How an alarm monitoring system works
•Als PPTX, PDF herunterladen•
1 gefällt mir•416 views
Ever wonder what happens when an alarm monitoring system’s alarm goes off? What if it doesn’t deter the intruders when it’s supposed to? Who’s going to save the day?
Melden
Teilen
Melden
Teilen
Empfohlen
Empfohlen
Weitere ähnliche Inhalte
Kürzlich hochgeladen
Kürzlich hochgeladen (20)
1111 ChatGPT Prompts PDF Free Download - Prompts for ChatGPT

1111 ChatGPT Prompts PDF Free Download - Prompts for ChatGPT
The Value of Certifying Products for FDO _ Paul at FIDO Alliance.pdf

The Value of Certifying Products for FDO _ Paul at FIDO Alliance.pdf
Extensible Python: Robustness through Addition - PyCon 2024

Extensible Python: Robustness through Addition - PyCon 2024
Harnessing Passkeys in the Battle Against AI-Powered Cyber Threats.pptx

Harnessing Passkeys in the Battle Against AI-Powered Cyber Threats.pptx
TEST BANK For, Information Technology Project Management 9th Edition Kathy Sc...

TEST BANK For, Information Technology Project Management 9th Edition Kathy Sc...
Intro in Product Management - Коротко про професію продакт менеджера

Intro in Product Management - Коротко про професію продакт менеджера
Microsoft CSP Briefing Pre-Engagement - Questionnaire

Microsoft CSP Briefing Pre-Engagement - Questionnaire
Introduction to FDO and How It works Applications _ Richard at FIDO Alliance.pdf

Introduction to FDO and How It works Applications _ Richard at FIDO Alliance.pdf
FDO for Camera, Sensor and Networking Device – Commercial Solutions from VinC...

FDO for Camera, Sensor and Networking Device – Commercial Solutions from VinC...
Using IESVE for Room Loads Analysis - UK & Ireland

Using IESVE for Room Loads Analysis - UK & Ireland
State of the Smart Building Startup Landscape 2024!

State of the Smart Building Startup Landscape 2024!
(Explainable) Data-Centric AI: what are you explaininhg, and to whom?

(Explainable) Data-Centric AI: what are you explaininhg, and to whom?
Long journey of Ruby Standard library at RubyKaigi 2024

Long journey of Ruby Standard library at RubyKaigi 2024
Breaking Down the Flutterwave Scandal What You Need to Know.pdf

Breaking Down the Flutterwave Scandal What You Need to Know.pdf
Event-Driven Architecture Masterclass: Integrating Distributed Data Stores Ac...

Event-Driven Architecture Masterclass: Integrating Distributed Data Stores Ac...
Empfohlen
More than Just Lines on a Map: Best Practices for U.S Bike Routes
This session highlights best practices and lessons learned for U.S. Bike Route System designation, as well as how and why these routes should be integrated into bicycle planning at the local and regional level.
Presenters:
Presenter: Kevin Luecke Toole Design Group
Co-Presenter: Virginia Sullivan Adventure Cycling AssociationMore than Just Lines on a Map: Best Practices for U.S Bike Routes

More than Just Lines on a Map: Best Practices for U.S Bike RoutesProject for Public Spaces & National Center for Biking and Walking
Empfohlen (20)
AI Trends in Creative Operations 2024 by Artwork Flow.pdf

AI Trends in Creative Operations 2024 by Artwork Flow.pdf
Content Methodology: A Best Practices Report (Webinar)

Content Methodology: A Best Practices Report (Webinar)
How to Prepare For a Successful Job Search for 2024

How to Prepare For a Successful Job Search for 2024
Social Media Marketing Trends 2024 // The Global Indie Insights

Social Media Marketing Trends 2024 // The Global Indie Insights
Trends In Paid Search: Navigating The Digital Landscape In 2024

Trends In Paid Search: Navigating The Digital Landscape In 2024
5 Public speaking tips from TED - Visualized summary

5 Public speaking tips from TED - Visualized summary
Google's Just Not That Into You: Understanding Core Updates & Search Intent

Google's Just Not That Into You: Understanding Core Updates & Search Intent
The six step guide to practical project management

The six step guide to practical project management
Beginners Guide to TikTok for Search - Rachel Pearson - We are Tilt __ Bright...

Beginners Guide to TikTok for Search - Rachel Pearson - We are Tilt __ Bright...
Unlocking the Power of ChatGPT and AI in Testing - A Real-World Look, present...

Unlocking the Power of ChatGPT and AI in Testing - A Real-World Look, present...
More than Just Lines on a Map: Best Practices for U.S Bike Routes

More than Just Lines on a Map: Best Practices for U.S Bike Routes
How an alarm monitoring system works
- 1. How an Alarm Monitoring System Works and other Stuff You Need to Know
- 2. Ever wonder what happens when an alarm monitoring system’s alarm goes off? What if it doesn’t deter the intruders when it’s supposed to? Who’s going to save the day?
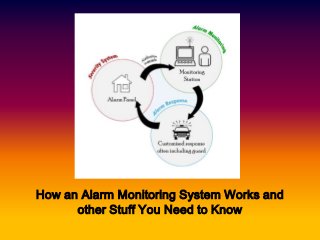
- 3. First, the alarm. • Setting up an alarm monitoring in Sydney has grown significantly in number in many homes and business. That’s because it has been proven effective in deterring burglars. An alarm system utilizes various ways to thwart unlawful entry. • When an electronic contact on doors or windows are tripped, it triggers the alarm to go off. In some more sophisticated devices, lasers are used as a triggering mechanism, much like those that you saw on several Mission Impossible movies. Others are triggered by movements that are detected by motion sensors.
- 4. Alerting the authorities • For a monthly fee, when the alarm monitoring system is triggered, it doesn’t only alarm loud enough to send the intruder panicking; it also sends an electronic transmission to a central monitoring station, which in turn sends an alert to the local police station in your area. • But what if it was just a false alarm? • A call will be sent to the owner’s home or office where the alarm went off to verify the situation. If the call is unanswered, or if the call is answered in distress, the police are notified immediately and dispatched to the area.
- 5. What happens to the alarm monitoring system when power is out? • Usually, a home or office alarm or security system is powered by an AC current. But when power goes out, the security system uses its own back-up power which only lasts for several hours. This is especially helpful for when the intruder decided to cut the power lines in your home. Once power is back, the security system reverts back to the AC current while recharging its own back-up power supply.
- 6. What if the alarm system was just accidently triggered? • There will be instances when the alarm has been accidentally triggered by anyone living in the home or working in the office. The central monitoring station will first place a call to check whether the alarm was legitimate. They will do proper identity check by asking for your secret password. No police will be dispatched to your property if the alarm was proven to be triggered accidentally.
- 7. Costs involved in setting up a monitored alarm • It goes without saying that monitored alarms cost significantly more than regular alarm security systems. That’s because the response and added security are more sophisticated. You get the peace of mind from tighter security measures and more sophisticated security devices. • Also, keep in mind that there could be added costs to the owner for excessive alarms. That’s why when deciding on alarm monitoring systems for your Sydney property, be sure to talk to your security system provider for anything related to costs so you won’t be blind-sided once the devices have been set-up within your property.
- 8. For more information on setting up an alarm monitoring system in your home or business, call 1300 133 343 or visit us today!