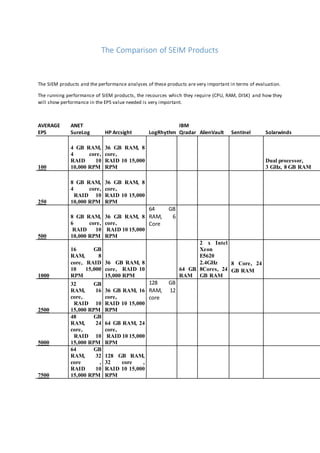
SIEM Surelog Arcsight Qradar LogRhythm Alienvault Solarwinds LEM Performance Comparison
- 1. The Comparison of SEIM Products The SIEM products and the performance analyses of these products are very important in terms of evaluation. The running performance of SIEM products, the resources which they require (CPU, RAM, DISK) and how they will show performance in the EPS value needed is very important. AVERAGE EPS ANET SureLog HP Arcsight LogRhythm IBM Qradar AlienVault Sentinel Solarwinds 100 4 GB RAM, 4 core, RAID 10 10,000 RPM 36 GB RAM, 8 core, RAID 10 15,000 RPM Dual processor, 3 GHz, 8 GB RAM 250 8 GB RAM, 4 core, RAID 10 10,000 RPM 36 GB RAM, 8 core, RAID 10 15,000 RPM 500 8 GB RAM, 6 core, RAID 10 10,000 RPM 36 GB RAM, 8 core, RAID 10 15,000 RPM 64 GB RAM, 6 Core 1000 16 GB RAM, 8 core, RAID 10 15,000 RPM 36 GB RAM, 8 core, RAID 10 15,000 RPM 64 GB RAM 2 x Intel Xeon E5620 2.4GHz 8Cores, 24 GB RAM 8 Core, 24 GB RAM 2500 32 GB RAM, 16 core, RAID 10 15,000 RPM 36 GB RAM, 16 core, RAID 10 15,000 RPM 128 GB RAM, 12 core 5000 48 GB RAM, 24 core, RAID 10 15,000 RPM 64 GB RAM, 24 core, RAID 10 15,000 RPM 7500 64 GB RAM, 32 core , RAID 10 15,000 RPM 128 GB RAM, 32 core , RAID 10 15,000 RPM
- 2. The relationship between the average EPS values and the maximum EPS values of the system in SIEM projects worked on and planning of system resources accordingly is a critical stage. How much EPS value the system reaches which will produce1000 EPS logs under normal conditions,in casean attack happens or a virus infects. If such cases occurs in the system, how SIEM system reacts. It is very critical planning all those cases. [1,6] HP Arcsight, ANET SureLog, IBM Qradar, LogRhthym, AlienVault, Novell Sentinel and Solarwinds LEM are compared with each other in this study. ANET SureLog has one other advantage over others that Log Management is also integrated in ANET SureLog while others are just SIEM. While the average EPS values are specified in some of the manufacturer tables, the max EPS values are specified in the others. The average EPS values are taken for each SIEM product in the table shown above. The some of the parameters which will affect the values in the table above [10,11] The number of total rules [12] The difficulty degree of the rules o Warn if user A can’t log into X server and caused failed authentication, and in two hours if that user A can’t log into the same X server. o Warn for a traffic whose destination port is 67, protocol is UDP, and destination IP is not in registered DHCP server list, occurs more than two times in one minute. o Warn if the servers are accessed out of hours. o Warn if more than 100 connections are established from different external IPs to the same destination IP in one minute. o Warn if 100 connections are established from the same external IP through different ports to the same destination IP in one minute. o Warn if the same user tries more than three failed logon attempts to the same machine in an hour. o Warn if the source or destination IP access attempt occurs to an IP address in the IP Reputation list. The correlation speed The Taxonomy features and the number of categories The type of correlation o A true correlation engine and in-memory correlation o ELK-based, the methods which are actually search based. This study is conducted over average EPS values. For reaching max EPS values, the resources should be expanded by 1,5-2 times. The accurate planning of the EPS values and the behavior of the system under high load depend fully upon these system resources. Also the other critical matter is that the system resource requirements of Log Management solutions and SEIM solutions are completely different from each other. For example in ANET SureLog solution [8], 8 Core CPU and 16 GB RAM are required for 1000 EPS. In case the correlation module is disabled, 4 Core CPU and 8 GB RAM are required for 1000 EPS. References: 1. http://www.slideshare.net/anetertugrul/log-ynetimi-sisteminizin-log-karp-karmadn-test-etmek-ister- misiniz 2. http://www8.hp.com/tr/tr/software-solutions/arcsight-esm-enterprise-security-management/tech- specs.html 3. http://www.solarwinds.com/log-event-manager.aspx#p_systemrequirements
- 3. 4. https://www.alienvault.com/docs/data-sheets/AV-USM.pdf 5. http://www- 01.ibm.com/support/knowledgecenter/SS42VS_7.2.4/com.ibm.qradar.doc_7.2.4/c_hwg_3105_allone _base.html 6. http://www.slideshare.net/anetertugrul/normal-artlarda-200-250-eps-logum-anca-oluyor-yksek- performansa-neden-ihtiya-duyaym 7. http://www.slideshare.net/anetertugrul/log-yonetiminde-cihaz-sayilari-ile-eps-degerleri-arasindaki- iliski 8. http://www.slideshare.net/anetertugrul/surelog-international-edition 9. https://www.netiq.com/documentation/sentinel70/s701_install/data/btmckgy.html#bwwvoik 10. http://blogs.gartner.com/anton-chuvakin/2014/06/17/on-siem-tool-and-operation-metrics/ 11. https://www.sans.org/reading-room/whitepapers/analyst/benchmarking-security-information-event- management-siem-34755 12. http://www.slideshare.net/NOVL/how-to-architect-a-novell-sentinel-implementation
