Common Cybersecurity Mistakes
•
0 gefällt mir•370 views
Common Cybersecurity Mistakes Businesses Continue To Make
Melden
Teilen
Melden
Teilen
Downloaden Sie, um offline zu lesen
Empfohlen
Empfohlen
Weitere ähnliche Inhalte
Was ist angesagt?
Was ist angesagt? (19)
Containing the outbreak: The healthcare security pandemic

Containing the outbreak: The healthcare security pandemic
What is CryptoLocker and How Can I Protect My Business From It?

What is CryptoLocker and How Can I Protect My Business From It?
Video surveillance: Why should my business use it?

Video surveillance: Why should my business use it?
INFOGRAPHIC▶ Spear Phishing Scammers Sharpen Their Attacks

INFOGRAPHIC▶ Spear Phishing Scammers Sharpen Their Attacks
Ähnlich wie Common Cybersecurity Mistakes
Ähnlich wie Common Cybersecurity Mistakes (20)
Cyber Risks & Liabilities - Cyber Security for Small Businesses

Cyber Risks & Liabilities - Cyber Security for Small Businesses
How to assess your Cybersecurity Vulnerability_.pdf

How to assess your Cybersecurity Vulnerability_.pdf
How to assess your Cybersecurity Vulnerability_.pptx

How to assess your Cybersecurity Vulnerability_.pptx
The Small Business Cyber Security Best Practice Guide

The Small Business Cyber Security Best Practice Guide
BIZGrowth Strategies — Cybersecurity Special Edition 2023

BIZGrowth Strategies — Cybersecurity Special Edition 2023
Human Error in Cyber Security Breaches | Cyberroot Risk Advisory

Human Error in Cyber Security Breaches | Cyberroot Risk Advisory
Netwealth educational webinar: Peace of mind in a digital world

Netwealth educational webinar: Peace of mind in a digital world
5 Reasons Cyber Attackers Target Small and Medium Businesses 

5 Reasons Cyber Attackers Target Small and Medium Businesses
Mark Villinski - Top 10 Tips for Educating Employees about Cybersecurity

Mark Villinski - Top 10 Tips for Educating Employees about Cybersecurity
How to Protect Your Business from Cyber Threats | The Entrepreneur Review

How to Protect Your Business from Cyber Threats | The Entrepreneur Review
10 Most Important Strategies for Cybersecurity Risk Mitigation.pdf

10 Most Important Strategies for Cybersecurity Risk Mitigation.pdf
Kürzlich hochgeladen
Saudi Arabia [ Abortion pills) Jeddah/riaydh/dammam/++918133066128☎️] cytotec tablets uses abortion pills 💊💊 How effective is the abortion pill? 💊💊 +918133066128) "Abortion pills in Jeddah" how to get cytotec tablets in Riyadh " Abortion pills in dammam*💊💊 The abortion pill is very effective. If you’re taking mifepristone and misoprostol, it depends on how far along the pregnancy is, and how many doses of medicine you take:💊💊 +918133066128) how to buy cytotec pills
At 8 weeks pregnant or less, it works about 94-98% of the time. +918133066128[ 💊💊💊 At 8-9 weeks pregnant, it works about 94-96% of the time. +918133066128) At 9-10 weeks pregnant, it works about 91-93% of the time. +918133066128)💊💊 If you take an extra dose of misoprostol, it works about 99% of the time. At 10-11 weeks pregnant, it works about 87% of the time. +918133066128) If you take an extra dose of misoprostol, it works about 98% of the time. In general, taking both mifepristone and+918133066128 misoprostol works a bit better than taking misoprostol only. +918133066128 Taking misoprostol alone works to end the+918133066128 pregnancy about 85-95% of the time — depending on how far along the+918133066128 pregnancy is and how you take the medicine. +918133066128 The abortion pill usually works, but if it doesn’t, you can take more medicine or have an in-clinic abortion. +918133066128 When can I take the abortion pill?+918133066128 In general, you can have a medication abortion up to 77 days (11 weeks)+918133066128 after the first day of your last period. If it’s been 78 days or more since the first day of your last+918133066128 period, you can have an in-clinic abortion to end your pregnancy.+918133066128
Why do people choose the abortion pill? Which kind of abortion you choose all depends on your personal+918133066128 preference and situation. With+918133066128 medication+918133066128 abortion, some people like that you don’t need to have a procedure in a doctor’s office. You can have your medication abortion on your own+918133066128 schedule, at home or in another comfortable place that you choose.+918133066128 You get to decide who you want to be with during your abortion, or you can go it alone. Because+918133066128 medication abortion is similar to a miscarriage, many people feel like it’s more “natural” and less invasive. And some+918133066128 people may not have an in-clinic abortion provider close by, so abortion pills are more available to+918133066128 them. +918133066128 Your doctor, nurse, or health center staff can help you decide which kind of abortion is best for you. +918133066128 More questions from patients: Saudi Arabia+918133066128 CYTOTEC Misoprostol Tablets. Misoprostol is a medication that can prevent stomach ulcers if you also take NSAID medications. It reduces the amount of acid in your stomach, which protects your stomach lining. The brand name of this medication is Cytotec®.+918133066128) Unwanted Kit Mifty kit IN Salmiya (+918133066128) Abortion pills IN Salmiyah Cytotec pills

Mifty kit IN Salmiya (+918133066128) Abortion pills IN Salmiyah Cytotec pillsAbortion pills in Kuwait Cytotec pills in Kuwait
Saudi Arabia [ Abortion pills) Jeddah/riaydh/dammam/++918133066128☎️] cytotec tablets uses abortion pills 💊💊 How effective is the abortion pill? 💊💊 +918133066128) "Abortion pills in Jeddah" how to get cytotec tablets in Riyadh " Abortion pills in dammam*💊💊 The abortion pill is very effective. If you’re taking mifepristone and misoprostol, it depends on how far along the pregnancy is, and how many doses of medicine you take:💊💊 +918133066128) how to buy cytotec pills
At 8 weeks pregnant or less, it works about 94-98% of the time. +918133066128[ 💊💊💊 At 8-9 weeks pregnant, it works about 94-96% of the time. +918133066128) At 9-10 weeks pregnant, it works about 91-93% of the time. +918133066128)💊💊 If you take an extra dose of misoprostol, it works about 99% of the time. At 10-11 weeks pregnant, it works about 87% of the time. +918133066128) If you take an extra dose of misoprostol, it works about 98% of the time. In general, taking both mifepristone and+918133066128 misoprostol works a bit better than taking misoprostol only. +918133066128 Taking misoprostol alone works to end the+918133066128 pregnancy about 85-95% of the time — depending on how far along the+918133066128 pregnancy is and how you take the medicine. +918133066128 The abortion pill usually works, but if it doesn’t, you can take more medicine or have an in-clinic abortion. +918133066128 When can I take the abortion pill?+918133066128 In general, you can have a medication abortion up to 77 days (11 weeks)+918133066128 after the first day of your last period. If it’s been 78 days or more since the first day of your last+918133066128 period, you can have an in-clinic abortion to end your pregnancy.+918133066128
Why do people choose the abortion pill? Which kind of abortion you choose all depends on your personal+918133066128 preference and situation. With+918133066128 medication+918133066128 abortion, some people like that you don’t need to have a procedure in a doctor’s office. You can have your medication abortion on your own+918133066128 schedule, at home or in another comfortable place that you choose.+918133066128 You get to decide who you want to be with during your abortion, or you can go it alone. Because+918133066128 medication abortion is similar to a miscarriage, many people feel like it’s more “natural” and less invasive. And some+918133066128 people may not have an in-clinic abortion provider close by, so abortion pills are more available to+918133066128 them. +918133066128 Your doctor, nurse, or health center staff can help you decide which kind of abortion is best for you. +918133066128 More questions from patients: Saudi Arabia+918133066128 CYTOTEC Misoprostol Tablets. Misoprostol is a medication that can prevent stomach ulcers if you also take NSAID medications. It reduces the amount of acid in your stomach, which protects your stomach lining. The brand name of this medication is Cytotec®.+918133066128) Unwanted Kit is a combination of two medicines, ounwanted pregnancy Kit [+918133066128] Abortion Pills IN Dubai UAE Abudhabi![unwanted pregnancy Kit [+918133066128] Abortion Pills IN Dubai UAE Abudhabi](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![unwanted pregnancy Kit [+918133066128] Abortion Pills IN Dubai UAE Abudhabi](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
unwanted pregnancy Kit [+918133066128] Abortion Pills IN Dubai UAE AbudhabiAbortion pills in Kuwait Cytotec pills in Kuwait
Kürzlich hochgeladen (20)
Marel Q1 2024 Investor Presentation from May 8, 2024

Marel Q1 2024 Investor Presentation from May 8, 2024
Rice Manufacturers in India | Shree Krishna Exports

Rice Manufacturers in India | Shree Krishna Exports
Pre Engineered Building Manufacturers Hyderabad.pptx

Pre Engineered Building Manufacturers Hyderabad.pptx
Falcon Invoice Discounting: Empowering Your Business Growth

Falcon Invoice Discounting: Empowering Your Business Growth
Al Mizhar Dubai Escorts +971561403006 Escorts Service In Al Mizhar

Al Mizhar Dubai Escorts +971561403006 Escorts Service In Al Mizhar
Jual Obat Aborsi ( Asli No.1 ) 085657271886 Obat Penggugur Kandungan Cytotec

Jual Obat Aborsi ( Asli No.1 ) 085657271886 Obat Penggugur Kandungan Cytotec
Mifty kit IN Salmiya (+918133066128) Abortion pills IN Salmiyah Cytotec pills

Mifty kit IN Salmiya (+918133066128) Abortion pills IN Salmiyah Cytotec pills
Falcon's Invoice Discounting: Your Path to Prosperity

Falcon's Invoice Discounting: Your Path to Prosperity
New 2024 Cannabis Edibles Investor Pitch Deck Template

New 2024 Cannabis Edibles Investor Pitch Deck Template
Falcon Invoice Discounting: Tailored Financial Wings

Falcon Invoice Discounting: Tailored Financial Wings
Falcon Invoice Discounting: Aviate Your Cash Flow Challenges

Falcon Invoice Discounting: Aviate Your Cash Flow Challenges
Horngren’s Cost Accounting A Managerial Emphasis, Canadian 9th edition soluti...

Horngren’s Cost Accounting A Managerial Emphasis, Canadian 9th edition soluti...
joint cost.pptx COST ACCOUNTING Sixteenth Edition ...

joint cost.pptx COST ACCOUNTING Sixteenth Edition ...
unwanted pregnancy Kit [+918133066128] Abortion Pills IN Dubai UAE Abudhabi![unwanted pregnancy Kit [+918133066128] Abortion Pills IN Dubai UAE Abudhabi](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![unwanted pregnancy Kit [+918133066128] Abortion Pills IN Dubai UAE Abudhabi](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
unwanted pregnancy Kit [+918133066128] Abortion Pills IN Dubai UAE Abudhabi
Common Cybersecurity Mistakes
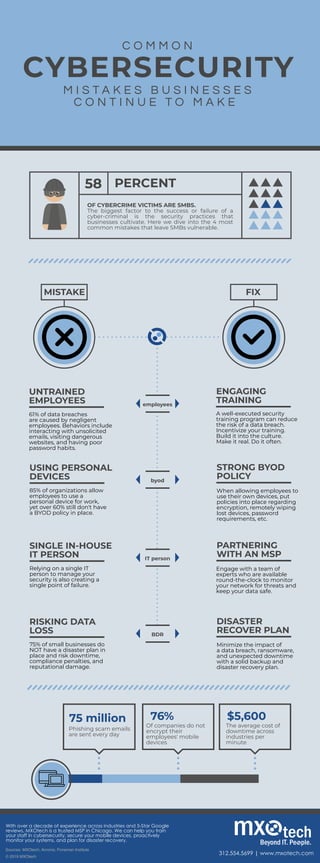
- 1. C O M M O N CYBERSECURITY M I S T A K E S B U S I N E S S E S C O N T I N U E T O M A K E MISTAKE FIX food ENGAGING TRAINING A well-executed security training program can reduce the risk of a data breach. Incentivize your training. Build it into the culture. Make it real. Do it often. UNTRAINED EMPLOYEES 61% of data breaches are caused by negligent employees. Behaviors include interacting with unsolicited emails, visiting dangerous websites, and having poor password habits. 58 PERCENT OF CYBERCRIME VICTIMS ARE SMBS. The biggest factor to the success or failure of a cyber-criminal is the security practices that businesses cultivate. Here we dive into the 4 most common mistakes that leave SMBs vulnerable. employees STRONG BYOD POLICY When allowing employees to use their own devices, put policies into place regarding encryption, remotely wiping lost devices, password requirements, etc. USING PERSONAL DEVICES 85% of organizations allow employees to use a personal device for work, yet over 60% still don't have a BYOD policy in place. byod PARTNERING WITH AN MSP Engage with a team of experts who are available round-the-clock to monitor your network for threats and keep your data safe. SINGLE IN-HOUSE IT PERSON Relying on a single IT person to manage your security is also creating a single point of failure. IT person DISASTER RECOVER PLAN Minimize the impact of a data breach, ransomware, and unexpected downtime with a solid backup and disaster recovery plan. RISKING DATA LOSS 75% of small businesses do NOT have a disaster plan in place and risk downtime, compliance penalties, and reputational damage. BDR Phishing scam emails are sent every day 75 million Of companies do not encrypt their employees' mobile devices 76% The average cost of downtime across industries per minute $5,600 Sources: MXOtech; Acronis; Poneman Institute 312.554.5699 | www.mxotech.com With over a decade of experience across industries and 5-Star Google reviews, MXOtech is a trusted MSP in Chicago. We can help you train your staff in cybersecurity, secure your mobile devices, proactively monitor your systems, and plan for disaster recovery. © 2019 MXOtech