Block Armour Case Study
•
0 gefällt mir•333 views
Check out our latest case study about how we helped a leading Compliance consultancy an BPO to enable secure and compliant access to IT systems for teams working from home
Melden
Teilen
Melden
Teilen
Downloaden Sie, um offline zu lesen
Empfohlen
Empfohlen
Weitere ähnliche Inhalte
Was ist angesagt?
Was ist angesagt? (19)
Block Armour Zero Trust Solution for Hybrid and Distributed IT environments

Block Armour Zero Trust Solution for Hybrid and Distributed IT environments
Zero Trust Cybersecurity for Microsoft Azure Cloud 

Zero Trust Cybersecurity for Microsoft Azure Cloud
IoT Armour - Next-gen Zero Trust Cybersecurity for Industry 4.0 Architecture 

IoT Armour - Next-gen Zero Trust Cybersecurity for Industry 4.0 Architecture
Next-generation Zero Trust Cybersecurity for the Space Age

Next-generation Zero Trust Cybersecurity for the Space Age
CASE STUDY: How Block Armour enabled secure remote access to on- premise as ...

CASE STUDY: How Block Armour enabled secure remote access to on- premise as ...
Block Armour Unified Secure Access Solution (based on Zero Trust principles)

Block Armour Unified Secure Access Solution (based on Zero Trust principles)
Out Go The Lights: An enlightening discussion of IoT automation security By D...

Out Go The Lights: An enlightening discussion of IoT automation security By D...
Transforming Smart Building Cybersecurity Strategy for the Age of IoT

Transforming Smart Building Cybersecurity Strategy for the Age of IoT
Ähnlich wie Block Armour Case Study
Ähnlich wie Block Armour Case Study (20)
COVID-19: Strategies to Stay Secure and Ensure Business Continuity

COVID-19: Strategies to Stay Secure and Ensure Business Continuity
Smarter Commerce Summit - IBM MobileFirst Services

Smarter Commerce Summit - IBM MobileFirst Services
DSS ITSEC Webinars 2013 - Network Access Control + Mobile Security (Forescout)

DSS ITSEC Webinars 2013 - Network Access Control + Mobile Security (Forescout)
WatchGuard Integrates with CommScope RUCKUS: Full Solutions for 2021

WatchGuard Integrates with CommScope RUCKUS: Full Solutions for 2021
Security as a Service with Microsoft Presented by Razor Technology

Security as a Service with Microsoft Presented by Razor Technology
Just-How-Secure-is-your-Remote-Workforce-Infinity-Group-Ebook.pdf

Just-How-Secure-is-your-Remote-Workforce-Infinity-Group-Ebook.pdf
Zero trust for everybody: 3 ways to get there fast

Zero trust for everybody: 3 ways to get there fast
Mehr von Block Armour
Mehr von Block Armour (9)
Blockchain Defined Perimeter (BDP) - Experience the power of Software Defined...

Blockchain Defined Perimeter (BDP) - Experience the power of Software Defined...
Block Armour Blockchain Defined Perimeter Brochure

Block Armour Blockchain Defined Perimeter Brochure
Block Armour securing critical IoT infrastructure and 5g networks

Block Armour securing critical IoT infrastructure and 5g networks
Block Armour Zero Trust Cybersecurity for the Space Age

Block Armour Zero Trust Cybersecurity for the Space Age
Kürzlich hochgeladen
Kürzlich hochgeladen (20)
Boost PC performance: How more available memory can improve productivity

Boost PC performance: How more available memory can improve productivity
AWS Community Day CPH - Three problems of Terraform

AWS Community Day CPH - Three problems of Terraform
Strategies for Unlocking Knowledge Management in Microsoft 365 in the Copilot...

Strategies for Unlocking Knowledge Management in Microsoft 365 in the Copilot...
TrustArc Webinar - Unlock the Power of AI-Driven Data Discovery

TrustArc Webinar - Unlock the Power of AI-Driven Data Discovery
From Event to Action: Accelerate Your Decision Making with Real-Time Automation

From Event to Action: Accelerate Your Decision Making with Real-Time Automation
Automating Google Workspace (GWS) & more with Apps Script

Automating Google Workspace (GWS) & more with Apps Script
Bajaj Allianz Life Insurance Company - Insurer Innovation Award 2024

Bajaj Allianz Life Insurance Company - Insurer Innovation Award 2024
Scaling API-first – The story of a global engineering organization

Scaling API-first – The story of a global engineering organization
Strategies for Landing an Oracle DBA Job as a Fresher

Strategies for Landing an Oracle DBA Job as a Fresher
What Are The Drone Anti-jamming Systems Technology?

What Are The Drone Anti-jamming Systems Technology?
How to Troubleshoot Apps for the Modern Connected Worker

How to Troubleshoot Apps for the Modern Connected Worker
Apidays New York 2024 - Scaling API-first by Ian Reasor and Radu Cotescu, Adobe

Apidays New York 2024 - Scaling API-first by Ian Reasor and Radu Cotescu, Adobe
Advantages of Hiring UIUX Design Service Providers for Your Business

Advantages of Hiring UIUX Design Service Providers for Your Business
The 7 Things I Know About Cyber Security After 25 Years | April 2024

The 7 Things I Know About Cyber Security After 25 Years | April 2024
Exploring the Future Potential of AI-Enabled Smartphone Processors

Exploring the Future Potential of AI-Enabled Smartphone Processors
Block Armour Case Study
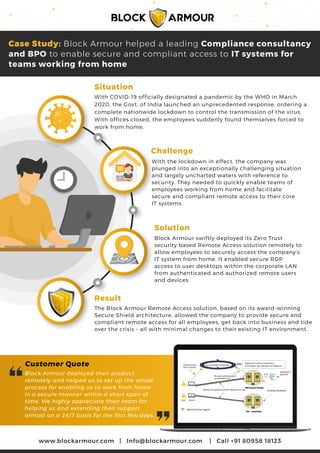
- 1. www.blockarmour.com | Info@blockarmour.com | Call +91 80958 18123 Situation With COVID-19 officially designated a pandemic by the WHO in March 2020, the Govt. of India launched an unprecedented response, ordering a complete nationwide lockdown to control the transmission of the virus. With offices closed, the employees suddenly found themselves forced to work from home. Challenge With the lockdown in effect, the company was plunged into an exceptionally challenging situation and largely uncharted waters with reference to security. They needed to quickly enable teams of employees working from home and facilitate secure and compliant remote access to their core IT systems. Solution Result Block Armour deployed their product remotely and helped us to set up the whole process for enabling us to work from home in a secure manner within a short span of time. We highly appreciate their team for helping us and extending their support almost on a 24/7 basis for the first few days. Customer Quote Case Study: Block Armour helped a leading Compliance consultancy and BPO to enable secure and compliant access to IT systems for teams working from home The Block Armour Remote Access solution, based on its award-winning Secure Shield architecture, allowed the company to provide secure and compliant remote access for all employees, get back into business and tide over the crisis – all with minimal changes to their existing IT environment. Block Armour swiftly deployed its Zero Trust security based Remote Access solution remotely to allow employees to securely access the company’s IT system from home. It enabled secure RDP access to user desktops within the corporate LAN from authenticated and authorized remote users and devices. MS Azure Cloud On - premise Invisible Systems Secure Shield Controller Digital ID, Policies, Dashboard, Immutable logs, Resilient Architecture - Block Armour Agent Authenticate User & Device Mutual Authentication to establish Trust Precise Encrypted Dynamic Network Access User Device CUSTOM APPS Application Agnostic
