Unisys Security Insights Infographic: Australia - Data Breaches Most Likely by Industry
•
1 gefällt mir•1,181 views
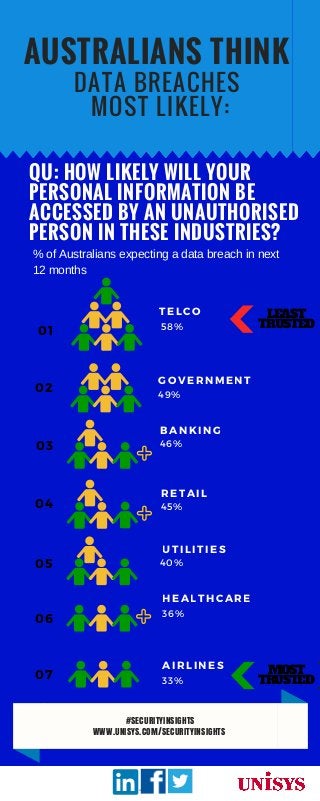
Consumer viewpoints on security: Industry trust The Unisys Security Insights research reveals what industries the general public perceives is most likely to suffer a data breach. View full report: http://outreach.unisys.com/LP=1162?src=SS
Melden
Teilen
Melden
Teilen
Downloaden Sie, um offline zu lesen
Empfohlen
Weitere ähnliche Inhalte
Mehr von Unisys Corporation
Mehr von Unisys Corporation (20)
Unisys Integrated Medical Device Management - Executive Brief

Unisys Integrated Medical Device Management - Executive Brief
SURVEY RESULTS: ACCELERATING INNOVATION AND THE DIGITAL JOURNEY - INFOGRAPHIC

SURVEY RESULTS: ACCELERATING INNOVATION AND THE DIGITAL JOURNEY - INFOGRAPHIC
Stealth Secures Along Every Step of Your Journey Infographic

Stealth Secures Along Every Step of Your Journey Infographic
DIE NEUE DIGITALE INFRASTRUKTUR FÜR DIGITALE MITARBEITER DER NÄCHSTEN GENERAT...

DIE NEUE DIGITALE INFRASTRUKTUR FÜR DIGITALE MITARBEITER DER NÄCHSTEN GENERAT...
STEHEN DIE ENDBENUTZER DER GENERATION „DIGITAL“FÜR DAS ENDE VON IT-TRANSPAREN...

STEHEN DIE ENDBENUTZER DER GENERATION „DIGITAL“FÜR DAS ENDE VON IT-TRANSPAREN...
DIE GENERATION DIGITAL UND DIE IT-LÜCKE IN UNTERNEHMEN.

DIE GENERATION DIGITAL UND DIE IT-LÜCKE IN UNTERNEHMEN.
Kürzlich hochgeladen
Kürzlich hochgeladen (20)
Exploring the Future Potential of AI-Enabled Smartphone Processors

Exploring the Future Potential of AI-Enabled Smartphone Processors
The 7 Things I Know About Cyber Security After 25 Years | April 2024

The 7 Things I Know About Cyber Security After 25 Years | April 2024
Understanding Discord NSFW Servers A Guide for Responsible Users.pdf

Understanding Discord NSFW Servers A Guide for Responsible Users.pdf
Strategies for Unlocking Knowledge Management in Microsoft 365 in the Copilot...

Strategies for Unlocking Knowledge Management in Microsoft 365 in the Copilot...
Tata AIG General Insurance Company - Insurer Innovation Award 2024

Tata AIG General Insurance Company - Insurer Innovation Award 2024
2024: Domino Containers - The Next Step. News from the Domino Container commu...

2024: Domino Containers - The Next Step. News from the Domino Container commu...
Powerful Google developer tools for immediate impact! (2023-24 C)

Powerful Google developer tools for immediate impact! (2023-24 C)
What Are The Drone Anti-jamming Systems Technology?

What Are The Drone Anti-jamming Systems Technology?
Axa Assurance Maroc - Insurer Innovation Award 2024

Axa Assurance Maroc - Insurer Innovation Award 2024
08448380779 Call Girls In Diplomatic Enclave Women Seeking Men

08448380779 Call Girls In Diplomatic Enclave Women Seeking Men
Boost Fertility New Invention Ups Success Rates.pdf

Boost Fertility New Invention Ups Success Rates.pdf
The Role of Taxonomy and Ontology in Semantic Layers - Heather Hedden.pdf

The Role of Taxonomy and Ontology in Semantic Layers - Heather Hedden.pdf
Workshop - Best of Both Worlds_ Combine KG and Vector search for enhanced R...

Workshop - Best of Both Worlds_ Combine KG and Vector search for enhanced R...
From Event to Action: Accelerate Your Decision Making with Real-Time Automation

From Event to Action: Accelerate Your Decision Making with Real-Time Automation
How to Troubleshoot Apps for the Modern Connected Worker

How to Troubleshoot Apps for the Modern Connected Worker
Unisys Security Insights Infographic: Australia - Data Breaches Most Likely by Industry
- 1. DATA BREACHES MOST LIKELY: AUSTRALIANS THINK 01 02 03 04 05 TELCO 58% GOVERNMENT 49% BANKING 46% RETAIL 45% UTILITIES 40% QU: HOW LIKELY WILL YOUR PERSONAL INFORMATION BE ACCESSED BY AN UNAUTHORISED PERSON IN THESE INDUSTRIES? 06 07 HEALTHCARE 36% AIRLINES 33% LEAST TRUSTED MOST TRUSTED #SECURITYINSIGHTS WWW.UNISYS.COM/SECURITYINSIGHTS % of Australians expecting a data breach in next 12 months
