Melden
Teilen
Downloaden Sie, um offline zu lesen
Empfohlen
Empfohlen
Weitere ähnliche Inhalte
Was ist angesagt?
Was ist angesagt? (20)
3 reasons your business can't ignore Two-Factor Authentication

3 reasons your business can't ignore Two-Factor Authentication
A Complete Software Engineer With Hardware / Networking Skill's

A Complete Software Engineer With Hardware / Networking Skill's
AN ENHANCED SECURITY FOR GOVERNMENT BASE ON MULTIFACTOR BIOMETRIC AUTHENTICATION

AN ENHANCED SECURITY FOR GOVERNMENT BASE ON MULTIFACTOR BIOMETRIC AUTHENTICATION
Combat the Latest Two-Factor Authentication Evasion Techniques

Combat the Latest Two-Factor Authentication Evasion Techniques
Architecture and security - Gauthier Van Damme (IBBT-COSIC- K.U.Leuven) & Kri...

Architecture and security - Gauthier Van Damme (IBBT-COSIC- K.U.Leuven) & Kri...
Combat Passwords on Post-Its with Multi-Factor Authentication for IBM i

Combat Passwords on Post-Its with Multi-Factor Authentication for IBM i
Adding Two Factor Authentication to your App with Authy

Adding Two Factor Authentication to your App with Authy
Avoiding Two-factor Authentication? You're Not Alone

Avoiding Two-factor Authentication? You're Not Alone
Ähnlich wie Datasheet two factor-authenticationx
Ähnlich wie Datasheet two factor-authenticationx (20)
Multifactor authenticationMultifactor authentication or MFA .docx

Multifactor authenticationMultifactor authentication or MFA .docx
AN ENHANCED SECURITY FOR GOVERNMENT BASE ON MULTIFACTOR BIOMETRIC AUTHENTICATION

AN ENHANCED SECURITY FOR GOVERNMENT BASE ON MULTIFACTOR BIOMETRIC AUTHENTICATION
A secure communication in smart phones using two factor authentication

A secure communication in smart phones using two factor authentication
A secure communication in smart phones using two factor authentications

A secure communication in smart phones using two factor authentications
Narrative of digital signature technology and moving forward

Narrative of digital signature technology and moving forward
IRJET- Data Security with Multifactor Authentication

IRJET- Data Security with Multifactor Authentication
Mobile Devices & BYOD Security – Deployment & Best Practices

Mobile Devices & BYOD Security – Deployment & Best Practices
Mehr von Hai Nguyen
Mehr von Hai Nguyen (20)
Quest defender provides_secure__affordable_two-factor_authentication_for_okla...

Quest defender provides_secure__affordable_two-factor_authentication_for_okla...
Attachment 1 – mitigation measures for two factor authentication compromise

Attachment 1 – mitigation measures for two factor authentication compromise
Kürzlich hochgeladen
A Principled Technologies deployment guide
Conclusion
Deploying VMware Cloud Foundation 5.1 on next gen Dell PowerEdge servers brings together critical virtualization capabilities and high-performing hardware infrastructure. Relying on our hands-on experience, this deployment guide offers a comprehensive roadmap that can guide your organization through the seamless integration of advanced VMware cloud solutions with the performance and reliability of Dell PowerEdge servers. In addition to the deployment efficiency, the Cloud Foundation 5.1 and PowerEdge solution delivered strong performance while running a MySQL database workload. By leveraging VMware Cloud Foundation 5.1 and PowerEdge servers, you could help your organization embrace cloud computing with confidence, potentially unlocking a new level of agility, scalability, and efficiency in your data center operations.Deploy with confidence: VMware Cloud Foundation 5.1 on next gen Dell PowerEdg...

Deploy with confidence: VMware Cloud Foundation 5.1 on next gen Dell PowerEdg...Principled Technologies
💉💊+971581248768>> SAFE AND ORIGINAL ABORTION PILLS FOR SALE IN DUBAI AND ABUDHABI}}+971581248768
+971581248768 Mtp-Kit (500MG) Prices » Dubai [(+971581248768**)] Abortion Pills For Sale In Dubai, UAE, Mifepristone and Misoprostol Tablets Available In Dubai, UAE CONTACT DR.Maya Whatsapp +971581248768 We Have Abortion Pills / Cytotec Tablets /Mifegest Kit Available in Dubai, Sharjah, Abudhabi, Ajman, Alain, Fujairah, Ras Al Khaimah, Umm Al Quwain, UAE, Buy cytotec in Dubai +971581248768''''Abortion Pills near me DUBAI | ABU DHABI|UAE. Price of Misoprostol, Cytotec” +971581248768' Dr.DEEM ''BUY ABORTION PILLS MIFEGEST KIT, MISOPROTONE, CYTOTEC PILLS IN DUBAI, ABU DHABI,UAE'' Contact me now via What's App…… abortion Pills Cytotec also available Oman Qatar Doha Saudi Arabia Bahrain Above all, Cytotec Abortion Pills are Available In Dubai / UAE, you will be very happy to do abortion in Dubai we are providing cytotec 200mg abortion pill in Dubai, UAE. Medication abortion offers an alternative to Surgical Abortion for women in the early weeks of pregnancy. We only offer abortion pills from 1 week-6 Months. We then advise you to use surgery if its beyond 6 months. Our Abu Dhabi, Ajman, Al Ain, Dubai, Fujairah, Ras Al Khaimah (RAK), Sharjah, Umm Al Quwain (UAQ) United Arab Emirates Abortion Clinic provides the safest and most advanced techniques for providing non-surgical, medical and surgical abortion methods for early through late second trimester, including the Abortion By Pill Procedure (RU 486, Mifeprex, Mifepristone, early options French Abortion Pill), Tamoxifen, Methotrexate and Cytotec (Misoprostol). The Abu Dhabi, United Arab Emirates Abortion Clinic performs Same Day Abortion Procedure using medications that are taken on the first day of the office visit and will cause the abortion to occur generally within 4 to 6 hours (as early as 30 minutes) for patients who are 3 to 12 weeks pregnant. When Mifepristone and Misoprostol are used, 50% of patients complete in 4 to 6 hours; 75% to 80% in 12 hours; and 90% in 24 hours. We use a regimen that allows for completion without the need for surgery 99% of the time. All advanced second trimester and late term pregnancies at our Tampa clinic (17 to 24 weeks or greater) can be completed within 24 hours or less 99% of the time without the need surgery. The procedure is completed with minimal to no complications. Our Women's Health Center located in Abu Dhabi, United Arab Emirates, uses the latest medications for medical abortions (RU-486, Mifeprex, Mifegyne, Mifepristone, early options French abortion pill), Methotrexate and Cytotec (Misoprostol). The safety standards of our Abu Dhabi, United Arab Emirates Abortion Doctors remain unparalleled. They consistently maintain the lowest complication rates throughout the nation. Our Physicians and staff are always available to answer questions and care for women in one of the most difficult times in their lives. The decision to have an abortion at the Abortion Cl+971581248768>> SAFE AND ORIGINAL ABORTION PILLS FOR SALE IN DUBAI AND ABUDHA...

+971581248768>> SAFE AND ORIGINAL ABORTION PILLS FOR SALE IN DUBAI AND ABUDHA...?#DUbAI#??##{{(☎️+971_581248768%)**%*]'#abortion pills for sale in dubai@
Kürzlich hochgeladen (20)
Bajaj Allianz Life Insurance Company - Insurer Innovation Award 2024

Bajaj Allianz Life Insurance Company - Insurer Innovation Award 2024
Repurposing LNG terminals for Hydrogen Ammonia: Feasibility and Cost Saving

Repurposing LNG terminals for Hydrogen Ammonia: Feasibility and Cost Saving
Deploy with confidence: VMware Cloud Foundation 5.1 on next gen Dell PowerEdg...

Deploy with confidence: VMware Cloud Foundation 5.1 on next gen Dell PowerEdg...
The 7 Things I Know About Cyber Security After 25 Years | April 2024

The 7 Things I Know About Cyber Security After 25 Years | April 2024
AWS Community Day CPH - Three problems of Terraform

AWS Community Day CPH - Three problems of Terraform
Exploring the Future Potential of AI-Enabled Smartphone Processors

Exploring the Future Potential of AI-Enabled Smartphone Processors
Mastering MySQL Database Architecture: Deep Dive into MySQL Shell and MySQL R...

Mastering MySQL Database Architecture: Deep Dive into MySQL Shell and MySQL R...
ProductAnonymous-April2024-WinProductDiscovery-MelissaKlemke

ProductAnonymous-April2024-WinProductDiscovery-MelissaKlemke
How to Troubleshoot Apps for the Modern Connected Worker

How to Troubleshoot Apps for the Modern Connected Worker
Powerful Google developer tools for immediate impact! (2023-24 C)

Powerful Google developer tools for immediate impact! (2023-24 C)
Bajaj Allianz Life Insurance Company - Insurer Innovation Award 2024

Bajaj Allianz Life Insurance Company - Insurer Innovation Award 2024
Strategies for Unlocking Knowledge Management in Microsoft 365 in the Copilot...

Strategies for Unlocking Knowledge Management in Microsoft 365 in the Copilot...
HTML Injection Attacks: Impact and Mitigation Strategies

HTML Injection Attacks: Impact and Mitigation Strategies
Automating Google Workspace (GWS) & more with Apps Script

Automating Google Workspace (GWS) & more with Apps Script
+971581248768>> SAFE AND ORIGINAL ABORTION PILLS FOR SALE IN DUBAI AND ABUDHA...

+971581248768>> SAFE AND ORIGINAL ABORTION PILLS FOR SALE IN DUBAI AND ABUDHA...
Workshop - Best of Both Worlds_ Combine KG and Vector search for enhanced R...

Workshop - Best of Both Worlds_ Combine KG and Vector search for enhanced R...
Apidays New York 2024 - The Good, the Bad and the Governed by David O'Neill, ...

Apidays New York 2024 - The Good, the Bad and the Governed by David O'Neill, ...
Cloud Frontiers: A Deep Dive into Serverless Spatial Data and FME

Cloud Frontiers: A Deep Dive into Serverless Spatial Data and FME
Datasheet two factor-authenticationx
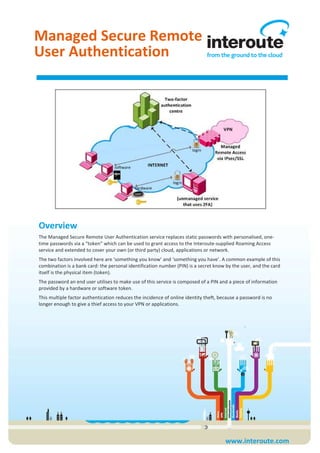
- 1. www.interoute.com Overview The Managed Secure Remote User Authentication service replaces static passwords with personalised, one- time passwords via a “token” which can be used to grant access to the Interoute-supplied Roaming Access service and extended to cover your own (or third party) cloud, applications or network. The two factors involved here are ‘something you know’ and ‘something you have’. A common example of this combination is a bank card: the personal identification number (PIN) is a secret know by the user, and the card itself is the physical item (token). The password an end user utilises to make use of this service is composed of a PIN and a piece of information provided by a hardware or software token. This multiple factor authentication reduces the incidence of online identity theft, because a password is no longer enough to give a thief access to your VPN or applications. Managed Secure Remote User Authentication
- 2. 2 www.interoute.com Technical Service Details Interoute, using carefully selected third parties, supplies and supports Two-Factor Authentication (also known as 2FA) as either as a complement for Roaming Access via IPsec or SSL as well as a standalone service for your own specific needs (for example, access to a web server, a cloud service, etc.) Once implemented, the customer (via a nominated administrator) assumes control of the management and provisioning of its token inventory using the 3 rd party’s web portal. The web portal allows the customer and their end users to perform basic operations with their tokens, such as token re-synchronisation and PIN change. When ordered as a standalone service, the customer is responsible of configuring their equipment to send authentication requests directly to the 2FA supplier’s infrastructure. Interoute can provide configuration documentation from the supplier as well as give support customers who require it. Interoute 2FA service is supported by hardware or software tokens: Hardware tokens (fob) A hardware token is similar to a key-fob, which shows the current one-time password. The token is synchronised with the authentication server and the password cycles regularly. Hardware tokens are tamper-resistant, tamper-evident and machine independent, allowing a user to logon from any location or machine. Software-based token A cryptography piece of software is installed on your computer or smart phone, which generates a one-time password anytime you have to present your login credentials. Software tokens can be massively deployed without hardware distribution. See the table under Customer Requirements for available platforms. Note: Interoute provides limited support for software-related troubleshooting (see Limitations).
- 3. 3 www.interoute.com Customer Requirements Once the tokens are shipped to a designated customer location – for hardware tokens – or made available to the customer via the 3 rd party portal for software tokens – it is the customer’s responsibility to enrol the end users. The software tokens can be used on the following platforms: Platform Operating System Windows PC (32/64 bit) XP, Vista, 7, 2003 Server, 2008 Server iPhone, iPad iOS 4.1 or later BlackBerry OS 4.5 or later Table 1: Platform and operating system availability for software tokens Supported Service Changes • For any existing service, you can order additional tokens (regardless of type) Reporting Token usage log and any authentication events are available via the 3 rd party web portal. Limitations Support scope for software tokens is limited to dealing with outages affecting the 2FA provider service; any problems resulting from non-network customer configuration or faults in computer and network operating systems (e.g. Windows, Blackberry, Apple iOS, etc.) or any third party software are not within scope. Billing The following Billing plan is available for Interoute’s Managed Secure Remote User Authentication Service: • An initial non-recurring charge for service setup and – if applicable – token purchase. • A monthly flat rate charge based on the number of tokens Product Codes Service Code Two-Factor Authentication SVC-TOKEN Related services The Managed Secure Remote User Authentication Service improves security of Roaming Access Service to VPN How to order Order through an Interoute Account Manager or via the HUB, Interoute’s online portal. More information For product enquiries, please consult the Security Services Product Manager.
