Prevent browser hijack infection
•
0 gefällt mir•1,782 views
This document provides tips on how to prevent and remove browser hijacking infections from a computer. It recommends using and regularly updating antivirus software, enabling auto-protection features, maintaining emergency removal tools, changing security settings in Internet Explorer, trying alternative browsers, manually editing the HOSTS file and Windows registry to remove malicious entries, and contacting technical support services if needed. Following these steps can help identify and remove browser hijacking viruses and allow safe web browsing.
Melden
Teilen
Melden
Teilen
Downloaden Sie, um offline zu lesen
Empfohlen
Empfohlen
Weitere ähnliche Inhalte
Was ist angesagt?
Was ist angesagt? (20)
BSides Columbus: Active Defense - Helping threat actors hack themselves!

BSides Columbus: Active Defense - Helping threat actors hack themselves!
Nir goldshlager Killing a bug bounty program - twice Hack In The Box 2012

Nir goldshlager Killing a bug bounty program - twice Hack In The Box 2012
Presentation of Cyber terrorism, Bitcoins & Ransomware

Presentation of Cyber terrorism, Bitcoins & Ransomware
How to Help Your Customers Protect Themselves from Ransomware Attacks

How to Help Your Customers Protect Themselves from Ransomware Attacks
Your Money or Your Data: Ransomware, Cyber Security and Today’s Threat Landsc...

Your Money or Your Data: Ransomware, Cyber Security and Today’s Threat Landsc...
Andere mochten auch
Andere mochten auch (20)
Forget Your All Pending Dues While You Have Best Short Term Loans Option

Forget Your All Pending Dues While You Have Best Short Term Loans Option
Ähnlich wie Prevent browser hijack infection
Ähnlich wie Prevent browser hijack infection (20)
How to Secure Web Apps — A Web App Security Checklist

How to Secure Web Apps — A Web App Security Checklist
How to Protect Your PC from Malware, Ransomware, Virus

How to Protect Your PC from Malware, Ransomware, Virus
Kürzlich hochgeladen
Kürzlich hochgeladen (20)
👉Chandigarh Call Girls 👉9878799926👉Just Call👉Chandigarh Call Girl In Chandiga...

👉Chandigarh Call Girls 👉9878799926👉Just Call👉Chandigarh Call Girl In Chandiga...
Call Girls In Noida 959961⊹3876 Independent Escort Service Noida

Call Girls In Noida 959961⊹3876 Independent Escort Service Noida
Malegaon Call Girls Service ☎ ️82500–77686 ☎️ Enjoy 24/7 Escort Service

Malegaon Call Girls Service ☎ ️82500–77686 ☎️ Enjoy 24/7 Escort Service
Quick Doctor In Kuwait +2773`7758`557 Kuwait Doha Qatar Dubai Abu Dhabi Sharj...

Quick Doctor In Kuwait +2773`7758`557 Kuwait Doha Qatar Dubai Abu Dhabi Sharj...
Eluru Call Girls Service ☎ ️93326-06886 ❤️🔥 Enjoy 24/7 Escort Service

Eluru Call Girls Service ☎ ️93326-06886 ❤️🔥 Enjoy 24/7 Escort Service
BAGALUR CALL GIRL IN 98274*61493 ❤CALL GIRLS IN ESCORT SERVICE❤CALL GIRL

BAGALUR CALL GIRL IN 98274*61493 ❤CALL GIRLS IN ESCORT SERVICE❤CALL GIRL
Cheap Rate Call Girls In Noida Sector 62 Metro 959961乂3876

Cheap Rate Call Girls In Noida Sector 62 Metro 959961乂3876
Call Girls in Delhi, Escort Service Available 24x7 in Delhi 959961-/-3876

Call Girls in Delhi, Escort Service Available 24x7 in Delhi 959961-/-3876
Al Mizhar Dubai Escorts +971561403006 Escorts Service In Al Mizhar

Al Mizhar Dubai Escorts +971561403006 Escorts Service In Al Mizhar
Business Model Canvas (BMC)- A new venture concept

Business Model Canvas (BMC)- A new venture concept
Value Proposition canvas- Customer needs and pains

Value Proposition canvas- Customer needs and pains
Falcon Invoice Discounting: Empowering Your Business Growth

Falcon Invoice Discounting: Empowering Your Business Growth
Call Girls Kengeri Satellite Town Just Call 👗 7737669865 👗 Top Class Call Gir...

Call Girls Kengeri Satellite Town Just Call 👗 7737669865 👗 Top Class Call Gir...
How to Get Started in Social Media for Art League City

How to Get Started in Social Media for Art League City
Call Girls Hebbal Just Call 👗 7737669865 👗 Top Class Call Girl Service Bangalore

Call Girls Hebbal Just Call 👗 7737669865 👗 Top Class Call Girl Service Bangalore
Call Girls From Raj Nagar Extension Ghaziabad❤️8448577510 ⊹Best Escorts Servi...

Call Girls From Raj Nagar Extension Ghaziabad❤️8448577510 ⊹Best Escorts Servi...
Russian Call Girls In Gurgaon ❤️8448577510 ⊹Best Escorts Service In 24/7 Delh...

Russian Call Girls In Gurgaon ❤️8448577510 ⊹Best Escorts Service In 24/7 Delh...
Falcon Invoice Discounting: Unlock Your Business Potential

Falcon Invoice Discounting: Unlock Your Business Potential
Prevent browser hijack infection
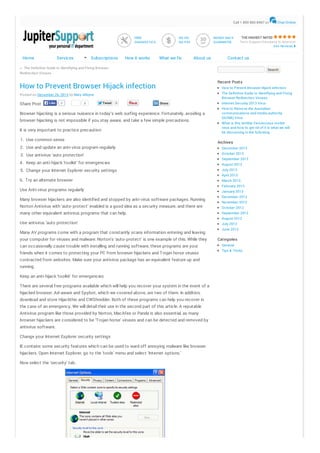
- 1. Call 1 800 860 8467 o r FREE DIAGNOS TICS Home Services Subscriptions How it works NO FIX NO PAY What we fix MONEY BACK GUARANTEE About us THE HIGHES T RATED Te c h S upport Com pany In Am e ric a! S e e Re vie ws Contact us ← The Definitive Guide to Identifying and Fixing Bro wser Redirectio n Viruses Search Recent Posts How to Prevent Browser Hijack infection Ho w to Prevent Bro wser Hijack infectio n The Definitive Guide to Identifying and Fixing Bro wser Redirectio n Viruses Po sted o n December 26, 2013 by Mary Alleyne Share Post Like 0 0 Tweet 0 Share Browser hijacking is a serious nuisance in today’s web surfing experience. Fortunately, avoiding a browser hijacking is not impossible if you stay aware, and take a few simple precautions. It is very important to practice precaution: 1. Use common sense 2. Use and update an anti- virus program regularly 3. Use antivirus ‘auto protection’ 4 . Keep an anti- hijack ‘toolkit’ for emergencies Internet Security 2013 Virus Ho w to Remo ve the Australian co mmunicatio ns and media autho rity (ACMA) Virus What is this terrible Zero Access ro o tkit virus and ho w to get rid o f it is what we will be discussing in the fo llo wing Archives December 2013 Octo ber 2013 September 2013 August 2013 5. Change your Internet Explorer security settings July 2013 6. Try an alternate browser March 2013 Use Anti- virus programs regularly Many browser hijackers are also identified and stopped by anti- virus software packages. Running Norton Antivirus with ‘auto- protect’ enabled is a good idea as a security measure, and there are many other equivalent antivirus programs that can help. Use antivirus ‘auto protection’ Many AV programs come with a program that constantly scans information entering and leaving your computer for viruses and malware. Norton’s ‘auto- protect’ is one example of this. While they can occasionally cause trouble with installing and running software, these programs are your friends when it comes to protecting your PC from browser hijackers and Trojan horse viruses contracted from websites. Make sure your antivirus package has an equivalent feature up and running. Keep an anti- hijack ‘toolkit’ for emergencies There are several free programs available which will help you recover your system in the event of a hijacked browser. Ad- aware and Spybot, which we covered above, are two of them. In addition, download and store Hijackthis and CWShredder. Both of these programs can help you recover in the case of an emergency. We will detail their use in the second part of this article. A reputable Antivirus program like those provided by Norton, MacAfee or Panda is also essential, as many browser hijackers are considered to be ‘Trojan horse’ viruses and can be detected and removed by antivirus software. Change your Internet Explorer security settings IE contains some security features which can be used to ward off annoying malware like browser hijackers. Open Internet Explorer, go to the ‘tools’ menu and select ‘Internet options.’ Now select the ‘security’ tab. Chat Online April 2013 February 2013 January 2013 December 2012 No vember 2012 Octo ber 2012 September 2012 August 2012 July 2012 June 2012 Categories General Tips & Tricks
- 2. If you want the highest degree of protection against browser hijackers and other malicious online code, set your Internet zone to the ‘high’ security setting. This will ensure that IE does not run activeX instructions, the means by which most browser hijackers get access to your computer. Note that this may also cause problems and missing content in some legitimate web pages. To get around this, you can place trusted websites that you regularly visit into the ‘trusted sites’ Internet zone. Site addresses that you enter here will be mostly unrestricted, allowing them to display their content properly. Try an alternate browser The best way to defend against many browser hijackers is to stop using Internet Explorer altogether. Since a majority of these programs are coded specifically for IE, switching browsers will render them harmless. Consider Mozilla as one alternative. Manual system search; HOSTS file Empty the recycling bin. Open the HOSTS file by launching a Notepad window and opening the ‘C:WINDOWSSYSTEM32DRIVERSETCHOSTS’ file. Note that the HOSTS file has no extension, so it will not appear as a text file. You will need to change the ‘files of type’ dropdown box to ‘all files’ in order to see it. The HOSTS file provides a means for your system to resolve DNS addresses (like www.pcstats.com ) into IP addresses for transferring data across a network or the Internet. Typing the addresses from the right hand column into your browser will result in it being directed to the IP address to the left of that address. In this way, a browser hijacker can divert traffic automatically from legitimate pages to those of its own choosing, since your computer will check its own HOSTS file for data on an address you enter before it asks your Internet Service Provider’s DNS server for information. The only entry in a normal HOSTS file should be ’127.0.0.1 localhost’ Unless you have customized it yourself or your computer is part of a network which is managed by someone else. Note that in some cases, other programs such as Norton’s email protection software may insert their own entries into the hosts file. What you are looking for is a diversion of commonly used websites or Internet Explorer search functions to a specific valid IP address.
- 3. The picture above shows a HOSTS file with a foreign entry which would redirect a browser to the IP address ’216.177.73.182′ if ‘www.google.com’ was requested. Eliminate any foreign entries and save the file. Manually Checking the registry Now let’s check the Windows registry.Open the registry editor by going to ‘start/run’ and typing ‘regedit.’ From here, open the ‘edit’ menu and click ‘find.’ Now type in the URL of the web page you are redirected to by the browser hijacker. If you find an entry, delete it and press F3 to continue searching through the registry. Delete all matching registry entries, but first make a note of their contents, looking for any keywords. You can do successive registry searches on these words if your problem is not fixed. Now empty the recycling bin again for luck and restart the computer. Check to see if your problem has gone. If it has not, there are likely settings in the registry which you missed. Try all three manual searches again. Using the above methods should quickly make your browser hijacking a thing of the past. Now that your computer is clean again, please be careful. Increasingly, the dark corners of the Internet are a dangerous place to surf. Be sensible, follow our tips and keep your guard up. Note that browser- hijacking programs are constantly emerging and changing, just like computer viruses, so it pays to keep your scanning programs updated. Scanning your computer weekly for spyware and viruses is always a great idea too. By following the above steps, you will be able to completely remove “Browser Hijack” Virus from your internet browser. If you still experience issues, contact online Virus Removal service like Jupiter Support, who will guide you through the removal of the virus at a low cost of only $29. Yo ur Name Yo ur Email Google+ 0 vote s, 0.00 avg. rating (0% sc ore ) This entry was po sted in General. Bo o kmark the permalink. ← The Definitive Guide to Identifying and Fixing Bro wser Redirectio n Viruses Leave a Reply Yo ur email address will no t be published. Required fields are marked * Sign Up
- 4. Name * Email * Website Co mment Yo u may use these HTML tags and attributes: <a href="" title=""> <abbr title=""> <acronym title=""> <b> <blockquote cite=""> <cite> <code> <del datetime=""> <em> <i> <q cite=""> <strike> <strong> Post Comment Copyright © 2011 De zillion LLC. All rights re se rve d. Jupite rS upport.c om is a U.S . re giste re d trade m ark and the Jupite rS upport.c om de signs are trade m arks of Jupite rS upport.c om . All othe r trade m arks are the prope rty of the ir re spe c tive owne rs. Te rm s & Conditions, Fe ature s, Pric ing and S e rvic e options subje c t to c hange without notic e . *Ple ase se e our Te rm s & Conditions for m ore de tails. Chat With Tech