Disabling Ports 135 and 445 to protect the Road Warrior
•
2 gefällt mir•1,030 views
Step-by-step instructions to close down unused ports in an unprotected (non-firewalled) public WiFi access point.
Melden
Teilen
Melden
Teilen
Empfohlen
Weitere ähnliche Inhalte
Was ist angesagt?
Was ist angesagt? (15)
Mission Critical Security in a Post-Stuxnet World Part 1

Mission Critical Security in a Post-Stuxnet World Part 1
RCCreator Guidance. Remote control adding (copy codes from your original remo...

RCCreator Guidance. Remote control adding (copy codes from your original remo...
Andere mochten auch
Andere mochten auch (20)
Textil laboral y calzado de seguridad J'HAYBER WORKS - 2013

Textil laboral y calzado de seguridad J'HAYBER WORKS - 2013
Estat de l’art del digital signage i l'outdoor broadcasting

Estat de l’art del digital signage i l'outdoor broadcasting
Tutorial on Using Amazon Mechanical Turk (MTurk) for HCI Research

Tutorial on Using Amazon Mechanical Turk (MTurk) for HCI Research
Historical Perspective of the Cooperative Movement

Historical Perspective of the Cooperative Movement
Ähnlich wie Disabling Ports 135 and 445 to protect the Road Warrior
Ähnlich wie Disabling Ports 135 and 445 to protect the Road Warrior (20)
Hacker Halted 2014 - Post-Exploitation After Having Remote Access

Hacker Halted 2014 - Post-Exploitation After Having Remote Access
Lab-10 Malware Creation and Denial of Service (DoS) In t.docx

Lab-10 Malware Creation and Denial of Service (DoS) In t.docx
Lab-2 Buffer Overflow In this lab, you will gain insight

Lab-2 Buffer Overflow In this lab, you will gain insight
Hacking Highly Secured Enterprise Environments by Zoltan Balazs

Hacking Highly Secured Enterprise Environments by Zoltan Balazs
IT Essentials (Version 7.0) - ITE Chapter 13 Exam Answers

IT Essentials (Version 7.0) - ITE Chapter 13 Exam Answers
Defcon 22-zoltan-balazs-bypass-firewalls-application-whiteli

Defcon 22-zoltan-balazs-bypass-firewalls-application-whiteli
Mehr von David Sweigert
Mehr von David Sweigert (20)
The hacking methods of the Singularity Event doomsday cult (TYLER A.I.)

The hacking methods of the Singularity Event doomsday cult (TYLER A.I.)
Sample Network Analysis Report based on Wireshark Analysis

Sample Network Analysis Report based on Wireshark Analysis
Department of Defense standard 8570 - CompTia Advanced Security Practitioner 

Department of Defense standard 8570 - CompTia Advanced Security Practitioner
National Cyber Security Awareness Month - October 2017

National Cyber Security Awareness Month - October 2017
California Attorney General Notification Penal Code 646.9

California Attorney General Notification Penal Code 646.9
Congressional support of Ethical Hacking and Cyber Security

Congressional support of Ethical Hacking and Cyber Security
EXAM NOTES for DOD Standard 8570 CompTia Advanced Security Practitioner (CASP)

EXAM NOTES for DOD Standard 8570 CompTia Advanced Security Practitioner (CASP)
Application of Racketeering Law to Suppress CrowdStalking Threats

Application of Racketeering Law to Suppress CrowdStalking Threats
Canada Communications Security Establishment - Threat Vector Chart

Canada Communications Security Establishment - Threat Vector Chart
Port of Charleston evacuation case study: The cognitive threat of conspiracy ...

Port of Charleston evacuation case study: The cognitive threat of conspiracy ...
Cyber Incident Response Team - NIMS - Public Comment

Cyber Incident Response Team - NIMS - Public Comment
National Incident Management System (NIMS) NQS DRAFT

National Incident Management System (NIMS) NQS DRAFT
National Incident Management System - NQS Public Feedback

National Incident Management System - NQS Public Feedback
Nursing meets Hacking -- Medical Computer Emergency Response Teams -- MedCERT

Nursing meets Hacking -- Medical Computer Emergency Response Teams -- MedCERT
Cyber Risk Assessment for the Emergency Services Sector - DHS

Cyber Risk Assessment for the Emergency Services Sector - DHS
Kürzlich hochgeladen
❤️Call girls in Jalandhar ☎️9876848877☎️ Call Girl service in Jalandhar☎️ Jal...

❤️Call girls in Jalandhar ☎️9876848877☎️ Call Girl service in Jalandhar☎️ Jal...chandigarhentertainm
Kürzlich hochgeladen (20)
Call Now ☎ 9999965857 !! Call Girls in Hauz Khas Escort Service Delhi N.C.R.

Call Now ☎ 9999965857 !! Call Girls in Hauz Khas Escort Service Delhi N.C.R.
Jaipur Call Girls 9257276172 Call Girl in Jaipur Rajasthan

Jaipur Call Girls 9257276172 Call Girl in Jaipur Rajasthan
Russian Call Girls Kota * 8250192130 Service starts from just ₹9999 ✅

Russian Call Girls Kota * 8250192130 Service starts from just ₹9999 ✅
bhubaneswar Call Girls 👙 6297143586 👙 Genuine WhatsApp Number for Real Meet

bhubaneswar Call Girls 👙 6297143586 👙 Genuine WhatsApp Number for Real Meet
Russian Call Girls in Noida Pallavi 9711199171 High Class Call Girl Near Me

Russian Call Girls in Noida Pallavi 9711199171 High Class Call Girl Near Me
Call Girls Service Faridabad 📲 9999965857 ヅ10k NiGhT Call Girls In Faridabad

Call Girls Service Faridabad 📲 9999965857 ヅ10k NiGhT Call Girls In Faridabad
Nanded Call Girls 👙 6297143586 👙 Genuine WhatsApp Number for Real Meet

Nanded Call Girls 👙 6297143586 👙 Genuine WhatsApp Number for Real Meet
VIP Call Girl Sector 32 Noida Just Book Me 9711199171

VIP Call Girl Sector 32 Noida Just Book Me 9711199171
Call Girl In Zirakpur ❤️♀️@ 9988299661 Zirakpur Call Girls Near Me ❤️♀️@ Sexy...

Call Girl In Zirakpur ❤️♀️@ 9988299661 Zirakpur Call Girls Near Me ❤️♀️@ Sexy...
Chandigarh Call Girls 👙 7001035870 👙 Genuine WhatsApp Number for Real Meet

Chandigarh Call Girls 👙 7001035870 👙 Genuine WhatsApp Number for Real Meet
Mangalore Call Girls 👙 6297143586 👙 Genuine WhatsApp Number for Real Meet

Mangalore Call Girls 👙 6297143586 👙 Genuine WhatsApp Number for Real Meet
❤️♀️@ Jaipur Call Girls ❤️♀️@ Jaispreet Call Girl Services in Jaipur QRYPCF ...

❤️♀️@ Jaipur Call Girls ❤️♀️@ Jaispreet Call Girl Services in Jaipur QRYPCF ...
Call Girl Raipur 📲 9999965857 ヅ10k NiGhT Call Girls In Raipur

Call Girl Raipur 📲 9999965857 ヅ10k NiGhT Call Girls In Raipur
❤️♀️@ Jaipur Call Girl Agency ❤️♀️@ Manjeet Russian Call Girls Service in Jai...

❤️♀️@ Jaipur Call Girl Agency ❤️♀️@ Manjeet Russian Call Girls Service in Jai...
❤️♀️@ Jaipur Call Girls ❤️♀️@ Meghna Jaipur Call Girls Number CRTHNR Call G...

❤️♀️@ Jaipur Call Girls ❤️♀️@ Meghna Jaipur Call Girls Number CRTHNR Call G...
❤️Call girls in Jalandhar ☎️9876848877☎️ Call Girl service in Jalandhar☎️ Jal...

❤️Call girls in Jalandhar ☎️9876848877☎️ Call Girl service in Jalandhar☎️ Jal...
Jalna Call Girls 👙 6297143586 👙 Genuine WhatsApp Number for Real Meet

Jalna Call Girls 👙 6297143586 👙 Genuine WhatsApp Number for Real Meet
VIP Call Girl DLF Phase 2 Gurgaon (Noida) Just Meet Me@ 9711199012

VIP Call Girl DLF Phase 2 Gurgaon (Noida) Just Meet Me@ 9711199012
Hubli Call Girls 👙 6297143586 👙 Genuine WhatsApp Number for Real Meet

Hubli Call Girls 👙 6297143586 👙 Genuine WhatsApp Number for Real Meet
Disabling Ports 135 and 445 to protect the Road Warrior
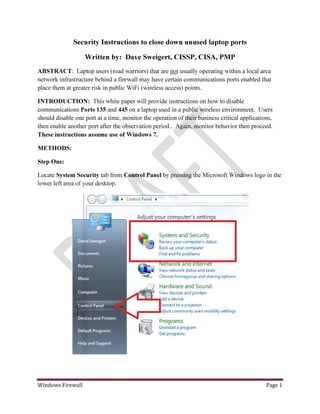
- 1. Windows Firewall Page 1 Security Instructions to close down unused laptop ports Written by: Dave Sweigert, CISSP, CISA, PMP ABSTRACT: Laptop users (road warriors) that are not usually operating within a local area network infrastructure behind a firewall may have certain communications ports enabled that place them at greater risk in public WiFi (wireless access) points. INTRODUCTION: This white paper will provide instructions on how to disable communications Ports 135 and 445 on a laptop used in a public wireless environment. Users should disable one port at a time, monitor the operation of their business critical applications, then enable another port after the observation period.. Again, monitor behavior then proceed. These instructions assume use of Windows 7. METHODS: Step One: Locate System Security tab from Control Panel by pressing the Microsoft Windows logo in the lower left area of your desktop.
- 2. Windows Firewall Page 2 Step Two: Locate the FIREWALL capability. Step Three: Click Advanced Settings
- 3. Windows Firewall Page 3 Step Four: Click INBOUND RULES on the left tool bar and observe NEW RULE in the right hand tool bar. Step Five: Click NEW RULE then observe a new dialogue box, click PORT.
- 4. Windows Firewall Page 4 Step Six: Enter NEXT then observe SPECIFIED LOCAL PORTS; enter 135 then NEXT DISCUSSION: Well known malware Root kits can use port 135 to transmit data back to home base and download more malware. An attacker who can access TCP or ports 135, 139 or 445 could execute arbitrary code with Local System privileges. This allows the attacker to gain complete control over the exploited system. On systems protected by an infrastructure firewall, it is a standard practice to block these ports due to the known associated risks.
- 6. Windows Firewall Page 6 Step Seven: Select BLOCK the connection and enter NEXT.
- 7. Windows Firewall Page 7 Step Eight: Leave all check marks in-place and proceed with NEXT.
- 8. Windows Firewall Page 8 Step Nine: Apply a suitable name to this rule; such as “Block Inbound Port 135”.
- 9. Windows Firewall Page 9 Step Ten: Observe the new rule. Repeat the same process for OUTBOUND Port 135. After a positive observation period, repeat for Port 445 (notice OUTBOUND RULES below). RESULTS: Inbound and Outbound attempts to use these ports will be disabled. In sum, these ports are considered unnecessary in a WiFi public setting and are considered another gateway for malicious software and hacker activities.
