HTTP basics in relation to Applicaiton Security - OWASP
•Als PPTX, PDF herunterladen•
2 gefällt mir•1,727 views
Slides covering HTTP from an application security standpoint. Presented by @manicode and @eoinkeary For more see bccriskadvisory.com & manicode.net
Melden
Teilen
Melden
Teilen
Empfohlen
Empfohlen
Weitere ähnliche Inhalte
Was ist angesagt?
Was ist angesagt? (7)
Cross Site Scripting - Mozilla Security Learning Center

Cross Site Scripting - Mozilla Security Learning Center
Ähnlich wie HTTP basics in relation to Applicaiton Security - OWASP
Ähnlich wie HTTP basics in relation to Applicaiton Security - OWASP (20)
HTTP Security Headers Every Java Developer Must Know

HTTP Security Headers Every Java Developer Must Know
OWASP ESAPI and Microsoft Web Libraries in Cross-Site Scripting

OWASP ESAPI and Microsoft Web Libraries in Cross-Site Scripting
Identifying Web Servers: A First-look Into the Future of Web Server Fingerpri...

Identifying Web Servers: A First-look Into the Future of Web Server Fingerpri...
Web Browser Basics, Tips & Tricks - Draft 20 (Revised 5/18/17)

Web Browser Basics, Tips & Tricks - Draft 20 (Revised 5/18/17)
Hacking HTML5 offensive course (Zeronights edition)

Hacking HTML5 offensive course (Zeronights edition)
10 things I’ve learnt about web application security

10 things I’ve learnt about web application security
Warning Ahead: SecurityStorms are Brewing in Your JavaScript

Warning Ahead: SecurityStorms are Brewing in Your JavaScript
Mehr von Eoin Keary
Mehr von Eoin Keary (20)
Does a Hybrid model for vulnerability Management Make Sense.pdf

Does a Hybrid model for vulnerability Management Make Sense.pdf
Vulnerability Intelligence - Standing Still in a world full of change

Vulnerability Intelligence - Standing Still in a world full of change
Edgescan vulnerability stats report 2019 - h-isac-2-2-2019

Edgescan vulnerability stats report 2019 - h-isac-2-2-2019
Hide and seek - Attack Surface Management and continuous assessment.

Hide and seek - Attack Surface Management and continuous assessment.
Web security – everything we know is wrong cloud version

Web security – everything we know is wrong cloud version
Vulnerability management and threat detection by the numbers

Vulnerability management and threat detection by the numbers
Kürzlich hochgeladen
Call Girl Pune Indira Call Now: 8250077686 Pune Escorts Booking Contact Details WhatsApp Chat: +91-8250077686 Pune Escort Service includes providing maximum physical satisfaction to their clients as well as engaging conversation that keeps your time enjoyable and entertainin. Plus they look fabulously elegant; making an impressionable. Independent Escorts Pune understands the value of confidentiality and discretion - they will go the extra mile to meet your needs. Simply contact them via text messaging or through their online profiles; they'd be more than delighted to accommodate any request or arrange a romantic date or fun-filled night together. We provide –(INDIRA) Call Girl Pune Call Now 8250077686 Pune Escorts 24x7

(INDIRA) Call Girl Pune Call Now 8250077686 Pune Escorts 24x7Call Girls in Nagpur High Profile Call Girls
Rohini Sector 22 Call Girls Delhi 9999965857 @Sabina Saikh No Advance
Booking Contact Details :-
WhatsApp Chat :- [+91-9999965857 ]
The Best Call Girls Delhi At Your Service
Russian Call Girls Delhi Doing anything intimate with can be a wonderful way to unwind from life's stresses, while having some fun. These girls specialize in providing sexual pleasure that will satisfy your fetishes; from tease and seduce their clients to keeping it all confidential - these services are also available both install and outcall, making them great additions for parties or business events alike. Their expert sex skills include deep penetration, oral sex, cum eating and cum eating - always respecting your wishes as part of the experience
(27-April-2024(PSS)
Two shots with one girl: ₹4000/in-call, ₹7000/out-call
Body to body massage with : ₹4500/in-call
Full night for one person: ₹7000/in-call, ₹12000/out-call
Delhi Russian Escorts provide clients with the opportunity to experience an array of activities - everything from dining at upscale restaurants to watching the latest movies. Hotel call girls are available year-round to offer unforgettable experiences and fulfill all of your erotica desires. Escort services go beyond the traditional notion of call girls by providing clients with customized experiences beyond dinner companionship to social events. (27-April-2024(PSS)
Mahipalpur | Majnu Ka Tilla | Aerocity | Delhi,Noida | Gurgaon | Paharganj | GTB Nagar | Sarita Vihar | Chattarpur | Dwarka | Rajouri Garden | Connaught Place | Janakpuri
▂▃▄▅▆▇█▓▒░░▒▓█▇▆▅▄▃▂📢N-C-R⭐VIP⭐GENUINE🅰️█▬█⓿▀█▀💋 𝐆𝐈𝐑𝐋 💥ANAL SEX💥 BDSM💥69 POSE💥LIP KISS💥 DEEP SUCKING WITHOUT CONDOM💥 CUM ON FACE💥 NUDE DANCE💥 BOOBS RUBBING💥 LICKING💥HAND JOB 💏GIRLFRIEND EXPERIENCE💏 ❣️College girls, ❣️Russian girls, ❣️Working girls, ❣️North-east girls, ❣️ Punjabi girls, etc........................
EROTIC MASSAGE💥Rohini Sector 22 Call Girls Delhi 9999965857 @Sabina Saikh No Advance

Rohini Sector 22 Call Girls Delhi 9999965857 @Sabina Saikh No AdvanceCall Girls In Delhi Whatsup 9873940964 Enjoy Unlimited Pleasure
Russian Call Girls in %(+971524965298 )# Call Girls in Dubai
Russian Call Girls in %(+971524965298 )# Call Girls in Dubai
Russian Call Girls in %(+971524965298 )# Call Girls in Dubai
Russian Call Girls in %(+971524965298 )# Call Girls in Dubai
Russian Call Girls in %(+971524965298 )# Call Girls in Dubai
Russian Call Girls in %(+971524965298 )# Call Girls in Dubai
Russian Call Girls in %(+971524965298 )# Call Girls in Dubai

Russian Call Girls in %(+971524965298 )# Call Girls in DubaiDubai call girls 971524965298 Call girls in Bur Dubai
Russian #ℂall #Girls in #Goa That's where #Goa #ℂall -#Girls comes in. As the premier outℂall ℂall -Girls service in Goa , we provide beautiful, charming ℂall -Girls in Goa who will join you in the privacy of your hotel room or villa for an evening of pleasure and delight. That's where Goa ℂall -Girls comes in. As the premier outℂall ℂall -Girls service in Goa , We provide beautiful, charming ℂall -Girls in Goa who will join you in the privacy of your hotel room or villa for an evening of pleasure and delight. Our VIP Girl's in Goa ' will also provide you the top-level satisfaction. We have available Filipina Girl's who can fully satisfy our clients. Our Escorts in Goa ' Agency always hires the Girl's on the basis of their intelligence, sexual appearance, beauty, attractiveness, and friendly nature. For Booking Kindly Message on Whatsapp
ℂall / Whatsapp- Goa 'ℂall 'girls 'ℂall 'girls in Goa 'ℂall 'girls Service, Indian 'ℂall 'girls in Goa , Russian 'ℂall 'girls in Goa , Independent 'ℂall 'girls in Goa Cheap 'ℂall 'girls in Goa Russian 'ℂall 'girls in Goa , Hot Al Barsha 'ℂall 'girls
I've Used the Service from this agency history in Bur Goa Area. The 'ℂall 'girl was so corporative and Fashionable. She Came Into my hostel room. I got This Goa 'ℂall 'girl figures from Goa so straightway I communicated her. I'm so happy after using this agency service. This is largely recommended if you're a ℂall er in Goa and you do n’t have an idea how to get the 'ℂall 'girls In Goa . This agency is having a big collection of Indian 'ℂall 'girls In Goa and Russian 'ℂall 'girls In Goa and the stylish thing about it's they all are vindicated, staff. Indeed They've a huge variety of Independent 'ℂall 'girls In Goa as well. This agency is holding a verified Staff which is a great occasion for every stoner in Goa or any part of Goa .Hot Service (+9316020077 ) Goa Call Girls Real Photos and Genuine Service

Hot Service (+9316020077 ) Goa Call Girls Real Photos and Genuine Servicesexy call girls service in goa
@9999965857 🫦 Sexy Desi Call Girls Laxmi Nagar 💓 High Profile Escorts Delhi 🫶
Delhi Russian Escorts provide clients with the opportunity to experience an array of activities - everything from dining at upscale restaurants to watching the latest movies. Hotel call girls are available year-round to offer unforgettable experiences and fulfill all of your erotica desires. Escort services go beyond the traditional notion of call girls by providing clients with customized experiences beyond dinner companionship to social events. (27-April-2024(PSS)
Mahipalpur | Majnu Ka Tilla | Aerocity | Delhi,Noida | Gurgaon | Paharganj | GTB Nagar | Sarita Vihar | Chattarpur | Dwarka | Rajouri Garden | Connaught Place | Janakpuri
▂▃▄▅▆▇█▓▒░░▒▓█▇▆▅▄▃▂📢N-C-R⭐VIP⭐GENUINE🅰️█▬█⓿▀█▀💋 𝐆𝐈𝐑𝐋 💥ANAL SEX💥 BDSM💥69 POSE💥LIP KISS💥 DEEP SUCKING WITHOUT CONDOM💥 CUM ON FACE💥 NUDE DANCE💥 BOOBS RUBBING💥 LICKING💥HAND JOB 💏GIRLFRIEND EXPERIENCE💏 ❣️College girls, ❣️Russian girls, ❣️Working girls, ❣️North-east girls, ❣️ Punjabi girls, etc........................
EROTIC MASSAGE💥@9999965857 🫦 Sexy Desi Call Girls Laxmi Nagar 💓 High Profile Escorts Delhi 🫶

@9999965857 🫦 Sexy Desi Call Girls Laxmi Nagar 💓 High Profile Escorts Delhi 🫶Call Girls In Delhi Whatsup 9873940964 Enjoy Unlimited Pleasure
Top Rated Pune Call Girls Daund ⟟ 6297143586 ⟟ Call Me For Genuine Sex Service At Affordable Rate
Booking Contact Details
WhatsApp Chat: +91-6297143586
pune Escort Service includes providing maximum physical satisfaction to their clients as well as engaging conversation that keeps your time enjoyable and entertaining. Plus they look fabulously elegant; making an impressionable.
Independent Escorts pune understands the value of confidentiality and discretion - they will go the extra mile to meet your needs. Simply contact them via text messaging or through their online profiles; they'd be more than delighted to accommodate any request or arrange a romantic date or fun-filled night together.
We provide -
01-may-2024(v.n)
Top Rated Pune Call Girls Daund ⟟ 6297143586 ⟟ Call Me For Genuine Sex Servi...

Top Rated Pune Call Girls Daund ⟟ 6297143586 ⟟ Call Me For Genuine Sex Servi...Call Girls in Nagpur High Profile
Kürzlich hochgeladen (20)
(INDIRA) Call Girl Pune Call Now 8250077686 Pune Escorts 24x7

(INDIRA) Call Girl Pune Call Now 8250077686 Pune Escorts 24x7
𓀤Call On 7877925207 𓀤 Ahmedguda Call Girls Hot Model With Sexy Bhabi Ready Fo...

𓀤Call On 7877925207 𓀤 Ahmedguda Call Girls Hot Model With Sexy Bhabi Ready Fo...
Call Now ☎ 8264348440 !! Call Girls in Sarai Rohilla Escort Service Delhi N.C.R.

Call Now ☎ 8264348440 !! Call Girls in Sarai Rohilla Escort Service Delhi N.C.R.
Delhi Call Girls Rohini 9711199171 ☎✔👌✔ Whatsapp Hard And Sexy Vip Call

Delhi Call Girls Rohini 9711199171 ☎✔👌✔ Whatsapp Hard And Sexy Vip Call
Rohini Sector 22 Call Girls Delhi 9999965857 @Sabina Saikh No Advance

Rohini Sector 22 Call Girls Delhi 9999965857 @Sabina Saikh No Advance
Call Girls Service Chandigarh Lucky ❤️ 7710465962 Independent Call Girls In C...

Call Girls Service Chandigarh Lucky ❤️ 7710465962 Independent Call Girls In C...
Pune Airport ( Call Girls ) Pune 6297143586 Hot Model With Sexy Bhabi Ready...

Pune Airport ( Call Girls ) Pune 6297143586 Hot Model With Sexy Bhabi Ready...
Call Now ☎ 8264348440 !! Call Girls in Shahpur Jat Escort Service Delhi N.C.R.

Call Now ☎ 8264348440 !! Call Girls in Shahpur Jat Escort Service Delhi N.C.R.
✂️ 👅 Independent Andheri Escorts With Room Vashi Call Girls 💃 9004004663

✂️ 👅 Independent Andheri Escorts With Room Vashi Call Girls 💃 9004004663
'Future Evolution of the Internet' delivered by Geoff Huston at Everything Op...

'Future Evolution of the Internet' delivered by Geoff Huston at Everything Op...
Call Girls Ludhiana Just Call 98765-12871 Top Class Call Girl Service Available

Call Girls Ludhiana Just Call 98765-12871 Top Class Call Girl Service Available
Call Girls In Sukhdev Vihar Delhi 💯Call Us 🔝8264348440🔝

Call Girls In Sukhdev Vihar Delhi 💯Call Us 🔝8264348440🔝
Russian Call Girls in %(+971524965298 )# Call Girls in Dubai

Russian Call Girls in %(+971524965298 )# Call Girls in Dubai
Hot Service (+9316020077 ) Goa Call Girls Real Photos and Genuine Service

Hot Service (+9316020077 ) Goa Call Girls Real Photos and Genuine Service
WhatsApp 📞 8448380779 ✅Call Girls In Mamura Sector 66 ( Noida)

WhatsApp 📞 8448380779 ✅Call Girls In Mamura Sector 66 ( Noida)
On Starlink, presented by Geoff Huston at NZNOG 2024

On Starlink, presented by Geoff Huston at NZNOG 2024
Best VIP Call Girls Noida Sector 75 Call Me: 8448380779

Best VIP Call Girls Noida Sector 75 Call Me: 8448380779
@9999965857 🫦 Sexy Desi Call Girls Laxmi Nagar 💓 High Profile Escorts Delhi 🫶

@9999965857 🫦 Sexy Desi Call Girls Laxmi Nagar 💓 High Profile Escorts Delhi 🫶
Top Rated Pune Call Girls Daund ⟟ 6297143586 ⟟ Call Me For Genuine Sex Servi...

Top Rated Pune Call Girls Daund ⟟ 6297143586 ⟟ Call Me For Genuine Sex Servi...
HTTP basics in relation to Applicaiton Security - OWASP
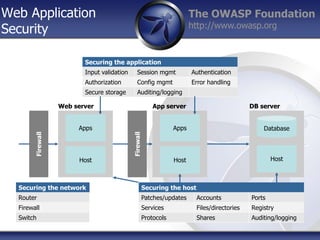
- 1. The OWASP Foundation http://www.owasp.org Web Application Security Host Apps Firewall Host Apps Database Host Web server App server DB server Securing the application Input validation Session mgmt Authentication Authorization Config mgmt Error handling Secure storage Auditing/logging Securing the network Router Firewall Switch Securing the host Patches/updates Accounts Ports Services Files/directories Registry Protocols Shares Auditing/logging Firewall
- 2. The OWASP Foundation http://www.owasp.org HTTP is stateless and hence requests and responses to communicate between browser and server have no memory. Most typical HTTP requests utilise either GET or POST methods Scripting can occur on: Server-Side (e.g. perl, asp, jsp) Client-Side (javascript, flash, applets) Web server file mappings allow the web server to handle certain file types using specific handlers (ASP, ASP.NET, Java, JSP,CFM etc) Data is posted to the application through HTTP methods, this data is processed by the relevant script and result returned to the user’s browser Web Application Behaviour 2
- 3. The OWASP Foundation http://www.owasp.org HTTP POST HTTP GET “GET” exposes sensitive authentication information in the URL In Web Server and Proxy Server logs In the http referer header In Bookmarks/Favorites often emailed to others “POST” places information in the body of the request and not the URL Enforce HTTPS POST For Sensitive Data Transport 3
- 4. The OWASP Foundation http://www.owasp.org GET vs POST HTTP Request GET /search.jsp?name=blah&type=1 HTTP/1.0 User-Agent: Mozilla/4.0 Host: www.mywebsite.com Cookie: SESSIONID=2KDSU72H9GSA289 <CRLF> GET request POST request POST /search.jsp HTTP/1.0 User-Agent: Mozilla/4.0 Host: www.mywebsite.com Content-Length: 16 Cookie: SESSIONID=2KDSU72H9GSA289 <CRLF> name=blah&type=1 <CRLF>
- 5. The OWASP Foundation http://www.owasp.org What are HTTP Headers? HTTP headers are components of the message header of HTTP Requests and Responses HTTP headers define different aspects of an HTTP transaction HTTP headers are colon-separated name-value pairs in clear-text string format, terminated by a carriage return (CR) and line feed (LF) character sequence. http://en.wikipedia.org/wiki/List_of_HTTP_header_fields
- 6. The OWASP Foundation http://www.owasp.org Security HTTP Response Headers X-Frame-Options X-Xss-Protection X-Content-Type-Options Content Security Policy Access-Control-Allow-Origin HTTPS Strict Transport Security Cache-Control / Pragma
- 7. The OWASP Foundation http://www.owasp.org Security HTTP Response headers X-Frame-Options 'SAMEORIGIN' - allow framing on same domain. Set it to 'DENY' to deny framing at all or 'ALLOWALL' if you want to allow framing for all website. X-XSS-Protection '1; mode=block' - use XSS Auditor and block page if XSS attack is detected. Set it to '0;' if you want to switch XSS Auditor off(useful if response contents scripts from request parameters) X-Content-Type-Options 'nosniff’ - stops the browser from guessing the MIME type of a file. X-Content-Security-Policy - A powerful mechanism for controlling which sites certain content types can be loaded from Access-Control-Allow-Origin - used to control which sites are allowed to bypass same origin policies and send cross-origin requests. Strict-Transport-Security - used to control if the browser is allowed to only access a site over a secure connection Cache-Control - used to control mandatory content caching rules
- 8. The OWASP Foundation http://www.owasp.org X-Frame-Options Protects you from most classes of Clickjacking X-Frame-Options: DENY X-Frame-Options: SAMEORIGIN X-Frame-Options: ALLOW FROM
- 9. The OWASP Foundation http://www.owasp.org X-XSS-Protection Use the browser’s built in XSS Auditor X-XSS-Protection: [0-1](; mode=block)? X-XSS-Protection: 1; mode=block
- 10. The OWASP Foundation http://www.owasp.org X-ContentType-Options Fixes mime sniffing attacks Only applies to IE, because only IE would do something like this X-Content-Type-Options = ‘nosniff’
- 11. The OWASP Foundation http://www.owasp.org Content Security Policy • Anti-XSS W3C standard http://www.w3.org/TR/CSP/ • Move all inline script and style into external files • Add the X-Content-Security-Policy response header to instruct the browser that CSP is in use • Define a policy for the site regarding loading of content • Chrome version 25 and later (50%) • Firefox version 23 and later (30%) • Internet Explorer version 10 and later (10%)
- 12. The OWASP Foundation http://www.owasp.org Strict Transport Security Strict-transport-security: max-age=10000000 Do all of your subdomains support SSL? Strict-transport-security: max-age=10000000; includeSubdomains
- 13. The OWASP Foundation http://www.owasp.org Disabling the Browser Cache Add the following as part of your HTTP Response Cache-Control: no-store, no-cache, must-revalidate Expires: -1
- 14. The OWASP Foundation http://www.owasp.org HTTP Security Headers Tool Secure headers! Open source https://github.com/twitter/secureheaders
Hinweis der Redaktion
- Note that security is often begun in the network and host boxes, but application security requires work at the top box (application layer)
- // HTTP 1.1 response.setHeader("Cache-Control", "no-store, no-cache, must-revalidate"); // HTTP 1.0 response.setHeader("Pragma","no-cache"); response.setDateHeader("Expires", -1);
- save resources since nothing is framed
