MIAMI MEETING 2018: Day 2 @ 16:00 Sustainability and T...
Kürzlich hochgeladen
VIP Independent Call Girls in Taloja 🌹 9920725232 ( Call Me ) Mumbai Escorts * Ruhi Singh *
FOR BOOKING ★ A-Level (5-star Escort) (Akanksha): ☎️ +91-9920725232
AVAILABLE FOR COMPLETE ENJOYMENT WITH HIGH PROFILE INDIAN MODEL AVAILABLE HOTEL & HOME
Visit Our Site For More Pleasure in your City 👉 ☎️ +91-9920725232 👈
★ SAFE AND SECURE HIGH-CLASS SERVICE AFFORDABLE RATE
★
SATISFACTION, UNLIMITED ENJOYMENT.
★ All Meetings are confidential and no information is provided to any one at any cost.
★ EXCLUSIVE PROFILes Are Safe and Consensual with Most Limits Respected
★ Service Available In: - HOME & HOTEL Star Hotel Service. In Call & Out call
SeRvIcEs :
★ A-Level (star escort)
★ Strip-tease
★ BBBJ (Bareback Blowjob) Receive advanced sexual techniques in different mode make their life more pleasurable.
★ Spending time in hotel rooms
★ BJ (Blowjob Without a Condom)
★ Completion (Oral to completion)
★ Covered (Covered blowjob Without condom
★ANAL SERVICES.
Contact me
TELEPHONE
WHATSAPP
Looking for Enjoy all Day(Akanksha) : ☎️ +91-9920725232
Mumbai, Andheri, Navi Mumbai, Thane, Mumbai Airport, Mumbai Central, South Mumbai, Juhu, Bandra, Colaba, Nariman point, Malad, Powai, Mira Road, Dahisar, Mira Bhayandar, Worli, Santacruz, Vile Parle, Lower Parel, Chembur, Dadar, Ghatkopar, Kurla, Mulund, Goregaon, Kandivali, Borivali, Jogeshwari, Kalyan, Vashi , Nerul, Panvel, Dombivli, Lokhandwala, Four Bungalows, Versova, NRI Complex, Kharghar, Belapur, Taloja, Marine Drive, Hiranandani Gardens, Churchgate, Marine lines, Oshiwara, DN Nagar, Jb Nagar, Marol Naka, Saki Naka, Andheri East, Andheri West, Bandra West, Bandra East , Thane West, Ghodbundar Road,
There is a lot of talk about it in the media and news, so you might be wondering if this particular service is really worth the effort. A call girl service is exactly what it sounds like – a service where a woman offers sexual services over the phone. This type of service has been around for a long time and has become increasingly popular over the years. In most cases, call girl services are legal and regulated in many countries. There are a few things to keep in mind when considering the choice of whether to use a call girl service. First and foremost, make sure that you are comfortable with the particular person you are using the service from. Second, research accordingly before choosing a call girl. Don't just go with the first provider that comes up in your search; get opinions from others as well. Finally, be sure to have fun while using a call girl service; it's not just about sex. S040524N
★OUR BEST SERVICES: - FOR BOOKING ★ A-Level (5-star escort) ★ Strip-tease ★ BBBJ (Bareback Blowjob) ★ Spending time in my rooms ★ BJ (Blowjob Without a Condom) ★ COF (Come on Face) ★ Completion ★ (Oral to completion) noncovered ★ Special Massage ★ O-Level (Oral) ★ Blow Job; ★ Oral fun uncovered) ★ COB (Come on Body) ★. Extra ball (Have ride many times) ☛ ☛ ☛ ✔✔ secure✔✔ 100% safe WHATSAPP CALL ME +91-9920725232
VIP Independent Call Girls in Taloja 🌹 9920725232 ( Call Me ) Mumbai Escorts ...

VIP Independent Call Girls in Taloja 🌹 9920725232 ( Call Me ) Mumbai Escorts ...dipikadinghjn ( Why You Choose Us? ) Escorts
Model Call Girl Services in Delhi reach out to us at 🔝 9953056974 🔝✔️✔️
Our agency presents a selection of young, charming call girls available for bookings at Oyo Hotels. Experience high-class escort services at pocket-friendly rates, with our female escorts exuding both beauty and a delightful personality, ready to meet your desires. Whether it's Housewives, College girls, Russian girls, Muslim girls, or any other preference, we offer a diverse range of options to cater to your tastes.
We provide both in-call and out-call services for your convenience. Our in-call location in Delhi ensures cleanliness, hygiene, and 100% safety, while our out-call services offer doorstep delivery for added ease.
We value your time and money, hence we kindly request pic collectors, time-passers, and bargain hunters to refrain from contacting us.
Our services feature various packages at competitive rates:
One shot: ₹2000/in-call, ₹5000/out-call
Two shots with one girl: ₹3500/in-call, ₹6000/out-call
Body to body massage with sex: ₹3000/in-call
Full night for one person: ₹7000/in-call, ₹10000/out-call
Full night for more than 1 person: Contact us at 🔝 9953056974 🔝. for details
Operating 24/7, we serve various locations in Delhi, including Green Park, Lajpat Nagar, Saket, and Hauz Khas near metro stations.
For premium call girl services in Delhi 🔝 9953056974 🔝. Thank you for considering us!Call Girls in New Ashok Nagar, (delhi) call me [9953056974] escort service 24X7![Call Girls in New Ashok Nagar, (delhi) call me [9953056974] escort service 24X7](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![Call Girls in New Ashok Nagar, (delhi) call me [9953056974] escort service 24X7](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
Call Girls in New Ashok Nagar, (delhi) call me [9953056974] escort service 24X79953056974 Low Rate Call Girls In Saket, Delhi NCR
Model Call Girl Services in Delhi reach out to us at 🔝 9953056974 🔝✔️✔️
Our agency presents a selection of young, charming call girls available for bookings at Oyo Hotels. Experience high-class escort services at pocket-friendly rates, with our female escorts exuding both beauty and a delightful personality, ready to meet your desires. Whether it's Housewives, College girls, Russian girls, Muslim girls, or any other preference, we offer a diverse range of options to cater to your tastes.
We provide both in-call and out-call services for your convenience. Our in-call location in Delhi ensures cleanliness, hygiene, and 100% safety, while our out-call services offer doorstep delivery for added ease.
We value your time and money, hence we kindly request pic collectors, time-passers, and bargain hunters to refrain from contacting us.
Our services feature various packages at competitive rates:
One shot: ₹2000/in-call, ₹5000/out-call
Two shots with one girl: ₹3500/in-call, ₹6000/out-call
Body to body massage with sex: ₹3000/in-call
Full night for one person: ₹7000/in-call, ₹10000/out-call
Full night for more than 1 person: Contact us at 🔝 9953056974 🔝. for details
Operating 24/7, we serve various locations in Delhi, including Green Park, Lajpat Nagar, Saket, and Hauz Khas near metro stations.
For premium call girl services in Delhi 🔝 9953056974 🔝. Thank you for considering us!call girls in Sant Nagar (DELHI) 🔝 >༒9953056974 🔝 genuine Escort Service 🔝✔️✔️

call girls in Sant Nagar (DELHI) 🔝 >༒9953056974 🔝 genuine Escort Service 🔝✔️✔️9953056974 Low Rate Call Girls In Saket, Delhi NCR
VIP Independent Call Girls in Mira Bhayandar 🌹 9920725232 ( Call Me ) Mumbai Escorts * Ruhi Singh *
FOR BOOKING ★ A-Level (5-star Escort) (Akanksha): ☎️ +91-9920725232
AVAILABLE FOR COMPLETE ENJOYMENT WITH HIGH PROFILE INDIAN MODEL AVAILABLE HOTEL & HOME
Visit Our Site For More Pleasure in your City 👉 ☎️ +91-9920725232 👈
★ SAFE AND SECURE HIGH-CLASS SERVICE AFFORDABLE RATE
★
SATISFACTION, UNLIMITED ENJOYMENT.
★ All Meetings are confidential and no information is provided to any one at any cost.
★ EXCLUSIVE PROFILes Are Safe and Consensual with Most Limits Respected
★ Service Available In: - HOME & HOTEL Star Hotel Service. In Call & Out call
SeRvIcEs :
★ A-Level (star escort)
★ Strip-tease
★ BBBJ (Bareback Blowjob) Receive advanced sexual techniques in different mode make their life more pleasurable.
★ Spending time in hotel rooms
★ BJ (Blowjob Without a Condom)
★ Completion (Oral to completion)
★ Covered (Covered blowjob Without condom
★ANAL SERVICES.
Contact me
TELEPHONE
WHATSAPP
Looking for Enjoy all Day(Akanksha) : ☎️ +91-9920725232
Mumbai, Andheri, Navi Mumbai, Thane, Mumbai Airport, Mumbai Central, South Mumbai, Juhu, Bandra, Colaba, Nariman point, Malad, Powai, Mira Road, Dahisar, Mira Bhayandar, Worli, Santacruz, Vile Parle, Lower Parel, Chembur, Dadar, Ghatkopar, Kurla, Mulund, Goregaon, Kandivali, Borivali, Jogeshwari, Kalyan, Vashi , Nerul, Panvel, Dombivli, Lokhandwala, Four Bungalows, Versova, NRI Complex, Kharghar, Belapur, Taloja, Marine Drive, Hiranandani Gardens, Churchgate, Marine lines, Oshiwara, DN Nagar, Jb Nagar, Marol Naka, Saki Naka, Andheri East, Andheri West, Bandra West, Bandra East , Thane West, Ghodbundar Road,
There is a lot of talk about it in the media and news, so you might be wondering if this particular service is really worth the effort. A call girl service is exactly what it sounds like – a service where a woman offers sexual services over the phone. This type of service has been around for a long time and has become increasingly popular over the years. In most cases, call girl services are legal and regulated in many countries. There are a few things to keep in mind when considering the choice of whether to use a call girl service. First and foremost, make sure that you are comfortable with the particular person you are using the service from. Second, research accordingly before choosing a call girl. Don't just go with the first provider that comes up in your search; get opinions from others as well. Finally, be sure to have fun while using a call girl service; it's not just about sex. S040524N
★OUR BEST SERVICES: - FOR BOOKING ★ A-Level (5-star escort) ★ Strip-tease ★ BBBJ (Bareback Blowjob) ★ Spending time in my rooms ★ BJ (Blowjob Without a Condom) ★ COF (Come on Face) ★ Completion ★ (Oral to completion) noncovered ★ Special Massage ★ O-Level (Oral) ★ Blow Job; ★ Oral fun uncovered) ★ COB (Come on Body) ★. Extra ball (Have ride many times) ☛ ☛ ☛ ✔✔ secure✔✔ 100% safe WHATSAPP CALL ME +91-992072VIP Independent Call Girls in Mira Bhayandar 🌹 9920725232 ( Call Me ) Mumbai ...

VIP Independent Call Girls in Mira Bhayandar 🌹 9920725232 ( Call Me ) Mumbai ...dipikadinghjn ( Why You Choose Us? ) Escorts
VIP Kalyan Call Girls 🌐 9920725232 🌐 Make Your Dreams Come True With Mumbai Escorts
Looking for Enjoy all Day(Akanksha) : ☎️ +91-9920725232
Today call girl service available 24X7*▬█⓿▀█▀ 𝐈𝐍𝐃𝐄𝐏𝐄𝐍𝐃𝐄𝐍𝐓 CALL 𝐆𝐈𝐑𝐋 𝐕𝐈𝐏 𝐄𝐒𝐂𝐎𝐑𝐓 SERVICE ✅
⭐➡️HOT & SEXY MODELS // COLLEGE GIRLS
AVAILABLE FOR COMPLETE ENJOYMENT WITH HIGH PROFILE INDIAN MODEL AVAILABLE HOTEL & HOME
★ SAFE AND SECURE HIGH CLASS SERVICE AFFORDABLE RATE
★ 100% SATISFACTION,UNLIMITED ENJOYMENT.
★ All Meetings are confidential and no information is provided to any one at any cost.
★ EXCLUSIVE PROFILes Are Safe and Consensual with Most Limits Respected
★ Service Available In: - HOME & HOTEL 24x7 :: #S07 3 * 5 *7 *Star Hotel Service .In Call & Out call SeRvIcEs :
★ A-Level (5 star escort)
★ Strip-tease
★ BBBJ (Bareback Blowjob)Receive advanced sexual techniques in different mode make their life more pleasurable.
★ Spending time in hotel rooms
★ BJ (Blowjob Without a Condom)
★ Completion (Oral to completion)
★ Covered (Covered blowjob Without condom
100% SAFE AND SECURE 24 HOURS SERVICE AVAILABLE HOME AND HOTEL SERVICES
Visit Our Site For More Pleasure in your City 👉 ☎️ +91-9920725232 👈VIP Kalyan Call Girls 🌐 9920725232 🌐 Make Your Dreams Come True With Mumbai E...

VIP Kalyan Call Girls 🌐 9920725232 🌐 Make Your Dreams Come True With Mumbai E...roshnidevijkn ( Why You Choose Us? ) Escorts
Call Girls Service Pune ₹7.5k Pick Up & Drop With Cash Payment 9352852248 Call Girls
Booking Now open +91- 9352852248
Why you Choose Us- +91- 9352852248
HOT⇄ 8005736733
Mr ashu ji
Call Mr ashu Ji +91- 9352852248
𝐇𝐨𝐭𝐞𝐥 𝐑𝐨𝐨𝐦𝐬 𝐈𝐧𝐜𝐥𝐮𝐝𝐢𝐧𝐠 𝐑𝐚𝐭𝐞 𝐒𝐡𝐨𝐭𝐬/𝐇𝐨𝐮𝐫𝐲🆓 .█▬█⓿▀█▀ 𝐈𝐍𝐃𝐄𝐏𝐄𝐍𝐃𝐄𝐍𝐓 𝐆𝐈𝐑𝐋 𝐕𝐈𝐏 𝐄𝐒𝐂𝐎𝐑𝐓
Hello Guys ! High Profiles young Beauties and Good Looking standard Profiles Available , Enquire Now if you are interested in Hifi Service and want to get connect with someone who can understand your needs.
Service offers you the most beautiful High Profile sexy independent female Escorts in genuine ✔✔✔ To enjoy with hot and sexy girls ✔✔✔$s07
★providing:-
• Models
• vip Models
• Russian Models
• Foreigner Models
• TV Actress and Celebrities
• Receptionist
• Air Hostess
• Call Center Working Girls/Women
• Hi-Tech Co. Girls/Women
• HousewifeCall Girls Service Pune ₹7.5k Pick Up & Drop With Cash Payment 9352852248 Cal...

Call Girls Service Pune ₹7.5k Pick Up & Drop With Cash Payment 9352852248 Cal...roshnidevijkn ( Why You Choose Us? ) Escorts
VIP Independent Call Girls in Bandra West 🌹 9920725232 ( Call Me ) Mumbai Escorts * Ruhi Singh *
FOR BOOKING ★ A-Level (5-star Escort) (Akanksha): ☎️ +91-9920725232
AVAILABLE FOR COMPLETE ENJOYMENT WITH HIGH PROFILE INDIAN MODEL AVAILABLE HOTEL & HOME
Visit Our Site For More Pleasure in your City 👉 ☎️ +91-9920725232 👈
★ SAFE AND SECURE HIGH-CLASS SERVICE AFFORDABLE RATE
★
SATISFACTION, UNLIMITED ENJOYMENT.
★ All Meetings are confidential and no information is provided to any one at any cost.
★ EXCLUSIVE PROFILes Are Safe and Consensual with Most Limits Respected
★ Service Available In: - HOME & HOTEL Star Hotel Service. In Call & Out call
SeRvIcEs :
★ A-Level (star escort)
★ Strip-tease
★ BBBJ (Bareback Blowjob) Receive advanced sexual techniques in different mode make their life more pleasurable.
★ Spending time in hotel rooms
★ BJ (Blowjob Without a Condom)
★ Completion (Oral to completion)
★ Covered (Covered blowjob Without condom
★ANAL SERVICES.
Contact me
TELEPHONE
WHATSAPP
Looking for Enjoy all Day(Akanksha) : ☎️ +91-9920725232
Mumbai, Andheri, Navi Mumbai, Thane, Mumbai Airport, Mumbai Central, South Mumbai, Juhu, Bandra, Colaba, Nariman point, Malad, Powai, Mira Road, Dahisar, Mira Bhayandar, Worli, Santacruz, Vile Parle, Lower Parel, Chembur, Dadar, Ghatkopar, Kurla, Mulund, Goregaon, Kandivali, Borivali, Jogeshwari, Kalyan, Vashi , Nerul, Panvel, Dombivli, Lokhandwala, Four Bungalows, Versova, NRI Complex, Kharghar, Belapur, Taloja, Marine Drive, Hiranandani Gardens, Churchgate, Marine lines, Oshiwara, DN Nagar, Jb Nagar, Marol Naka, Saki Naka, Andheri East, Andheri West, Bandra West, Bandra East , Thane West, Ghodbundar Road,
There is a lot of talk about it in the media and news, so you might be wondering if this particular service is really worth the effort. A call girl service is exactly what it sounds like – a service where a woman offers sexual services over the phone. This type of service has been around for a long time and has become increasingly popular over the years. In most cases, call girl services are legal and regulated in many countries. There are a few things to keep in mind when considering the choice of whether to use a call girl service. First and foremost, make sure that you are comfortable with the particular person you are using the service from. Second, research accordingly before choosing a call girl. Don't just go with the first provider that comes up in your search; get opinions from others as well. Finally, be sure to have fun while using a call girl service; it's not just about sex. S040524N
★OUR BEST SERVICES: - FOR BOOKING ★ A-Level (5-star escort) ★ Strip-tease ★ BBBJ (Bareback Blowjob) ★ Spending time in my rooms ★ BJ (Blowjob Without a Condom) ★ COF (Come on Face) ★ Completion ★ (Oral to completion) noncovered ★ Special Massage ★ O-Level (Oral) ★ Blow Job; ★ Oral fun uncovered) ★ COB (Come on Body) ★. Extra ball (Have ride many times) ☛ ☛ ☛ ✔✔ secure✔✔ 100% safe WHATSAPP CALL ME +91-992072523VIP Independent Call Girls in Bandra West 🌹 9920725232 ( Call Me ) Mumbai Esc...

VIP Independent Call Girls in Bandra West 🌹 9920725232 ( Call Me ) Mumbai Esc...dipikadinghjn ( Why You Choose Us? ) Escorts
Kürzlich hochgeladen (20)
VIP Independent Call Girls in Taloja 🌹 9920725232 ( Call Me ) Mumbai Escorts ...

VIP Independent Call Girls in Taloja 🌹 9920725232 ( Call Me ) Mumbai Escorts ...
Mira Road Memorable Call Grls Number-9833754194-Bhayandar Speciallty Call Gir...

Mira Road Memorable Call Grls Number-9833754194-Bhayandar Speciallty Call Gir...
Call Girls in New Ashok Nagar, (delhi) call me [9953056974] escort service 24X7![Call Girls in New Ashok Nagar, (delhi) call me [9953056974] escort service 24X7](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![Call Girls in New Ashok Nagar, (delhi) call me [9953056974] escort service 24X7](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
Call Girls in New Ashok Nagar, (delhi) call me [9953056974] escort service 24X7
Navi Mumbai Cooperetive Housewife Call Girls-9833754194-Natural Panvel Enjoye...

Navi Mumbai Cooperetive Housewife Call Girls-9833754194-Natural Panvel Enjoye...
Diva-Thane European Call Girls Number-9833754194-Diva Busty Professional Call...

Diva-Thane European Call Girls Number-9833754194-Diva Busty Professional Call...
call girls in Sant Nagar (DELHI) 🔝 >༒9953056974 🔝 genuine Escort Service 🔝✔️✔️

call girls in Sant Nagar (DELHI) 🔝 >༒9953056974 🔝 genuine Escort Service 🔝✔️✔️
VIP Independent Call Girls in Mira Bhayandar 🌹 9920725232 ( Call Me ) Mumbai ...

VIP Independent Call Girls in Mira Bhayandar 🌹 9920725232 ( Call Me ) Mumbai ...
Vip Call US 📞 7738631006 ✅Call Girls In Sakinaka ( Mumbai )

Vip Call US 📞 7738631006 ✅Call Girls In Sakinaka ( Mumbai )
VIP Kalyan Call Girls 🌐 9920725232 🌐 Make Your Dreams Come True With Mumbai E...

VIP Kalyan Call Girls 🌐 9920725232 🌐 Make Your Dreams Come True With Mumbai E...
Best VIP Call Girls Morni Hills Just Click Me 6367492432

Best VIP Call Girls Morni Hills Just Click Me 6367492432
Vasai-Virar Fantastic Call Girls-9833754194-Call Girls MUmbai

Vasai-Virar Fantastic Call Girls-9833754194-Call Girls MUmbai
Kopar Khairane Russian Call Girls Number-9833754194-Navi Mumbai Fantastic Unl...

Kopar Khairane Russian Call Girls Number-9833754194-Navi Mumbai Fantastic Unl...
Call Girls Banaswadi Just Call 👗 7737669865 👗 Top Class Call Girl Service Ban...

Call Girls Banaswadi Just Call 👗 7737669865 👗 Top Class Call Girl Service Ban...
Call Girls Service Pune ₹7.5k Pick Up & Drop With Cash Payment 9352852248 Cal...

Call Girls Service Pune ₹7.5k Pick Up & Drop With Cash Payment 9352852248 Cal...
VIP Independent Call Girls in Bandra West 🌹 9920725232 ( Call Me ) Mumbai Esc...

VIP Independent Call Girls in Bandra West 🌹 9920725232 ( Call Me ) Mumbai Esc...
Strategic Resources May 2024 Corporate Presentation

Strategic Resources May 2024 Corporate Presentation
#BCMeeting2019: Rethinking Cybersecurity
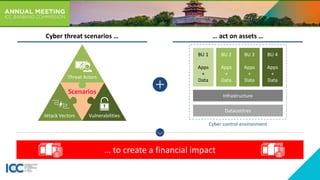
- 1. Scenarios Threat Actors Attack Vectors Vulnerabilities Cyber threat scenarios … … act on assets … … to create a financial impact Datacentres Infrastructure BU 1 Apps + Data BU 2 Apps + Data BU 3 Apps + Data BU 4 Apps + Data Cyber control environment
- 2. NIST is an industry standard framework for categorising Cyber controls Governance Outlines key governance processes that must be in place to manage cybersecurity environments, centered around strategy, policy and audit Identify Assists in developing controls required to identify where a cybersecurity event may take place, and understand the risk to systems, people, assets, data, and capabilities Protect Outlines appropriate safeguards to ensure delivery of critical infrastructure services, and supports the ability to limit or contain the impact of a potential cybersecurity event Detect Defines the appropriate activities to identify the occurrence of a cybersecurity event, driving to timely discovery of cybersecurity events Respond Includes appropriate activities to take action regarding a detected cybersecurity incident, including how to contain the impact of a potential cybersecurity incident. Recover Identifies appropriate activities to maintain plans for resilience and to restore any capabilities or services that were impaired due to a cybersecurity incident Explains how to manage and minimise supply chain and third party dependency risks that organisations have less control over Supply chain/dep. management
- 3. Estimating the impact of cybersecurity events … … enables clear communication of impact/mitigations Taking a methodology we're comfortable with … Expected Loss = Likelihood of Default x Impact given Default Likelihood of success x Financial Impact = Exposure ThreatIntensity (ThreatActors+AttackVectors) Vulnerability (as a function of controls) …and applying it to different types of cyber risk Allows estimation of loss impacts on assets … … and how to reduce impact through cyber mitigations
- 4. Call To Action! We need alignment on taxonomy … ...and to use similar methodologies
