Breach reporting requirements by State
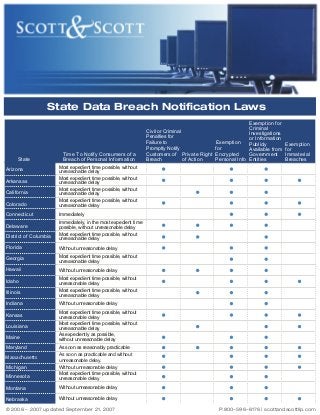
- 1. State Data Breach Notification Laws State Time To Notify Consumers of a Breach of Personal Information Colorado Exemption for Immaterial Breaches Most expedient time possible, without unreasonable delay Most expedient time possible, without unreasonable delay Most expedient time possible, without unreasonable delay Most expedient time possible, without unreasonable delay Connecticut Exemption for Criminal Civil or Criminal Investigations Penalties for or Information Failure to Exemption Publicly Promptly Notify for Available from Customers of Private Right Encrypted Government Breach of Action Personal Info Entities Immediately Arizona Arkansas California District of Columbia Immediately, in the most expedient time possible, without unreasonable delay Most expedient time possible, without unreasonable delay Florida Without unreasonable delay Georgia Most expedient time possible, without unreasonable delay Hawaii Without unreasonable delay Idaho Most expedient time possible, without unreasonable delay Most expedient time possible, without unreasonable delay Delaware Illinois Indiana Without unreasonable delay Kansas Most expedient time possible, without unreasonable delay Most expedient time possible, without unreasonable delay As expediently as possible, without unreasonable delay Louisiana Maine Maryland Massachusetts Michigan As soon as reasonably practicable As soon as practicable and without unreasonable delay. Minnesota Without unreasonable delay Most expedient time possible, without unreasonable delay Montana Without unreasonable delay Nebraska Without unreasonable delay © 2006 - 2007 updated September 21, 2007 P:800-596-6176 | scottandscottllp.com
- 2. State Data Breach Notification Laws State Time To Notify Consumers of a Breach of Personal Information Nevada As soon as possible, without unreasonable delay New Hampshire Civil or Criminal Penalties for Failure to Promptly Notify Customers of Private Right Breach of Action Exemption for Criminal Investigations or Information Exemption Publicly for Available from Encrypted Government Personal Info Entities Exemption for Immaterial Breaches As soon as possible. New York Most expedient time possible, without unreasonable delay Most expedient time possible, without unreasonable delay North Carolina Without unreasonable delay North Dakota * Most expedient time possible, without unreasonable delay New Jersey Oregon Most expedient time possible, but not later than 45 days Most expedient time possible, without unreasonable delay Most expedient time possible, without unreasonable delay Pennsylvania Without unreasonable delay Rhode Island Tennessee Most expedient time possible, without unreasonable delay Most expedient time possible, without unreasonable delay Texas As quickly as possible Utah Most expedient time possible, without unreasonable delay Most expedient time possible, without unreasonable delay Most expedient time possible, without unreasonable delay Within a reasonable time, not to exceed 45 days As soon as possible, in the most expedient time possible and without unreasonable delay Ohio Oklahoma Vermont Washington Wisconsin Wyoming * The private cause of action is assigned to the data collector whose information was breached against the party responsible for the breach. © 2006 - 2007 updated September 21, 2007 P:800-596-6176 | scottandscottllp.com
