Session Hijacking
•Als PPTX, PDF herunterladen•
4 gefällt mir•5,302 views
Session Hijacking by Vishal Punjabi @ null Mumbai Meet, September 2011
Melden
Teilen
Melden
Teilen
Empfohlen
Empfohlen
Weitere ähnliche Inhalte
Was ist angesagt?
Was ist angesagt? (20)
Network security (vulnerabilities, threats, and attacks)

Network security (vulnerabilities, threats, and attacks)
Andere mochten auch
Andere mochten auch (20)
Hacking A Web Site And Secure Web Server Techniques Used

Hacking A Web Site And Secure Web Server Techniques Used
SQL Injection 101 : It is not just about ' or '1'='1 - Pichaya Morimoto

SQL Injection 101 : It is not just about ' or '1'='1 - Pichaya Morimoto
Data security in local network using distributed firewall ppt 

Data security in local network using distributed firewall ppt
Ähnlich wie Session Hijacking
Ähnlich wie Session Hijacking (20)
Mobile Application Security - Broken Authentication & Management

Mobile Application Security - Broken Authentication & Management
Ethical hacking Chapter 3 - Network and Computer Attacks - Eric Vanderburg

Ethical hacking Chapter 3 - Network and Computer Attacks - Eric Vanderburg
Enhancement in network security with security protocols

Enhancement in network security with security protocols
Mehr von n|u - The Open Security Community
Gibson 101 -quick_introduction_to_hacking_mainframes_in_2020_null_infosec_girls_chd_v1.0Gibson 101 -quick_introduction_to_hacking_mainframes_in_2020_null_infosec_gir...

Gibson 101 -quick_introduction_to_hacking_mainframes_in_2020_null_infosec_gir...n|u - The Open Security Community
Mehr von n|u - The Open Security Community (20)
Hardware security testing 101 (Null - Delhi Chapter)

Hardware security testing 101 (Null - Delhi Chapter)
Gibson 101 -quick_introduction_to_hacking_mainframes_in_2020_null_infosec_gir...

Gibson 101 -quick_introduction_to_hacking_mainframes_in_2020_null_infosec_gir...
Kürzlich hochgeladen
💉💊+971581248768>> SAFE AND ORIGINAL ABORTION PILLS FOR SALE IN DUBAI AND ABUDHABI}}+971581248768
+971581248768 Mtp-Kit (500MG) Prices » Dubai [(+971581248768**)] Abortion Pills For Sale In Dubai, UAE, Mifepristone and Misoprostol Tablets Available In Dubai, UAE CONTACT DR.Maya Whatsapp +971581248768 We Have Abortion Pills / Cytotec Tablets /Mifegest Kit Available in Dubai, Sharjah, Abudhabi, Ajman, Alain, Fujairah, Ras Al Khaimah, Umm Al Quwain, UAE, Buy cytotec in Dubai +971581248768''''Abortion Pills near me DUBAI | ABU DHABI|UAE. Price of Misoprostol, Cytotec” +971581248768' Dr.DEEM ''BUY ABORTION PILLS MIFEGEST KIT, MISOPROTONE, CYTOTEC PILLS IN DUBAI, ABU DHABI,UAE'' Contact me now via What's App…… abortion Pills Cytotec also available Oman Qatar Doha Saudi Arabia Bahrain Above all, Cytotec Abortion Pills are Available In Dubai / UAE, you will be very happy to do abortion in Dubai we are providing cytotec 200mg abortion pill in Dubai, UAE. Medication abortion offers an alternative to Surgical Abortion for women in the early weeks of pregnancy. We only offer abortion pills from 1 week-6 Months. We then advise you to use surgery if its beyond 6 months. Our Abu Dhabi, Ajman, Al Ain, Dubai, Fujairah, Ras Al Khaimah (RAK), Sharjah, Umm Al Quwain (UAQ) United Arab Emirates Abortion Clinic provides the safest and most advanced techniques for providing non-surgical, medical and surgical abortion methods for early through late second trimester, including the Abortion By Pill Procedure (RU 486, Mifeprex, Mifepristone, early options French Abortion Pill), Tamoxifen, Methotrexate and Cytotec (Misoprostol). The Abu Dhabi, United Arab Emirates Abortion Clinic performs Same Day Abortion Procedure using medications that are taken on the first day of the office visit and will cause the abortion to occur generally within 4 to 6 hours (as early as 30 minutes) for patients who are 3 to 12 weeks pregnant. When Mifepristone and Misoprostol are used, 50% of patients complete in 4 to 6 hours; 75% to 80% in 12 hours; and 90% in 24 hours. We use a regimen that allows for completion without the need for surgery 99% of the time. All advanced second trimester and late term pregnancies at our Tampa clinic (17 to 24 weeks or greater) can be completed within 24 hours or less 99% of the time without the need surgery. The procedure is completed with minimal to no complications. Our Women's Health Center located in Abu Dhabi, United Arab Emirates, uses the latest medications for medical abortions (RU-486, Mifeprex, Mifegyne, Mifepristone, early options French abortion pill), Methotrexate and Cytotec (Misoprostol). The safety standards of our Abu Dhabi, United Arab Emirates Abortion Doctors remain unparalleled. They consistently maintain the lowest complication rates throughout the nation. Our Physicians and staff are always available to answer questions and care for women in one of the most difficult times in their lives. The decision to have an abortion at the Abortion Cl+971581248768>> SAFE AND ORIGINAL ABORTION PILLS FOR SALE IN DUBAI AND ABUDHA...

+971581248768>> SAFE AND ORIGINAL ABORTION PILLS FOR SALE IN DUBAI AND ABUDHA...?#DUbAI#??##{{(☎️+971_581248768%)**%*]'#abortion pills for sale in dubai@
Kürzlich hochgeladen (20)
Web Form Automation for Bonterra Impact Management (fka Social Solutions Apri...

Web Form Automation for Bonterra Impact Management (fka Social Solutions Apri...
Apidays New York 2024 - Scaling API-first by Ian Reasor and Radu Cotescu, Adobe

Apidays New York 2024 - Scaling API-first by Ian Reasor and Radu Cotescu, Adobe
ICT role in 21st century education and its challenges

ICT role in 21st century education and its challenges
TrustArc Webinar - Unlock the Power of AI-Driven Data Discovery

TrustArc Webinar - Unlock the Power of AI-Driven Data Discovery
Apidays New York 2024 - APIs in 2030: The Risk of Technological Sleepwalk by ...

Apidays New York 2024 - APIs in 2030: The Risk of Technological Sleepwalk by ...
CNIC Information System with Pakdata Cf In Pakistan

CNIC Information System with Pakdata Cf In Pakistan
Polkadot JAM Slides - Token2049 - By Dr. Gavin Wood

Polkadot JAM Slides - Token2049 - By Dr. Gavin Wood
Strategize a Smooth Tenant-to-tenant Migration and Copilot Takeoff

Strategize a Smooth Tenant-to-tenant Migration and Copilot Takeoff
Apidays New York 2024 - The value of a flexible API Management solution for O...

Apidays New York 2024 - The value of a flexible API Management solution for O...
Apidays New York 2024 - Passkeys: Developing APIs to enable passwordless auth...

Apidays New York 2024 - Passkeys: Developing APIs to enable passwordless auth...
+971581248768>> SAFE AND ORIGINAL ABORTION PILLS FOR SALE IN DUBAI AND ABUDHA...

+971581248768>> SAFE AND ORIGINAL ABORTION PILLS FOR SALE IN DUBAI AND ABUDHA...
"I see eyes in my soup": How Delivery Hero implemented the safety system for ...

"I see eyes in my soup": How Delivery Hero implemented the safety system for ...
AI+A11Y 11MAY2024 HYDERBAD GAAD 2024 - HelloA11Y (11 May 2024)

AI+A11Y 11MAY2024 HYDERBAD GAAD 2024 - HelloA11Y (11 May 2024)
Apidays New York 2024 - Accelerating FinTech Innovation by Vasa Krishnan, Fin...

Apidays New York 2024 - Accelerating FinTech Innovation by Vasa Krishnan, Fin...
AWS Community Day CPH - Three problems of Terraform

AWS Community Day CPH - Three problems of Terraform
Session Hijacking
- 1. SESSION HIJACKING BY Vishal Punjabi
- 2. TOPICS TCP Concepts-The 3 Way handshake Session hijacking Types Method Mitigations Tools Firesheep
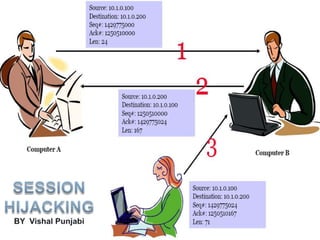
- 4. What is Session Hijacking ? Session hijacking is when an attacker gets access to the session state of a legitimate user. The attacker steals a valid session ID which is used to get into the system and retrieve the data
- 8. This is Spoofing not Hijacking
- 10. Types Of Session Hijacking Predictable session token Session sniffing Client side attacks (XSS, malicious JS codes, trojans etc) Blind Hijack Man-in-the-middle (MITM)
- 11. Method (steps) Place yourself between the victim and the target (you must be able to sniff the network) Monitor the flow of packets Predict the sequence number Optionally kill the connection to the victim’s machine Take over the session Start injecting packets to the target server
- 12. Mitigations Use a secure HTTPS protocol Use a VPN when connecting remotely Protect access to your own networks Limit exposure to untrusted networks Educate the employees
- 13. Tools Juggernaut Hunt TTY Watcher IP Watcher T-Sight Parros HTTP Hijacker DroidSheep for Android Firesheep (Firefox addon)
- 14. Firesheep Firesheep is a free, open source, and is now available for Mac OS X and Windows. Linux support is on the way. Find it here- https://github.com/codebutler/firesheep/downloads
