Biznet guideline configuration mikrotik router
•
0 gefällt mir•681 views
This document provides instructions for configuring a Mikrotik router for a Biznet Metronet internet service. It involves 11 steps: 1) Connecting to the router and logging in, 2) Configuring PPPoE for the internet connection, 3) Setting the username and password, 4) Enabling NAT and masquerading, 5) Configuring a default route, 6) Creating an IP pool for the local network, 7) Setting up a DHCP server to assign IPs from the pool to devices, and 8) Configuring the DHCP server network settings.
Melden
Teilen
Melden
Teilen
Downloaden Sie, um offline zu lesen
Empfohlen
MikroTik Firewall : Securing your Router with Port Knocking

MikroTik Firewall : Securing your Router with Port KnockingAkbar Azwir, MM, PMP, PMI-SP, PSM I, CISSP
Weitere ähnliche Inhalte
Was ist angesagt?
MikroTik Firewall : Securing your Router with Port Knocking

MikroTik Firewall : Securing your Router with Port KnockingAkbar Azwir, MM, PMP, PMI-SP, PSM I, CISSP
Was ist angesagt? (20)
How to hack wireless internet connections using aircrack-ng

How to hack wireless internet connections using aircrack-ng
Konfigurasi Site-to-Site IPSec VPN Tunnel di Mikrotik menggunakan GNS3

Konfigurasi Site-to-Site IPSec VPN Tunnel di Mikrotik menggunakan GNS3
MikroTik Firewall : Securing your Router with Port Knocking

MikroTik Firewall : Securing your Router with Port Knocking
OWASP Melbourne - Introduction to iOS Application Penetration Testing

OWASP Melbourne - Introduction to iOS Application Penetration Testing
MikroTik Certified Network Associate (MTCNA) - Training Indonesia

MikroTik Certified Network Associate (MTCNA) - Training Indonesia
Developing rich SIP applications with SIPSIMPLE SDK

Developing rich SIP applications with SIPSIMPLE SDK
Pembahasan Solusi Soal UKK SMK TKJ Paket 4 Kurikulum 2013 Tahun 2020

Pembahasan Solusi Soal UKK SMK TKJ Paket 4 Kurikulum 2013 Tahun 2020
Cisco Firepower Next-Generation Firewall (NGFW).pdf

Cisco Firepower Next-Generation Firewall (NGFW).pdf
Ähnlich wie Biznet guideline configuration mikrotik router
Ähnlich wie Biznet guideline configuration mikrotik router (20)
Uccn1003 -may10_-_lect02b1_-_lan_basic_in_packet_tracer

Uccn1003 -may10_-_lect02b1_-_lan_basic_in_packet_tracer
Step by Step guide to set up a simple network in Packet Tracer

Step by Step guide to set up a simple network in Packet Tracer
Mehr von arimayawulantara
Mehr von arimayawulantara (20)
Atkearney soe digital transformation report present

Atkearney soe digital transformation report present
Kürzlich hochgeladen
Kürzlich hochgeladen (20)
Apidays New York 2024 - Scaling API-first by Ian Reasor and Radu Cotescu, Adobe

Apidays New York 2024 - Scaling API-first by Ian Reasor and Radu Cotescu, Adobe
Powerful Google developer tools for immediate impact! (2023-24 C)

Powerful Google developer tools for immediate impact! (2023-24 C)
From Event to Action: Accelerate Your Decision Making with Real-Time Automation

From Event to Action: Accelerate Your Decision Making with Real-Time Automation
[2024]Digital Global Overview Report 2024 Meltwater.pdf![[2024]Digital Global Overview Report 2024 Meltwater.pdf](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![[2024]Digital Global Overview Report 2024 Meltwater.pdf](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
[2024]Digital Global Overview Report 2024 Meltwater.pdf
Automating Google Workspace (GWS) & more with Apps Script

Automating Google Workspace (GWS) & more with Apps Script
The 7 Things I Know About Cyber Security After 25 Years | April 2024

The 7 Things I Know About Cyber Security After 25 Years | April 2024
2024: Domino Containers - The Next Step. News from the Domino Container commu...

2024: Domino Containers - The Next Step. News from the Domino Container commu...
Tata AIG General Insurance Company - Insurer Innovation Award 2024

Tata AIG General Insurance Company - Insurer Innovation Award 2024
Handwritten Text Recognition for manuscripts and early printed texts

Handwritten Text Recognition for manuscripts and early printed texts
Mastering MySQL Database Architecture: Deep Dive into MySQL Shell and MySQL R...

Mastering MySQL Database Architecture: Deep Dive into MySQL Shell and MySQL R...
HTML Injection Attacks: Impact and Mitigation Strategies

HTML Injection Attacks: Impact and Mitigation Strategies
TrustArc Webinar - Stay Ahead of US State Data Privacy Law Developments

TrustArc Webinar - Stay Ahead of US State Data Privacy Law Developments
Scaling API-first – The story of a global engineering organization

Scaling API-first – The story of a global engineering organization
ProductAnonymous-April2024-WinProductDiscovery-MelissaKlemke

ProductAnonymous-April2024-WinProductDiscovery-MelissaKlemke
Understanding Discord NSFW Servers A Guide for Responsible Users.pdf

Understanding Discord NSFW Servers A Guide for Responsible Users.pdf
Biznet guideline configuration mikrotik router
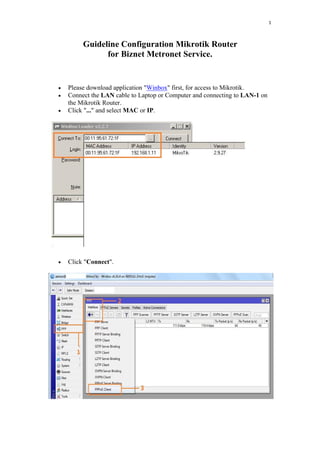
- 1. 1 Guideline Configuration Mikrotik Router for Biznet Metronet Service. Please download application "Winbox" first, for access to Mikrotik. Connect the LAN cable to Laptop or Computer and connecting to LAN-1 on the Mikrotik Router. Click "..." and select MAC or IP. Click "Connect".
- 2. 2 1. After successful login, please select menu "PPP". 2. Select tab "Interface" and click "+". 3. And then select "PPPoE Client". 1. Later will be show "New Interface", You can fill in the name of PPPoE that what you want. 2. Select "Interface" port that what you want, Usually most people using "Ether-1" or commonly called LAN-1.
- 3. 3 1. Next select tab "Dial Out". 2. For "Username" and "Password" use Biznet Customer ID and password on the form information provided at the time of installation. Note: * If forgot password, you can contact at 1500988 or email - customer_care@biznetnetworks.com. 3. Click "Apply" then "Ok".
- 4. 4 1. Next select menu "IP". 2. Select "Firewall". 1. Select tab "NAT. 2. Click "+".
- 5. 5 1. Select tab "General". 2. For Chain menu please change to "srcnat". 3. Out Interface "PPPoE Name that you create before". 4. Select tab "Action" , then change to "masquarade". 5. Click "Apply" then "Ok".
- 6. 6 1. Next select menu "IP". 2. Select "Routes".
- 7. 7 1. Select tab "Routes" , then click "+". 2. Dst. Address fill to "0.0.0.0/0" with PPPoE Name that you create before. 3. Click "Apply" then "Ok". Create DHCP IP for Private IP allocation for Internal Network.
- 8. 8 1. Select menu "IP". 2. And then select "Pool".
- 9. 9 1. Click "+". 2. Fill in the DHCP name that what you want. 3. And fill in the IP Address number that what you want. Usually for many IP addresses that using "192.168.1.2-192.168.1.200". 4. Click "Apply" then "Ok". 5. And then select menu "IP --> DHCP Server"
- 10. 10 1. Select Tab "DHCP" then click "+". 2. Fill in the DHCP Server name that what you want . 3. Interface menu please change to "Bridge1". 4. Address Pool you must select DHCP Pool Name that you create before. 5. Click "Apply" then "Ok".
- 11. 11 1. Click Tab "Networks". 2. Click "+". 3. Fill in the IP Address & Gateway according to the IP address you created earlier, If you follow the example above it is usually filled in IP Address "192.168.1.0/24" with Gateway "192.168.1.1". 4. Click "Apply" then "Ok".