Software Security
•Als PPTX, PDF herunterladen•
0 gefällt mir•296 views
Seven Touch Points
Melden
Teilen
Melden
Teilen
Empfohlen
Empfohlen
Weitere ähnliche Inhalte
Was ist angesagt?
Was ist angesagt? (20)
Introduction to Software Security and Best Practices

Introduction to Software Security and Best Practices
"CERT Secure Coding Standards" by Dr. Mark Sherman

"CERT Secure Coding Standards" by Dr. Mark Sherman
Ethical Hacking n VAPT presentation by Suvrat jain

Ethical Hacking n VAPT presentation by Suvrat jain
certified-ethical-hacker-cehv12_course_content.pdf

certified-ethical-hacker-cehv12_course_content.pdf
Ähnlich wie Software Security
Ähnlich wie Software Security (20)
Application Security Testing for Software Engineers: An approach to build sof...

Application Security Testing for Software Engineers: An approach to build sof...
Enumerating software security design flaws throughout the ssdlc cosac - 201...

Enumerating software security design flaws throughout the ssdlc cosac - 201...
Enumerating software security design flaws throughout the SSDLC

Enumerating software security design flaws throughout the SSDLC
DevSecCon Asia 2017 Pishu Mahtani: Adversarial Modelling

DevSecCon Asia 2017 Pishu Mahtani: Adversarial Modelling
4_25655_SE731_2020_1__2_1_Lecture 1 - Course Outline and Secure SDLC.ppt

4_25655_SE731_2020_1__2_1_Lecture 1 - Course Outline and Secure SDLC.ppt
black-box testing is a type of software testing in which the tester is not co...

black-box testing is a type of software testing in which the tester is not co...
Manoj Purandare - Application Security - Secure Code Assessment Program - Pre...

Manoj Purandare - Application Security - Secure Code Assessment Program - Pre...
Manoj Purandare - Application Security - Secure Code Assessment Program - Pre...

Manoj Purandare - Application Security - Secure Code Assessment Program - Pre...
Manoj Purandare - Application Security - Secure Code Assessment Program - Pre...

Manoj Purandare - Application Security - Secure Code Assessment Program - Pre...
Mehr von Integral university, India
Mehr von Integral university, India (17)
Kürzlich hochgeladen
💉💊+971581248768>> SAFE AND ORIGINAL ABORTION PILLS FOR SALE IN DUBAI AND ABUDHABI}}+971581248768
+971581248768 Mtp-Kit (500MG) Prices » Dubai [(+971581248768**)] Abortion Pills For Sale In Dubai, UAE, Mifepristone and Misoprostol Tablets Available In Dubai, UAE CONTACT DR.Maya Whatsapp +971581248768 We Have Abortion Pills / Cytotec Tablets /Mifegest Kit Available in Dubai, Sharjah, Abudhabi, Ajman, Alain, Fujairah, Ras Al Khaimah, Umm Al Quwain, UAE, Buy cytotec in Dubai +971581248768''''Abortion Pills near me DUBAI | ABU DHABI|UAE. Price of Misoprostol, Cytotec” +971581248768' Dr.DEEM ''BUY ABORTION PILLS MIFEGEST KIT, MISOPROTONE, CYTOTEC PILLS IN DUBAI, ABU DHABI,UAE'' Contact me now via What's App…… abortion Pills Cytotec also available Oman Qatar Doha Saudi Arabia Bahrain Above all, Cytotec Abortion Pills are Available In Dubai / UAE, you will be very happy to do abortion in Dubai we are providing cytotec 200mg abortion pill in Dubai, UAE. Medication abortion offers an alternative to Surgical Abortion for women in the early weeks of pregnancy. We only offer abortion pills from 1 week-6 Months. We then advise you to use surgery if its beyond 6 months. Our Abu Dhabi, Ajman, Al Ain, Dubai, Fujairah, Ras Al Khaimah (RAK), Sharjah, Umm Al Quwain (UAQ) United Arab Emirates Abortion Clinic provides the safest and most advanced techniques for providing non-surgical, medical and surgical abortion methods for early through late second trimester, including the Abortion By Pill Procedure (RU 486, Mifeprex, Mifepristone, early options French Abortion Pill), Tamoxifen, Methotrexate and Cytotec (Misoprostol). The Abu Dhabi, United Arab Emirates Abortion Clinic performs Same Day Abortion Procedure using medications that are taken on the first day of the office visit and will cause the abortion to occur generally within 4 to 6 hours (as early as 30 minutes) for patients who are 3 to 12 weeks pregnant. When Mifepristone and Misoprostol are used, 50% of patients complete in 4 to 6 hours; 75% to 80% in 12 hours; and 90% in 24 hours. We use a regimen that allows for completion without the need for surgery 99% of the time. All advanced second trimester and late term pregnancies at our Tampa clinic (17 to 24 weeks or greater) can be completed within 24 hours or less 99% of the time without the need surgery. The procedure is completed with minimal to no complications. Our Women's Health Center located in Abu Dhabi, United Arab Emirates, uses the latest medications for medical abortions (RU-486, Mifeprex, Mifegyne, Mifepristone, early options French abortion pill), Methotrexate and Cytotec (Misoprostol). The safety standards of our Abu Dhabi, United Arab Emirates Abortion Doctors remain unparalleled. They consistently maintain the lowest complication rates throughout the nation. Our Physicians and staff are always available to answer questions and care for women in one of the most difficult times in their lives. The decision to have an abortion at the Abortion Cl+971581248768>> SAFE AND ORIGINAL ABORTION PILLS FOR SALE IN DUBAI AND ABUDHA...

+971581248768>> SAFE AND ORIGINAL ABORTION PILLS FOR SALE IN DUBAI AND ABUDHA...?#DUbAI#??##{{(☎️+971_581248768%)**%*]'#abortion pills for sale in dubai@
Kürzlich hochgeladen (20)
Modular Monolith - a Practical Alternative to Microservices @ Devoxx UK 2024

Modular Monolith - a Practical Alternative to Microservices @ Devoxx UK 2024
Spring Boot vs Quarkus the ultimate battle - DevoxxUK

Spring Boot vs Quarkus the ultimate battle - DevoxxUK
Strategies for Landing an Oracle DBA Job as a Fresher

Strategies for Landing an Oracle DBA Job as a Fresher
DEV meet-up UiPath Document Understanding May 7 2024 Amsterdam

DEV meet-up UiPath Document Understanding May 7 2024 Amsterdam
"I see eyes in my soup": How Delivery Hero implemented the safety system for ...

"I see eyes in my soup": How Delivery Hero implemented the safety system for ...
Vector Search -An Introduction in Oracle Database 23ai.pptx

Vector Search -An Introduction in Oracle Database 23ai.pptx
Six Myths about Ontologies: The Basics of Formal Ontology

Six Myths about Ontologies: The Basics of Formal Ontology
Apidays New York 2024 - Scaling API-first by Ian Reasor and Radu Cotescu, Adobe

Apidays New York 2024 - Scaling API-first by Ian Reasor and Radu Cotescu, Adobe
Web Form Automation for Bonterra Impact Management (fka Social Solutions Apri...

Web Form Automation for Bonterra Impact Management (fka Social Solutions Apri...
Cloud Frontiers: A Deep Dive into Serverless Spatial Data and FME

Cloud Frontiers: A Deep Dive into Serverless Spatial Data and FME
ICT role in 21st century education and its challenges

ICT role in 21st century education and its challenges
Apidays New York 2024 - APIs in 2030: The Risk of Technological Sleepwalk by ...

Apidays New York 2024 - APIs in 2030: The Risk of Technological Sleepwalk by ...
+971581248768>> SAFE AND ORIGINAL ABORTION PILLS FOR SALE IN DUBAI AND ABUDHA...

+971581248768>> SAFE AND ORIGINAL ABORTION PILLS FOR SALE IN DUBAI AND ABUDHA...
TrustArc Webinar - Unlock the Power of AI-Driven Data Discovery

TrustArc Webinar - Unlock the Power of AI-Driven Data Discovery
Software Security
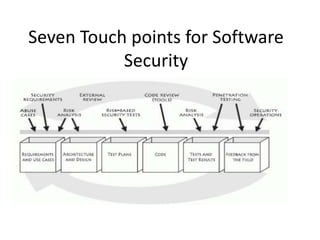
- 1. Seven Touch points for Software Security
- 2. • The touch points are one of the three pillars of software security • You don't have to adopt all seven touchpoints to begin to build security in (though doing so is highly recommended).
- 3. • The figure above shows the seven touchpoints ordered according to effectiveness and importance • The touchpoints are designed to fill the gap between the state of the art and the state of the practice-something that can be done only through the common adoption of best practices
- 4. • Touchpoints are a mix of destructive and constructive activities. • Destructive activities are about attacks, exploits, and breaking software. • These kinds of things are represented by the black hat (offense).
- 5. • Constructive activities are about design, defense, and functionality. • These are represented by the white hat (defense). • Both hats are necessary.
- 6. • Here are the touchpoints, in order of effectiveness: • 1. Code review • 2. Architectural risk analysis • 3. Penetration testing • 4. Risk-based security tests • 5. Abuse cases • 6. Security requirements • 7. Security operations
- 7. • 1. Code Review (Tools) Artifact: Code Example of risks found: Buffer overflow on line 42 • All software projects produce at least one artifactcode. • This fact moves code review to the number one slot on our list. • At the code level, the focus is on implementation bugs, especially those that static analysis tools that scan source code for common vulnerabilities can discover. • Several tools vendors now address this space. • Code review is a necessary but not sufficient practice for achieving secure software. • Security bugs (especially in C and C++) are a real problem, but architectural flaws are just as big a problem. • you'll learn how to review code with static analysis tools in next upcoming units
- 8. • Doing code review alone is an extremely useful activity, but given that this kind of review can only identify bugs, the best a code review can uncover is around 50% of the security problems. • Architectural problems are very difficult (and mostly impossible) to find by staring at code. • This is especially true for modern systems made of hundreds of thousands of lines of code. • A comprehensive approach to software security involves holistically combining both code review and architectural analysis.
- 9. • 2. Architectural Risk Analysis Artifact: Design and specification • Examples of risks found: Poor compartmentalization and protection of critical data; failure of a Web Service to authenticate calling code and its user and to make access control decisions based on proper context • At the design and architecture level, a system must be coherent and present a unified security front
- 10. • Designers, architects, and analysts should clearly document assumptions and identify possible attacks. • At both the specifications-based architecture stage and at the class-hierarchy design stage, architectural risk analysis is a necessity. • At this point, security analysts uncover and rank architectural flaws so that mitigation can begin. • Disregarding risk analysis at this level will lead to costly problems down the road.
- 11. • Note that risks crop up during all stages of the software lifecycle, so a constant risk management thread, with recurring risk- tracking and monitoring activities, is highly recommended. • Chapter 2 describes the RMF process and how to apply it. Chapter 5 teaches about architectural risk analysis and will help you ferret out flaws in software architecture.
- 12. Penetration Testing Artifact: System in its environment Example of risks found: Poor handling of program state in Web interface • Penetration testing is extremely useful, especially if an architectural risk analysis informs the tests. • The advantage of penetration testing is that it gives a good understanding of fielded software in its real environment. • Software that fails during the kind of canned black box testing practiced by prefab application security testing tools is truly bad. Thus, passing a low-octane penetration test reveals little about your actual security posture, but failing a canned penetration test indicates that you're in very deep trouble indeed.
- 13. • thank you
- 14. Risk-Based Security Testing • Artifact: Units and system • Example of risks found: Extent of data leakage possible by leveraging data protection risk • Security testing must encompass two strategies: • (1) testing of security functionality with standard functional testing techniques and • (2) risk-based security testing based on attack patterns, risk analysis results, and abuse cases. • A good security test plan embraces both strategies.
- 15. • Security problems aren't always apparent, even when you probe a system directly, so standard-issue quality assurance is unlikely to uncover all critical security issues. • QA is about making sure good things happen. Security testing is about making sure bad things don't happen. • Thinking like an attacker is essential. • Guiding security testing with knowledge of software architecture, common attacks, and the attacker's mindset is thus extremely important.
- 16. Security Operations Artifact: Fielded system • Example of risks found: Insufficient logging to prosecute a known attacker • Software security can benefit greatly from network security. • Well-integrated security operations allow and encourage network security professionals to get involved in applying the touchpoints, providing experience and security wisdom that might otherwise be missing from the development team.
- 17. • Battle-scarred operations people carefully set up and monitor fielded systems during use to enhance the security posture. • Attacks do happen, regardless of the strength of design and implementation, so understanding software behavior that leads to successful attack is an essential defensive technique. • Knowledge gained by understanding attacks and exploits should be cycled back into software development.
- 18. Abuse Cases Artifact: Requirements and use cases • Example of risks found: Susceptibility to well-known tampering attack • Building abuse cases is a great way to get into the mind of the attacker. • Similar to use cases, abuse cases describe the system's behavior under attack • Building abuse cases requires explicit coverage of what should be protected, from whom, and for how long.
- 19. Security Requirements Artifact: Requirements • Example of risks found: No explicit description of data protection needs • Security must be explicitly worked into the requirements level. • Good security requirements cover both overt functional security (say, the use of applied cryptography)
- 20. • emergent characteristics (best captured by abuse cases and attack patterns). • The art of identifying and maintaining security requirements is a complex undertaking that deserves broad treatment.
