Augmenting Netflow with the Honeypot Data for Internal Breach Monitoring and Detection
Over the past five years it has become clear that breaches are almost inevitable for any sizable enterprise. Often companies are breached for several months before accidently finding the compromise or being notified by external parties. It is clear that more needs to be done to reduce the size and scope of compromises. Internally deployed behind-the-firewall honeypots can greatly improve the visibility of compromises, especially since most netflow and IDS sensors are not monitoring all LANs and miss most intra-LAN scanning and lateral movement activity. In this talk we present Modern Honey Network (MHN), an open source (GPLv3) platform for deploying and managing honeypots in Enterprise environments. We discuss several case studies demonstrating how it augments Netflow, IDS, and other monitoring technologies. We show that it reduces the time between compromise and detection, increases the costs to the attacker, and acts as a high signal, low noise intrusion sensor. We discuss deployment best practices and integration with existing security systems.
Empfohlen
Empfohlen
Weitere ähnliche Inhalte
Andere mochten auch
Andere mochten auch (9)
Kürzlich hochgeladen
Kürzlich hochgeladen (20)
Augmenting Netflow with the Honeypot Data for Internal Breach Monitoring and Detection
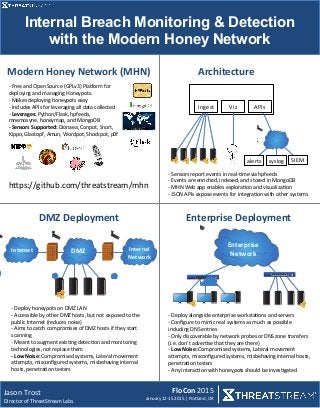
- 1. Modern Honey Network Internal Breach Monitoring & Detection with the Modern Honey Network Jason Trost Director of ThreatStream Labs FloCon 2015 January 12-‐15 2015 | Portland, OR Enterprise Deployment DMZ Deployment Enterprise Network Modern Honey Network (MHN) -‐ Free and Open Source (GPLv3) PlaIorm for deploying and managing Honeypots. -‐ Makes deploying honeypots easy -‐ Includes APIs for leveraging all data collected -‐ Leverages: Python/Flask, hpfeeds, mnemosyne, honeymap, and MongoDB -‐ Sensors Supported: Dionaea, Conpot, Snort, Kippo, Glastopf, Amun, Wordpot, Shockpot, p0f -‐ Deploy honeypots on DMZ LAN -‐ Accessible by other DMZ hosts, but not exposed to the public Internet (reduces noise) -‐ Aims to catch compromises of DMZ hosts if they start scanning -‐ Meant to augment exisYng detecYon and monitoring technologies, not replace them -‐ Low Noise: Compromised systems, Lateral movement aZempts, misconfigured systems, misbehaving internal hosts, penetraYon testers -‐ Deploy alongside enterprise workstaYons and servers -‐ Configure to mimic real systems as much as possible including DNS entries -‐ Only discoverable by network probes or DNS zone transfers (i.e. don’t adverYse that they are there) -‐ Low Noise: Compromised systems, Lateral movement aZempts, misconfigured systems, misbehaving internal hosts, penetraYon testers -‐ Any interacYon with honeypots should be invesYgated Ingest Viz Architecture APIs syslog SIEM alerts hZps://github.com/threatstream/mhn -‐ Sensors report events in real-‐Yme via hpfeeds -‐ Events are enriched, indexed, and stored in MongoDB -‐ MHN Web app enables exploraYon and visualizaYon -‐ JSON APIs expose events for integraYon with other systems DMZ Internet Internal Network
