Vanson Bourne Infographic: Big Data
•
1 gefällt mir•404 views
We're moving into an era of big data, where more information is captured in ever-finer detail from ever-more sources which means our decision-making is bound to improve. Doesn’t it? We interviewed 100 ITDMs from organisations with 1000 or more employees to find out.
Melden
Teilen
Melden
Teilen
Downloaden Sie, um offline zu lesen
Empfohlen
Empfohlen
Sharing the blame: How companies are collaborating on data security breaches

Sharing the blame: How companies are collaborating on data security breachesThe Economist Media Businesses
Weitere ähnliche Inhalte
Was ist angesagt?
Was ist angesagt? (20)
HIMSS Analytics® - 17 Technologies Shaping Hospital Purchases in 2016

HIMSS Analytics® - 17 Technologies Shaping Hospital Purchases in 2016
IDC Government Insights - Open Government Initiative Survey

IDC Government Insights - Open Government Initiative Survey
AI in Quality Control: How to do visual inspection with AI

AI in Quality Control: How to do visual inspection with AI
SVB Cybersecurity Impact on Innovation Report - Overview

SVB Cybersecurity Impact on Innovation Report - Overview
Data Management - a top Priority for Healthcare Practices

Data Management - a top Priority for Healthcare Practices
Data Collaboration in Healthcare -- presented at VLDB 2018

Data Collaboration in Healthcare -- presented at VLDB 2018
Infographic: Third-Party Risks: The cyber dimension

Infographic: Third-Party Risks: The cyber dimension
Ähnlich wie Vanson Bourne Infographic: Big Data
Sharing the blame: How companies are collaborating on data security breaches

Sharing the blame: How companies are collaborating on data security breachesThe Economist Media Businesses
Ähnlich wie Vanson Bourne Infographic: Big Data (20)
Sharing the blame: How companies are collaborating on data security breaches

Sharing the blame: How companies are collaborating on data security breaches
The hype and the hope: The road to big data adoption in Asia-Pacific

The hype and the hope: The road to big data adoption in Asia-Pacific
Data Modernization: Breaking the AI Vicious Cycle for Superior Decision-making

Data Modernization: Breaking the AI Vicious Cycle for Superior Decision-making
Ibm's global ai adoption index 2021 executive summary

Ibm's global ai adoption index 2021 executive summary
Lead Your Data Revolution - How to Build a Foundation of Trust and Data Gover...

Lead Your Data Revolution - How to Build a Foundation of Trust and Data Gover...
Envisioning IC ITE: The Next Generation of Information Sharing

Envisioning IC ITE: The Next Generation of Information Sharing
Finding their way: Corporates, governments and data privacy in Asia

Finding their way: Corporates, governments and data privacy in Asia
Making the Leap: Exploring the Push for Cloud Adoption

Making the Leap: Exploring the Push for Cloud Adoption
Intralinks Ponemon Research Report | Breaking Bad: The Risk of Unsecure File...

Intralinks Ponemon Research Report | Breaking Bad: The Risk of Unsecure File...
Mehr von Vanson Bourne
Mehr von Vanson Bourne (20)
Vanson Bourne Data Summary: Shadow IT - IT Decision-Makers

Vanson Bourne Data Summary: Shadow IT - IT Decision-Makers
Vanson Bourne Full Research Report: Directions in Tech Marketing

Vanson Bourne Full Research Report: Directions in Tech Marketing
Vanson Bourne Infographic: Social Media 2010 v 2013

Vanson Bourne Infographic: Social Media 2010 v 2013
Kürzlich hochgeladen
Kürzlich hochgeladen (20)
Raspberry Pi 5: Challenges and Solutions in Bringing up an OpenGL/Vulkan Driv...

Raspberry Pi 5: Challenges and Solutions in Bringing up an OpenGL/Vulkan Driv...
The 7 Things I Know About Cyber Security After 25 Years | April 2024

The 7 Things I Know About Cyber Security After 25 Years | April 2024
Breaking the Kubernetes Kill Chain: Host Path Mount

Breaking the Kubernetes Kill Chain: Host Path Mount
[2024]Digital Global Overview Report 2024 Meltwater.pdf![[2024]Digital Global Overview Report 2024 Meltwater.pdf](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![[2024]Digital Global Overview Report 2024 Meltwater.pdf](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
[2024]Digital Global Overview Report 2024 Meltwater.pdf
The Role of Taxonomy and Ontology in Semantic Layers - Heather Hedden.pdf

The Role of Taxonomy and Ontology in Semantic Layers - Heather Hedden.pdf
TrustArc Webinar - Stay Ahead of US State Data Privacy Law Developments

TrustArc Webinar - Stay Ahead of US State Data Privacy Law Developments
Kalyanpur ) Call Girls in Lucknow Finest Escorts Service 🍸 8923113531 🎰 Avail...

Kalyanpur ) Call Girls in Lucknow Finest Escorts Service 🍸 8923113531 🎰 Avail...
Exploring the Future Potential of AI-Enabled Smartphone Processors

Exploring the Future Potential of AI-Enabled Smartphone Processors
Automating Google Workspace (GWS) & more with Apps Script

Automating Google Workspace (GWS) & more with Apps Script
Unblocking The Main Thread Solving ANRs and Frozen Frames

Unblocking The Main Thread Solving ANRs and Frozen Frames
08448380779 Call Girls In Greater Kailash - I Women Seeking Men

08448380779 Call Girls In Greater Kailash - I Women Seeking Men
How to Troubleshoot Apps for the Modern Connected Worker

How to Troubleshoot Apps for the Modern Connected Worker
Strategies for Unlocking Knowledge Management in Microsoft 365 in the Copilot...

Strategies for Unlocking Knowledge Management in Microsoft 365 in the Copilot...
Vanson Bourne Infographic: Big Data
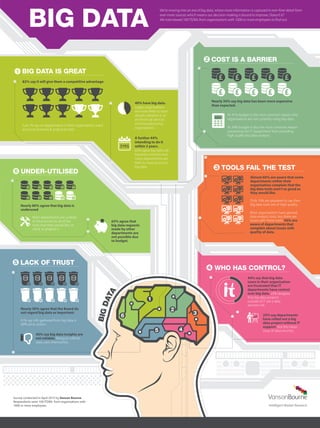
- 1. 36% say big data insights are not reliable. Rising to 53% for data users themselves. Survey conducted in April 2015 by Vanson Bourne. Respondents were 100 ITDMs from organisations with 1000 or more employees. BIG DATA IS GREAT BIG DATA COST IS A BARRIER UNDER-UTILISED LACK OF TRUST WHO HAS CONTROL? TOOLS FAIL THE TEST 1 2 1 6 5 2 4 3 6 5 4 3 40% have big data. Larger organisations are more likely to have already adopted it, as are financial services and manufacturing organisations. 82% say it will give them a competitive advantage Just 1% say no departments in their organisations want access to business & analytical tools. Nearly 80% agree that big data is underused. 44% say that big data users in their organisation are frustrated that IT departments have control over big data. 23% disagree that big data projects outside of IT are a data security risk. Nearly 50% say big data has been more expensive than expected. Almost 60% are aware that some departments within their organisation complain that the big data tools aren’t as good as they would like. Only 16% are prepared to say their big data tools are of high quality. Nearly 50% agree that the Board do not regard big data as important. 61% say info gathered from big data is difficult to action. We're moving into an era of big data, where more information is captured in ever-finer detail from ever-more sources which means our decision-making is bound to improve. Doesn’t it? We interviewed 100 ITDMs from organisations with 1000 or more employees to find out. At 41% budget is the most common reason why organisations are not currently using big data. At 34% budget is also the most common reason preventing the IT department from providing high quality big data analysis. 33% say departments have rolled out a big data project without IT support, but this raises issue of data security. Most departments are unlikely to have access to all of the tools that they would like, or need, to analyse it. 65% agree that big data requests made by other departments are not possible due to budget. Most organisations have general data analysis tools, but there are issues with these tools. 45% are aware of departments that complain about issues with quality of data. A further 44% intending to do it within 3 years. 82% agree big data will become common and many departments are keen to have access to big data.
