What is a Rainbow Table?
•Als PPTX, PDF herunterladen•
2 gefällt mir•6,008 views
this presentation introduces you an advanced way of decryption of data
Melden
Teilen
Melden
Teilen
Weitere ähnliche Inhalte
Was ist angesagt?
Was ist angesagt? (20)
substitution and transposition techniques_ppt.pptx

substitution and transposition techniques_ppt.pptx
Andere mochten auch
Andere mochten auch (11)
Password Storage And Attacking In PHP - PHP Argentina

Password Storage And Attacking In PHP - PHP Argentina
Mehr von Vahid Saffarian
Mehr von Vahid Saffarian (12)
Kürzlich hochgeladen
Kürzlich hochgeladen (20)
DevoxxFR 2024 Reproducible Builds with Apache Maven

DevoxxFR 2024 Reproducible Builds with Apache Maven
"LLMs for Python Engineers: Advanced Data Analysis and Semantic Kernel",Oleks...

"LLMs for Python Engineers: Advanced Data Analysis and Semantic Kernel",Oleks...
"Debugging python applications inside k8s environment", Andrii Soldatenko

"Debugging python applications inside k8s environment", Andrii Soldatenko
Vector Databases 101 - An introduction to the world of Vector Databases

Vector Databases 101 - An introduction to the world of Vector Databases
DevEX - reference for building teams, processes, and platforms

DevEX - reference for building teams, processes, and platforms
My INSURER PTE LTD - Insurtech Innovation Award 2024

My INSURER PTE LTD - Insurtech Innovation Award 2024
Designing IA for AI - Information Architecture Conference 2024

Designing IA for AI - Information Architecture Conference 2024
Transcript: New from BookNet Canada for 2024: BNC CataList - Tech Forum 2024

Transcript: New from BookNet Canada for 2024: BNC CataList - Tech Forum 2024
Beyond Boundaries: Leveraging No-Code Solutions for Industry Innovation

Beyond Boundaries: Leveraging No-Code Solutions for Industry Innovation
Nell’iperspazio con Rocket: il Framework Web di Rust!

Nell’iperspazio con Rocket: il Framework Web di Rust!
New from BookNet Canada for 2024: BNC CataList - Tech Forum 2024

New from BookNet Canada for 2024: BNC CataList - Tech Forum 2024
Tampa BSides - Chef's Tour of Microsoft Security Adoption Framework (SAF)

Tampa BSides - Chef's Tour of Microsoft Security Adoption Framework (SAF)
Powerpoint exploring the locations used in television show Time Clash

Powerpoint exploring the locations used in television show Time Clash
Developer Data Modeling Mistakes: From Postgres to NoSQL

Developer Data Modeling Mistakes: From Postgres to NoSQL
What is a Rainbow Table?
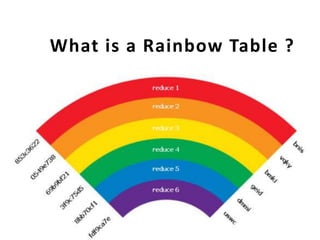
- 1. What is a Rainbow Table ?
- 2. A rainbow table is a precomputed table for reversing cryptographic hash functions, usually for cracking password hashes.
- 3. Tables are usually used in recovering a plaintext password up to a certain length consisting of a limited set of characters.
- 4. It is a practical example of a space/time trade- off, using more computer processing time at the cost of less storage when calculating a hash on every attempt, or less processing time and more storage when compared to a simple lookup table with one entry per hash.
- 6. Use of a key derivation function that employs a salt makes this attack infeasible.
- 7. Rainbow tables are an application of an earlier, simpler algorithm by Martin Hellman
