Memory organization
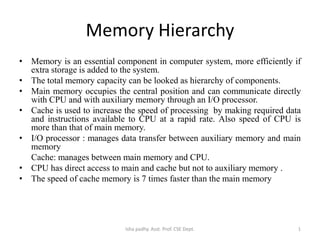
- 1. Memory Hierarchy • Memory is an essential component in computer system, more efficiently if extra storage is added to the system. • The total memory capacity can be looked as hierarchy of components. • Main memory occupies the central position and can communicate directly with CPU and with auxiliary memory through an I/O processor. • Cache is used to increase the speed of processing by making required data and instructions available to CPU at a rapid rate. Also speed of CPU is more than that of main memory. • I/O processor : manages data transfer between auxiliary memory and main memory Cache: manages between main memory and CPU. • CPU has direct access to main and cache but not to auxiliary memory . • The speed of cache memory is 7 times faster than the main memory 1Isha padhy. Asst. Prof. CSE Dept.
- 2. MEMORY SYSTEM HIERARCHY Magnetic tapes Magnetic disks I/O processor CPU Main memory Cache memory Auxiliary memory Register Cache Main Memory Magnetic Disk Magnetic TapeIncreasing size Increasing speed Increasing cost per bit
- 3. Main Memory Main memory consists of two kinds of memory 1. RAM – random access memory- volatile. Contents are destroyed when the power goes off. RAM can be static and dynamic. Static RAM stores binary info in flip flops, so info stays as long as power is applied. Dynamic RAM stores info in form of electric charges applied to capacitors. Charge stored tend to discharge with time. 2. ROM- read only memory.non volatile. Stores programs that are permanently resident in the computer.( bootstrap loader) Bootstrap loader is a program to start computer software operating when the power is turned on.( operating system) • PROM: Programmable Read Only Memory; - it allows user to load the required programs once. - faster and less expensive because they can be programmed directly by the user. • EPROM: Erasable Programmable Read Only Memory; the contents of the memory can be erased and store new data into the memory. In this case, we have to erase whole information. • Remove from the circuit for reprogramming and Erasing done by exposing chip to ultra violet rays . • EEPROM: Electrically Erasable Programmable Read Only Memory; - in this type of memory the contents of a particular location can be changed without effecting the contents of other location. Isha padhy. Asst. Prof. CSE Dept. 3
- 4. • Size of the main memory determined by addressing scheme • Ex- 16 bit computer generates 16 bit addresses capable of addressing upto 216 which is equal to 64K memory location. • 32 bit addresses, the total capacity will be 232 which is equal to 4G memory location. • The data transfer between main memory and the CPU takes place through two CPU registers. • MAR : Memory Address Register • MDR : Memory Data Register. • If the MAR is k-bit long, then the total addressable memory location will be 2k. • If the MDR is n-bit long, then the n bit of data is transferred in one memory cycle. • Data transfer takes place through address bus and data bus. • Control lines like Read, Write and Memory Function Complete (MFC) for coordinating data transfer. CPU needs to know when the desired memory function (Read or Write) has been completed. This line back to the CPU saying that the operation is complete is sometimes called memory function complete (MFC) Isha padhy. Asst. Prof. CSE Dept. 4
- 5. Isha padhy. Asst. Prof. CSE Dept. 5 - The word length of a computer is defined as the number of bits actually stored and retrieved in one main memory access. For eg. In a byte-addressable computer, generating 32 bit address from CPU to the main memory unit, high-order 30-bits determine which word will be accessed and the low-order 2- bits specifies which byte location is involved. Addressable unit of information is called memory word. - Address is assigned for each byte of information, and it is called byte- addressable computer. - One memory word contains the one or more bytes which can be addressed individually.
- 6. • Processor initiate the memory operation by loading appropriate address to MAR. • Read operation sets read control line to 1 and put the content of address to MDR. MFC to 1. • Write operation, sets write control line to 1. places the content of MDR to specified memory location and indicate the operation completed by setting up MFC to 1. • Speed of the memory unit is measured by 1. Memory Access Time:- time elapsed between the initiation of an operation and the completion of that operation (time between the Read and the MFC signals) 2. Memory Cycle Time:- minimum time delay required between the initiation of two successive memory operations (time between two successive Read operation) – slightly longer than memory access time Isha padhy. Asst. Prof. CSE Dept. 6
- 7. Isha padhy. Asst. Prof. CSE Dept. 7
- 8. RAM chip • 1 or more control inputs that select the chip only when required. • Bi-directional data bus that allows transfer of data either from memory(read) or to memory(write).This bus can be constructed by using 3 state buffers(high(1), low(0),high impedance(open ckt). • RAM capacity=128 words of 8 bits each. So for 128(27 )words 7 bits for addressing and 8 bits data bus. • Multiple select lines to select the chip when multiple chips are available in micro-computer. • The chip is in operation when CS1=1, CS2=0. bar on top of 2nd select var indicates that this input is enabled when 0. • Bus in High impedance state: when select lines are not enabled/ read –write inputs are not enabled. • When WR input is enabled data from data bus is stored in location specified by address bus. • When RD i/p signal is enabled the selected byte is placed on to data bus. Isha padhy. Asst. Prof. CSE Dept. 8
- 9. ROM chip • ROM can only read, data bus always in output mode. Isha padhy. Asst. Prof. CSE Dept. 9
- 10. Memory Address Map • The addressing of memory can be established by means of a table that specifies the memory address assigned to each chip.. A memory map is a massive table, in effect a database, that comprises complete information about how the memory is structured in a computer system. In the map, each computer file has a unique memory address reserved especially for it, so that no other data can overwrite or corrupt it. • In order for a computer to function properly, its OS (operating system) must always be able to access the right parts of its memory at the right times. When a computer first boots up(starts), the memory map tells the OS how much memory is available. • Component: specifies RAM/ROM Hexa-decimal address: a range of HD addresses for each chip address bus:16 bits, 10 are utilized here other 6 are assigned 0. x represent lines that are to be connected to address input in eac chip RAM has 128 addresses so 7 lines. ROM chip has 512 addresses so 9 lines. To distinguish between 4 RAM chips lines 8,9 are used to select line 10 distinguish RAM from ROM Isha padhy. Asst. Prof. CSE Dept. 10 RAM 1 RAM 2 RAM 3 RAM 4 ROM 0000 - 007F 0080 - 00FF 0100 - 017F 0180 - 01FF 0200 - 03FF Component Hexa address 0 0 0 x x x x x x x 0 0 1 x x x x x x x 0 1 0 x x x x x x x 0 1 1 x x x x x x x 1 x x x x x x x x x 10 9 8 7 6 5 4 3 2 1 Address bus Memory address map for micro-computer
- 11. Memory connection to CPU Isha padhy. Asst. Prof. CSE Dept. 11
- 12. Auxiliary memory • Auxiliary memory is the lowest-cost, highest-capacity, and slowest-access storage in a computer system. It is where programs and data are kept for long- term storage or when not in immediate use. Such memories tend to occur in two types-sequential access (data must be accessed in a linear sequence) and direct access (data may be accessed in any sequence). The most common sequential storage device is the magnetic tape, whereas direct-access devices include rotating drums, disks, CD-ROMs and DVD-ROMs. • The important characteristics of any device are access mode, access time, transfer rate, capacity and cost. • Access time: average time required to reach storage location in memory and obtain its contents is called access time. Access time= seek time(time required to put read/write head to a location) + transfer time( time required to move data to or from the device.) • Storage is organized in records or blocks. Reading/ writing is always done on entire records. Transfer rate is no. of blocks that the device can transfer per second after the head is placed in position. • Ex. Magnetic tapes, magnetic disks. Isha padhy. Asst. Prof. CSE Dept. 12
- 13. Average time to access some target sector approximated by : – Taccess = Tavg seek + Tavg rotation + Tavg transfer Seek time (Tavg seek) – Time to position heads over cylinder containing target sector – Typical Tavg seek = 9 ms Rotational latency (Tavg rotation) – Time waiting for first bit of target sector to pass under r/w head – Tavg rotation = 1/2 x 1/RPMs x 60 sec/1 min Transfer time (Tavg transfer) – Time to read the bits in the target sector. – Tavg transfer = 1/RPM x 1/(avg # sectors/track) x 60 secs/1 min • Transfers between the memory and the processor involves single words of data or large block of words. • The speed and efficiency of these transfers impact on performance of the system. • Performance is given by two parameters. • Latency and bandwidth. • Memory latency- the amount of time it takes to transfer a word of data to or from the memory • Bandwidth- no of bits or bytes transferred in one second. • Memory cycle time- the minimum time delay between the two independent memory operations( two successive memory read operations)Isha padhy. Asst. Prof. CSE Dept. 13
- 14. Associative memory • Generally data is stored in tabular format in memory. So to get a data from the table 2 ways can be used: - Choosing a sequence of address, reading the contents of the address, comparing the item with the contents until the match is found. - Search the item using part of or the data itself. • A memory unit accessed by content is called an associative memory. • Part of the required word is written in memory unused location and associative memory holds the actual word, then a search process selects all the matched words and marks them for reading. • Reading can be done simultaneously. • Costlier than RAM because searching logic ckts are to be implemented. Isha padhy. Asst. Prof. CSE Dept. 14
- 15. Hardware organization Isha padhy. Asst. Prof. CSE Dept. 15 -Array : m words* n bits each -Match register has m bits - A,K registers are n bit each - Each word in memory is compared bitwise with the word in argument register. - the words which match make the corresponding bit in match register as 1. - reading is done sequentially for all those words that matched. - key register is used as masking register. All the bits in argument reg is compared with the words in memory if all the bits in key register is 1, or else only those bits are compared with the words in memory whose corresponding bit in key register is 1. - Ex A: 101 110001 K: 111 000000 word1: 001 110001 (no match) Word2: 101 110101 (match)
- 16. Relation between memory array and external registers Isha padhy. Asst. Prof. CSE Dept. 16
- 17. - Cells have 2 subscripts:ij, ith word , jth location in the word - Aj is compared with all jth bit of all the words in Kj=1 - Mi=1, if all the bits match otherwise 0. - Match logic: word i is equal to the argument in A if aj=Fij, j=1,2,….n.2 bits are equal if both are 1 or 0. xj=AjFij+A’jF’ij - Mi=x1x2..xn // All X values must be 1 for Mi to be 1 - xj+K’j= xj if Kj=1 = 1 if Kj=0 // Kj should be 1 so that Fij can be compared with Aj. When Kj=1, xj is returned that means it got compared, when Kj=1, both cannot be compared. - So Mi= (x1+K’1)(x2+K’2)….(xn+K’n) When Kj=0 the term will be 1, when Kj=1, we get the term value as 1/0 depending on xj value. Isha padhy. Asst. Prof. CSE Dept. 17
- 18. Read operation Isha padhy. Asst. Prof. CSE Dept. 18
- 19. Cache memory In large programs the no of instructions are to be executed repeatedly. Loops, nested loops and some procedures call other procedures repeatedly. Instructions of few localized area of the program are repeatedly executed, while the remainder of the program is accessed relatively less. This phenomenon is referred to as locality of reference. Cache is the technique of storing a copy of data temporarily in rapidly- accessible storage media (also known as memory) local to the CPU and separate from bulk storage. Cache is faster device which is 5 to 10 times faster than the main memory. Reduces the data transfer between main memory to cache memory. Isha padhy. Asst. Prof. CSE Dept. 19
- 20. Operation of cache memory • Assumptions 1. CPU does not know that cache is in between them. 2. CPU makes read/write operation as on main memory. 3. CPU generates address and the block of data from the specified location is transferred into the cache. - In computer science, locality of reference, also called the principle of locality, is the term applied to situations where the same value or related storage locations are frequently accessed. There are three basic types of locality of reference: Temporal locality : Here a resource that is referenced at one point in time is referenced again soon afterwards. Spatial locality: Here the likelihood of referencing a storage location is greater if a storage location near it has been recently referenced. Sequential locality: Here storage is accessed sequentially, in descending or ascending order. - The performance of cache memory is measured in terms of a quantity called hit ratio. If the required word is found in cache then there is a hit otherwise a miss. Ratio of no.of hits and no. of cache reference is called hit ratio. Miss penalty time is time taken to move the required data from MM to CM. - CPU perform read operation. • The mapping of memory blocks to cache is done by mapping function. • Cache is limited in size. • If cache is full and requested memory word is not in cache make decision that which block is to be removed to provide space for new referenced memory word. It uses replacement algorithm. Isha padhy. Asst. Prof. CSE Dept. 20
- 21. When CPU makes Write operation Two ways to do 1. Cache location and main memory locations updated simultaneously. This is called store through method or write through method . 2. Update cache location only. - during replacement process, cache block is written on the main memory. This method is write back method. - this information is maintained with the help of flag bit - when write operation is done on cache block this bit is set to one. - during replacement time , checks the bit, if set to one write back the cache block to main memory otherwise not. If addressed word is not in the cache, directly write into the main memory Isha padhy. Asst. Prof. CSE Dept. 21
- 22. How the memory block is mapped to cache block Mapping function - transfers block of d to cache memory. Three mapping functions. 1. Direct mapping - A particular block of main memory can be brought to a particular block of cache memory. So, it is not flexible. 2. Associative mapping - any block of Main memory can potentially reside in any cache block position. 3. Block-set-associative mapping - blocks of cache are grouped into sets, and the mapping allows a block of main memory to reside in any block of a specific set Isha padhy. Asst. Prof. CSE Dept. 22
- 23. Example • Cache memory • Cache size= 4kb (4096 words) • No of address line required for 4KB words=12bits • Block size = 32 words • Total no of blocks in cache = 128 • To select one block out of 128 block, need 7 bit address lines. • To select one word within a block , requires 5 bit address lines Consider a main memory • Main memory capacity=64KB • No of address lines required for 64KB words=16 bits • Block size =32 words • Total no of block in main memory= 2048. • To select a block in main memory 11 bits are used. • To select a word within a block of main memory 5 bits are required. Isha padhy. Asst. Prof. CSE Dept. 23
- 24. Associative cache • MM is divided into a no. of blocks. Only the page that is required currently, is present in MM, others are brought on demand from secondary memory. A MM is divided into block, so when anything is to be transferred from MM to cache memory, complete block is transferred. block size can be 16byte/32 byte. • The address generated by CPU is divided into 2 parts. Isha padhy. Asst. Prof. CSE Dept. 24
- 25. • Cache memory will also have blocks and each block size=block size of MM. Ex 1 block contains 8 byte data(8 words of 1 byte each) which is same in both CM, MM. • Every block is identified by the block no. in address generated by CPU. • Ex assume a machine with address bits=16, every block=8 byte, so 16=(3 bits (8 byte)+13 bits for block number) • When a block is transferred from MM to CM, we need to check whether that particular block no. is present in CM or not so we have in CM another field which contains this block number, called TAG field. The no. of bits in TAG field=no.of bits in block no. field. No.of entries in TAG = no. of entry in Cache. A valid bit checks whether the block no present in the corresponding tag memory is valid or not, because initially it contains garbage value so all valid bits are 0. • So start checking with the valid bit, If its 1 then match the corresponding tag bits with block no. Search sequentially all the TAG bits. But sequentially checking will take lot of time, speed will be less. • Hardware Impl: Argument Register is connected to Address generated by CPU, from which it takes the Block no. part. Arg Reg is connected to TAG memory where it checks the block number in parallel with all the TAG elements. Comparison will be done in parallel. Match bit is 1 when there is a match. Isha padhy. Asst. Prof. CSE Dept. 25
- 26. Isha padhy. Asst. Prof. CSE Dept. 26
- 27. Direct mapping • CPU places main memory address and from this address corresponding cache address is to be generated. • Cache addr= mod(no. of cache locations)(MMAddress) ex mod(10)(23)=3 //1st fig ex mod(8)(21)=5 //2nd fig - If we consider reverse, cache loc 3 means either 3,13,23,33. we should know which memory loc data cache is holding. - Initially when system is switched on, cache contains invalid data. - Cache contents must have tag(extra information which is portion of DRAM EX which one out of 4 data in series), data, valid bit(indicating data is valid or not) - Ex for cache loc:2, valid:1, data: mem loc 32, so tag: 3 Isha padhy. Asst. Prof. CSE Dept. 27 VALID TAG DATA
- 28. Direct mapped • In associative mapping any of the block of MM can be kept in any of block of CM, in direct map the block of MM can be kept in a particular place, not any where. • Disadvantage of Associative mapping is the cost of argument register is more than RAM due to added logics for comparison. • The MM address is divided into 3 phase, Isha padhy. Asst. Prof. CSE Dept. 28 TAG BLOCK BYTE
- 29. Isha padhy. Asst. Prof. CSE Dept. 29 0 25 6 1 25 7 2 25 8 . . 255 0 3 Data Cache memory Valid bit Tag memory Main memory Tag 0 1 2 3 ……………… 31 Gr 0 1 2 255 Gr 0 2 TAG GROUP BYTE 5 8 3 Blockno (in associative mapping)= TAG+ BLOCK Each TAG denotes 256(28 ) groups, Each group has 23 =8 words. 16 bit address is divided as:
- 30. Set associative mapping MS= 64 B CS(cache size)=32 B Block size(BS)=4 B Set size=2 blocks(2 blocks in a set), also called 2 way set associative Cache blocks(lines)=CS/BS=8 blocks No. of sets=Cache blocks/set size=8/2=4 sets In MM, 64B/4B=16 blocks, In MM we don’t have sets, only blocks present. Isha padhy. Asst. Prof. CSE Dept. 30 0 1 2 3 4 5 6 7 0 1 2 0 1 15 TAG SET NO. 3 BYTE.
- 31. Virtual Memory • A computer can address more memory than the amount physically installed on the system. This extra memory is actually called virtual memory and it is a section of a hard disk that's set up to emulate the computer's RAM. • Virtual memory gives programmers the illusion that they have a very large memory and provides mechanism for dynamically translating program-generated addresses into correct main memory locations. The translation or mapping is handled automatically by the hardware by means of a mapping table. • An address used by the programmer is a virtual address (virtual memory addresses) and the set of such addresses is the Address Space. An address in main memory is called a location or physical address. The set of such locations is called the memory space. Thus, the address space is the set of addresses generated by the programs as they reference instructions and data; the memory space consists of actual main memory locations directly addressable for processing. Generally, the address space is larger than the memory space. • Consider main memory: 32K words (K=1024)= 215 and auxiliary memory 1024K words= 220. Thus, we need 15 bits to address physical memory and 20 bits for virtual memory (virtual memory can be as large as we have auxiliary storage). Here auxiliary memory has the capacity of storing information equivalent to 32 main memories. Address space N=1024K Memory space M=32K Isha padhy. Asst. Prof. CSE Dept. 31
- 32. • In multi-program computer system, programs and data are transferred to and from auxiliary and main memory based on the demands imposed by CPU. • We have 20-bit address of an instruction(to refer 20-bit virtual address) but physical memory addresses are specified with 15-bits. So a table is needed to map a virtual address of 20-bits to a physical address of 15- bits.Mapping is a dynamic operation, which means that every address is translated immediately as a word is referenced by CPU. Isha padhy. Asst. Prof. CSE Dept. 32
- 33. Address Mapping using Pages • Memory table implementation of address, mapping is simplified if the information in address space and memory space are each divided into groups of fixed size. • Blocks or page frame: The physical memory is broken down into groups of equal size called blocks, which may range from 64 to 4096 words each. • Pages: groups of address space of same size. • Example: consider computer with address space = 8K(23*210) and memory space = 4K(22*210). • If we split both spaces into groups of 1K words, we obtain 8 pages and 4 blocks. • Virtual address has 13bits .Since each page consists of 210=1024 words, high-order 3bits will specify one of 8 pages and low-order 10bits give the line address with in the pages. Memory space has 12 bits(MSB 2 bits for block number, 10 bits for the word) Isha padhy. Asst. Prof. CSE Dept. 33
- 34. Address Mapping using Pages • The mapping from address space to memory space becomes easy if virtual address is represented by two numbers : a page number address and a line with in the page. In a computer with 2pwords per page, p bits are used to specify a line address and remaining high-order bits of the virtual address specify the page number. • The memory page table consists of 8 words, one for each page. • The address in the page table denotes page number and the content of the word gives the block number where the page is stored in main memory. • Presence bit when 0 indicates page is not available in main memory and when 1 says that page has been transferred to main memory. • Table shows that pages 1, 2, 5 and 6 are now available in main memory in blocks 3, 0, 1 and 2 respectively. Isha padhy. Asst. Prof. CSE Dept. 34
- 35. Isha padhy. Asst. Prof. CSE Dept. 35
- 36. Associative memory page table • We use random-access page table which is inefficient with respect to storage utilization. For example: consider address space = 1024K words and memory space = 32K words. If each page or block contains 1K words, the number of pages is 1024 and number of blocks 32. The capacity of the memory page table must be 1024 words and only 32 locations have presence bit equal to 1. At any given time, at least 992 locations will be empty and not in use. • We can make no. of words in page table equal to no. of blocks in MM. This method can be implemented by means of an associative memory in which each word in memory containing a page number with its corresponding block number. • The page field in each associative memory table word is compared with page number bits in an argument register (which contains page number in the virtual address), if match occurs, the word is read form memory and its corresponding block number is extracted. Isha padhy. Asst. Prof. CSE Dept. 36
- 37. Page Replacement • A virtual memory system is a combination of hardware and software techniques. A memory management software system handles: • Which page in main memory could be removed to make room for a new page? • When a new page is to be transferred from auxiliary memory to main memory? • Where the page is to be placed in main memory? • When a program starts execution, one or more pages are transferred into main memory and the page table is set to indicate their position. The program is executed from main memory until it attempts to refer a page that is still in auxiliary memory. This condition is called page fault. When page fault occurs, the execution of the present program is suspended until required page is brought into memory. Since loading a page from auxiliary memory to main memory is basically an I/O operation, OS assigns this task to I/O processor. In the mean time, control is transferred to the next program in memory that is waiting to be processed in the CPU. Later, when memory block has been assigned, the original program can resume its operation. When a page fault occurs in a virtual memory system, it signifies that the page referenced by the program is not in main memory. A new page is then transferred from auxiliary memory to main memory. If main memory is full, it would be necessary to remove a page from a memory block to make a room for a new page. The policy for choosing pages to remove is determined from the replacement algorithm that is used. • 2 most common replacement algorithms are FIFO, LRU(Least Recently Used). Isha padhy. Asst. Prof. CSE Dept. 37
- 38. Memory management Hardware • Memory management system is a collection of hardware and software procedures for managing programs in memory. • Features of MMS are:- 1. A facility that maps logical memory references to physical memory addresses. 2. A provision of sharing common programs stored in memory by different users. 3. Protection of information against un-authorised access between users. • Here instead of considering fixed page size , the programs can be divided into parts called segments. • A segment is a set of logically related instructions or data elements associated with a single name. These are generated by programmers or the OS. Ex. Of segments are array of elements, functions etc. • Sharing of programs can be done ex. Many users who want to compile their programs can use a single copy of compiler instead of having separate copy of compiler in each memory of the user’s system. • The address generated by a segmented program is called a logical address. • Difference between logical and virtual address is logical address space is associated with variable length segments rather than fixed length pages. Isha padhy. Asst. Prof. CSE Dept. 38
- 39. Segment Page Mapping • The length of each segment is allowed to grow and contract according to the needs of the program being executed. One way of specifying the length of a segment is by associating with it a number of equal-sized pages. • Logical address = Segment+ page+ Word Segment: segment number Page: page within the segment word: gives the specific word within the page. A segment can have 1 page or more, basing on which the size of the segment can be decided. Here, mapping of logical address to physical address is done by using two tables: segment and page table. The entry in the segment table is a pointer address for the page table base, which is then added to page number(given in logical address). The sum point to some entry in page table and content of that page is the address of physical block. The concatenation of block field with the word field produces the final physical mapped address. Isha padhy. Asst. Prof. CSE Dept. 39
- 40. • Since memory reference from CPU will require 3 accesses to memory, 1 for segment table, one for page table and 3rd from main memory. This may increase the delay of accessing memory, so a fast associative memory is used to hold the most recent table entries. This memory is called Translation lookaside buffer(TLB) Isha padhy. Asst. Prof. CSE Dept. 40
- 41. 1. How many 128*8 RAM chips required for a memory capacity of 2048 bytes? • How many address lines are required for the above configuration. 2. An address space is specified by 24 bits and memory space by 16 bits - How many words are there in address space and memory space? Isha padhy. Asst. Prof. CSE Dept. 41