Infowatch endpoint security
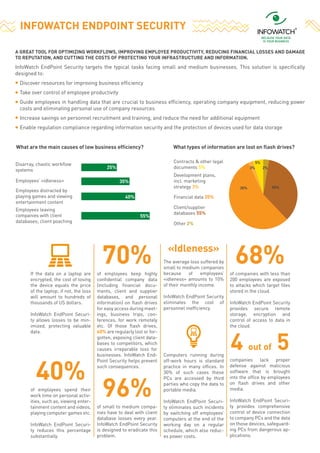
- 1. A GREAT TOOL FOR OPTIMIZING WORKFLOWS, IMPROVING EMPLOYEE PRODUCTIVITY, REDUCING FINANCIAL LOSSES AND DAMAGE TO REPUTATION, AND CUTTING THE COSTS OF PROTECTING YOUR INFRASTRUCTURE AND INFORMATION. InfoWatch EndPoint Security targets the typical tasks facing small and medium businesses. This solution is specifically designed to: Discover resources for improving business efficiency Take over control of employee productivity Guide employees in handling data that are crucial to business efficiency, operating company equipment, reducing power costs and eliminating personal use of company resources Increase savings on personnel recruitment and training, and reduce the need for additional equipment Enable regulation compliance regarding information security and the protection of devices used for data storage INFOWATCH ENDPOINT SECURITY 40%of employees spend their work time on personal activ- ities, such as, viewing enter- tainment content and videos, playing computer games etc. InfoWatch EndPoint Securi- ty reduces this percentage substantially. 70%of employees keep highly confidential company data (including financial docu- ments, client and supplier databases, and personal information) on flash drives for easy access during meet- ings, business trips, con- ferences, for work remotely etc. Of those flash drives, 60% are regularly lost or for- gotten, exposing client data- bases to competitors, which causes irreparable loss for businesses. InfoWatch End- Point Security helps prevent such consequences. 96%of small to medium compa- nies have to deal with client database losses every year. InfoWatch EndPoint Security is designed to eradicate this problem. 68%of companies with less than 200 employees are exposed to attacks which target files stored in the cloud. InfoWatch EndPoint Security provides secure remote storage, encryption and control of access to data in the cloud. «Idleness» The average loss suffered by small to medium companies because of employees’ «idleness» amounts to 10% of their monthly income. InfoWatch EndPoint Security eliminates the cost of personnel inefficiency. 4 out of 5 companies lack proper defense against malicious software that is brought into the office by employees on flash drives and other media. InfoWatch EndPoint Securi- ty provides comprehensive control of device connection to company PCs and the data on those devices, safeguard- ing PCs from dangerous ap- plications. If the data on a laptop are encrypted, the cost of losing the device equals the price of the laptop; if not, the loss will amount to hundreds of thousands of US dollars. InfoWatch EndPoint Securi- ty allows losses to be min- imized, protecting valuable data. Computers running during off-work hours is standard practice in many offices. In 30% of such cases these PCs are accessed by third parties who copy the data to portable media. InfoWatch EndPoint Securi- ty eliminates such incidents by switching off employees’ computers at the end of the working day on a regular schedule, which also reduc- es power costs. Disarray, chaotic workflow systems What are the main causes of low business efficiency? 25% 35% 40% 55% Employees’ «idleness» Employees distracted by playing games and viewing entertainment content Employees leaving companies with client databases; client poaching What types of information are lost on flash drives? Development plans, incl. marketing strategy 3% Financial data 35% Contracts & other legal documents 5% Other 2% Client/supplier databases 55% 5% 3% 35% 2% 55%
- 2. FUNCTIONAL FEATURES Control of employees’ access to valuable data InfoWatch EndPoint Security allows increased efficiency of workflow management and ensures tiered access to external devices for employees. InfoWatch EndPoint Security can manage more than 24 types of devices and external media! Employees actively use portable media, flash drives, tablets, smartphones and other communication devices at work, which implies considerable risks of valuable information being copied and used for personal purposes. This may cause irreparable harm for a company’s business and reputation. A virus from an employee’s flash drive might compromise a company’s entire IT infrastructure, blocking the operation of core business units for several hours or days. Automatic monitoring of unauthorized employee activity InfoWatch EndPoint Security supports event logs and allows the discovery of unauthorized handling of valuable information by employees. Automatic report generation enables the discovery of bottlenecks in the operations of office employees and extra resources to be located to enhance their productivity. An employee’s working day can be quite diversified, including: playing computer games, watching movies, or printing documents for personal use. 70% of companies do not track employees’ activity during work time, or the files and data they bring in or take away with them. This information is not registered in any way. INFOWATCH ENDPOINT SECURITY The solution enables full control of access to devices, ports, network interfaces and catalogs, and to cloud storage systems. It offers a variety of features to control access rights: – By means of black and white lists of devices – By device models (with exclusive access to devices according to the list of authorized device models) – By serial numbers of devices (with exclusive access to devices with certain serial numbers, irrespective of user privileges) – Through a list of authorized media and a list of authorized wireless networks (with exclusive access to authorized wi-fi networks) Event logs in InfoWatch EndPoint Security display useractivitiesperemployee: i. e., who performed certain operations and when (reading, copying, creating or deleting data) using removable media, phones, Wi-Fi networks, network folders, and cloud storage. The shadow copying feature allows access to files specified in the logs directly from the product console.
- 3. Data control during copying and storing, on premises and in the cloud Easy: Data encryption does not interfere with employees’ work and does not disrupt production. Safe: The loss or theft of media does not lead to data abuse by outsiders. InfoWatch EndPoint Security monitors all files uploaded to Dropbox, OneDrive, GoogleDrive, Yandex.Disk, or BoxSync by employees and authorizes external storage of files based on document type and data format. InfoWatch EndPoint Security allows to share files over the cloud storage, eliminating concerns about data security. Small to medium companies actively use the cloud to store and exchange information, but only a small percentage of these companies make sure their cloud data are protected. Over 80% of IT specialists are not even aware of the amount of data stored in the cloud, let alone the nature of those data or their value for the business. INFOWATCH ENDPOINT SECURITY Clients can choose a separate data encryption method for each cloud provider. Encryption keys are stored at the client’s site, not in the cloud, which ensures that they are never exposed to outsiders. Encryption is performed transparently at file level, so that employees are not involved in the process. This eliminates the possibility for employees to ignore or bypass this mechanism or to distribute unprotected confidential documents outside the company. Transparent: Data are automatically encrypted when recorded to media and decrypted when copied to hard drives. Flexible: Solvingvariousbusinessproblemsthroughencryption: you can grant access to encrypted files to all company employees, to a group of users (e.g., employees of a given department) or to a single employee. Encryption with InfoWatch EndPoint Security is:
- 4. Protection against data theft from lost laptops or flash drives InfoWatch EndPoint Security offers an easy and effortless way of protecting information through encryption. By enabling encryption in InfoWatch EndPoint Security, you can significantly enhance the security of stored data: – No outsiders can read the data – The theft or loss of devices do not cause information leaks – All data are automatically encrypted at creation without interference for employees, or requiring additional work by IT personnel (transparent encryption) Portable media and laptops are the weakest link of any corporate infrastructure, as they are very often lost or forgotten by employees. Application Control InfoWatch EndPoint Security allows businesses to manage the launch of applications and control employees’ access to applications by means of white lists (of authorized applications) and black lists (of blocked applications). This feature guarantees that no prohibited applications or files are installed or launched on any company PC. Games, movies, music, and entertainment content… Are you sure that your employees aren’t watching a new film at work right now? That they are not playing games? What tools does your company use to monitor these problems? Uncontrolled use of various applications by employees reduces their productivity, causing them to lag behind with tasks, which eventually leads to business losses because of inefficiency. INFOWATCH ENDPOINT SECURITY The solution enables data encryption on laptops, PCs, external devices, network drives, and in cloud storage directories. The encryption is carried out in the background and is fully transparent to employees. The solution employs the AES–256 OS encryption algorithm with 1,024 to 4,096-bit key lengths. InfoWatch EndPoint Security provides two ways of enabling encryption: optional, by employees, and mandatory, by system administrators. The mobile encryption feature of InfoWatch EndPoint Security allows secure off-site data processing. The solution includes a learning mode; in this mode the product automatically tracks applications launched from employees’ PCs and generates a list of trusted applications. This feature can be used to create a list of trusted applications categorized by applications developer and extension or file signature, and to setup rules for launching applications for individual employees, workstations, etc.
- 5. CLASSIC FEATURES OF INFOWATCH ENDPOINT SECURITY ARE DESCRIBED BY A SIMPLE ACRONYM C.A.F.E. – REVEALING THE CONCEPT OF THE PRODUCT AS AN EASY AND ROBUST PROTECTIVE TOOL TO ASSIST THE DEVELOPMENT OF A GROWING COMPANY: INFOWATCH ENDPOINT SECURITY Control over connections to external devices Audit of user activity Filtering by data type Encryption of data written to portable media, network folders and cloud storage InfoWatch EndPoint Security Server InfoWatch EndPoint Security Agent InfoWatch EndPoint Security Agent InfoWatch EndPoint Security Agent InfoWatch EndPoint Security Agent Management console Management console for iPhone O ine client Domain Controller Novell eDirectory InfoWatch EndPoint Security SQL Server TAN InfoWatch EndPoint Security: Perfect for small and medium business Fits the needs of any company, irrespective of industry or profile Alert to companies’ business processes Available even for small budgets Intuitive and user-friendly Easy installation and setup No extra network load Inconspicuous to employees Compatible with any software, including anti-virus programs A single management console
- 6. +7 (495) 22-900-22 IW-Global@infowatch.com www.infowatch.com BENEFITS FOR BUSINESS INFOWATCH ENDPOINT SECURITY – InfoWatch EndPoint Security substantially reduces the risks associated with data leakage: client databases copied to flash drives and passed to competitors may well put a company out of business. The product eliminates the risk of loss or theft of valuable information because its encryption feature can be used for any portable media and laptops, or for data transferred to cloud storage. – The solution reduces bandwidth consumption: InfoWatch EndPoint Security settings allow most traffic-consuming operations that are not job-related to be eliminated. – The solution reduces personnel costs: it incorporates very simple installation, setup and management procedures that can be performed without hiring a qualified administrator or IS officer. – The solution reduces power costs: its power control feature allows PCs to be switched on and off on a regular schedule, if employees forget to do so. – The solution reduces the cost of additional hardware, services and applications: InfoWatch EndPoint Security does not require the purchase of any extra hardware or software, and because of its encryption system many business features, such as document workflow management, can be deployed in the cloud, which facilitates clear cost reduction. Reduction of business costs and financial losses All necessary features in one product InfoWatch EndPoint Security does not contain any unnecessary functionality. All tasks concerning protection of information are integrated in the single user-friendly interface, which covers only decisive aspects of information security. Business process awareness InfoWatch EndPoint Security is easily adjustable to company workflows because of its modular, multicomponent structure: by pinpointing weak points in your business processes, you can provide targeted protection for such areas without restricting access to assets that are needed to complete the company’s work. Robust and high-quality product Only 1% of 1,000 companies that have installed InfoWatch EndPoint Security require support services. Faultless operation of the product eliminates concerns for system administrators, management and end users. Extreme simplicity and usability InfoWatch EndPoint Security can be installed and configured in 20 minutes, without any special qualifications or training, and it can be managed with a few clicks. The simplicity of these procedures is facilitated by the intuitive interface and business logic of the product. Affordable even on a small budget The price of InfoWatch EndPoint Security fits into the operating budget of any company. Compatibility and productivity InfoWatch EndPoint Security is fully compatible with any corporate devices, systems and applications.
