Four Network Security Challenges for the Cloud Generation
•
1 gefällt mir•404 views
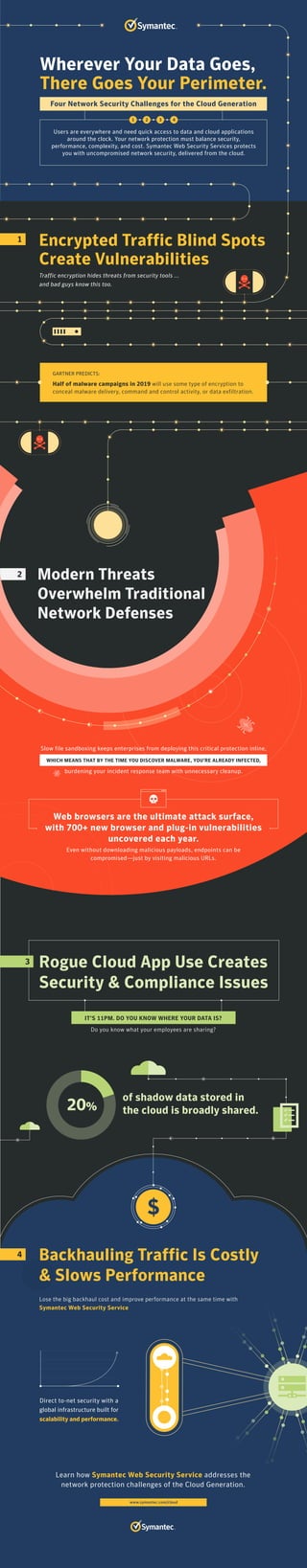
Users are accessing cloud applications from anywhere at any time, which has expanded the attack surface and made network defenses more difficult. Traditional network protections are overwhelmed by modern threats like encrypted web traffic and 700+ new browser vulnerabilities each year. Half of malware in 2019 will use encryption for delivery, command and control, or data exfiltration, hiding threats from security tools. Symantec Web Security Services provides cloud-based network security that balances security, performance, complexity and cost to address these challenges.
Melden
Teilen
Melden
Teilen
Downloaden Sie, um offline zu lesen
Empfohlen
Empfohlen
A profile is an extremely sensitive optional configuration file which allows to re-define different system functionality parameters such as mobile carrier settings, Mobile Device Management (MDM) settings and networking settings. Through social engineering techniques such as email phishing or a fake URL, an attacker can convince a user to install a malicious profile and compromise the device settings to silently route network traffic from the device to a remote proxy over SSL using a self-signed certificate.
The impact:
Once the attacker has re-routed all traffic from the mobile device to their own server, they can begin to install other malicious apps and decrypt SSL communications.iOS Threats - Malicious Configuration Profiles, Threat, Detection & Mitigation

iOS Threats - Malicious Configuration Profiles, Threat, Detection & MitigationLacoon Mobile Security
Weitere ähnliche Inhalte
Was ist angesagt?
A profile is an extremely sensitive optional configuration file which allows to re-define different system functionality parameters such as mobile carrier settings, Mobile Device Management (MDM) settings and networking settings. Through social engineering techniques such as email phishing or a fake URL, an attacker can convince a user to install a malicious profile and compromise the device settings to silently route network traffic from the device to a remote proxy over SSL using a self-signed certificate.
The impact:
Once the attacker has re-routed all traffic from the mobile device to their own server, they can begin to install other malicious apps and decrypt SSL communications.iOS Threats - Malicious Configuration Profiles, Threat, Detection & Mitigation

iOS Threats - Malicious Configuration Profiles, Threat, Detection & MitigationLacoon Mobile Security
Was ist angesagt? (20)
IT security in 2021: Why Ransomware Is Still The Biggest Threat

IT security in 2021: Why Ransomware Is Still The Biggest Threat
Re solution - corona virus cyber security infographic

Re solution - corona virus cyber security infographic
What is CryptoLocker and How Can I Protect My Business From It?

What is CryptoLocker and How Can I Protect My Business From It?
NormShield Cyber Threat & Vulnerability Orchestration Overview

NormShield Cyber Threat & Vulnerability Orchestration Overview
Ciberseguridad: Enemigos o defraudadores (MAGISTRAL)

Ciberseguridad: Enemigos o defraudadores (MAGISTRAL)
iOS Threats - Malicious Configuration Profiles, Threat, Detection & Mitigation

iOS Threats - Malicious Configuration Profiles, Threat, Detection & Mitigation
Ähnlich wie Four Network Security Challenges for the Cloud Generation
Ähnlich wie Four Network Security Challenges for the Cloud Generation (20)
Watch Guard Reputation Enabled Defense (White Paper)Dna

Watch Guard Reputation Enabled Defense (White Paper)Dna
Cloud Application Security Best Practices To follow.pdf

Cloud Application Security Best Practices To follow.pdf
Cloud Application Security Best Practices To follow.pdf

Cloud Application Security Best Practices To follow.pdf
MIST Effective Masquerade Attack Detection in the Cloud

MIST Effective Masquerade Attack Detection in the Cloud
The Notorious 9 Cloud Computing Threats - CSA Congress, San Jose

The Notorious 9 Cloud Computing Threats - CSA Congress, San Jose
Disrupting the Malware Kill Chain - What's New from Palo Alto Networks.

Disrupting the Malware Kill Chain - What's New from Palo Alto Networks.
Mehr von AboutSSL
Mehr von AboutSSL (12)
Difference Between Digital Signature vs Digital Certificate

Difference Between Digital Signature vs Digital Certificate
How to Install SSL Certificate in Red Hat Linux Apache Web Server

How to Install SSL Certificate in Red Hat Linux Apache Web Server
How to Move SSL Certificate from One Windows Server to Another

How to Move SSL Certificate from One Windows Server to Another
Installation Instructions for Microsoft Exchange 2010 Server

Installation Instructions for Microsoft Exchange 2010 Server
Wildcard and SAN (Multi-Domain) Certificates – What’s the Difference?

Wildcard and SAN (Multi-Domain) Certificates – What’s the Difference?
Which are the best Organization Validation SSL Certificates? 

Which are the best Organization Validation SSL Certificates?
Top 7 Cheap Multi-Domain SSL Certificate Providers

Top 7 Cheap Multi-Domain SSL Certificate Providers
A List of Affordable SSL Certificate Providers 2016

A List of Affordable SSL Certificate Providers 2016
Kürzlich hochgeladen
Kürzlich hochgeladen (20)
Web Form Automation for Bonterra Impact Management (fka Social Solutions Apri...

Web Form Automation for Bonterra Impact Management (fka Social Solutions Apri...
DEV meet-up UiPath Document Understanding May 7 2024 Amsterdam

DEV meet-up UiPath Document Understanding May 7 2024 Amsterdam
WSO2's API Vision: Unifying Control, Empowering Developers

WSO2's API Vision: Unifying Control, Empowering Developers
Elevate Developer Efficiency & build GenAI Application with Amazon Q

Elevate Developer Efficiency & build GenAI Application with Amazon Q
Polkadot JAM Slides - Token2049 - By Dr. Gavin Wood

Polkadot JAM Slides - Token2049 - By Dr. Gavin Wood
Rising Above_ Dubai Floods and the Fortitude of Dubai International Airport.pdf

Rising Above_ Dubai Floods and the Fortitude of Dubai International Airport.pdf
TrustArc Webinar - Unlock the Power of AI-Driven Data Discovery

TrustArc Webinar - Unlock the Power of AI-Driven Data Discovery
Introduction to Multilingual Retrieval Augmented Generation (RAG)

Introduction to Multilingual Retrieval Augmented Generation (RAG)
Cloud Frontiers: A Deep Dive into Serverless Spatial Data and FME

Cloud Frontiers: A Deep Dive into Serverless Spatial Data and FME
Apidays New York 2024 - Scaling API-first by Ian Reasor and Radu Cotescu, Adobe

Apidays New York 2024 - Scaling API-first by Ian Reasor and Radu Cotescu, Adobe
Finding Java's Hidden Performance Traps @ DevoxxUK 2024

Finding Java's Hidden Performance Traps @ DevoxxUK 2024
Strategize a Smooth Tenant-to-tenant Migration and Copilot Takeoff

Strategize a Smooth Tenant-to-tenant Migration and Copilot Takeoff
Biography Of Angeliki Cooney | Senior Vice President Life Sciences | Albany, ...

Biography Of Angeliki Cooney | Senior Vice President Life Sciences | Albany, ...
Vector Search -An Introduction in Oracle Database 23ai.pptx

Vector Search -An Introduction in Oracle Database 23ai.pptx
EMPOWERMENT TECHNOLOGY GRADE 11 QUARTER 2 REVIEWER

EMPOWERMENT TECHNOLOGY GRADE 11 QUARTER 2 REVIEWER
Four Network Security Challenges for the Cloud Generation
- 1. 4 Rogue Cloud App Use Creates Security & Compliance Issues of shadow data stored in the cloud is broadly shared. IT’S 11PM. DO YOU KNOW WHERE YOUR DATA IS? Do you know what your employees are sharing? 3 20% Modern Threats Overwhelm Traditional Network Defenses 2 Web browsers are the ultimate attack surface, with 700+ new browser and plug-in vulnerabilities uncovered each year. Even without downloading malicious payloads, endpoints can be compromised—just by visiting malicious URLs. Wherever Your Data Goes, There Goes Your Perimeter. Users are everywhere and need quick access to data and cloud applications around the clock. Your network protection must balance security, performance, complexity, and cost. Symantec Web Security Services protects you with uncompromised network security, delivered from the cloud. 1 GARTNER PREDICTS: Half of malware campaigns in 2019 will use some type of encryption to conceal malware delivery, command and control activity, or data exfiltration. Four Network Security Challenges for the Cloud Generation 1 2 3 4 Traffic encryption hides threats from security tools ... and bad guys know this too. Encrypted Traffic Blind Spots Create Vulnerabilities Lose the big backhaul cost and improve performance at the same time with Symantec Web Security Service Backhauling Traffic Is Costly & Slows Performance www.symantec.com/cloud Learn how Symantec Web Security Service addresses the network protection challenges of the Cloud Generation. Direct to-net security with a global infrastructure built for scalability and performance. Slow file sandboxing keeps enterprises from deploying this critical protection inline, WHICH MEANS THAT BY THE TIME YOU DISCOVER MALWARE, YOU’RE ALREADY INFECTED, burdening your incident response team with unnecessary cleanup.
