ThreatMetrix Fraud Network Presentation
•Als PPTX, PDF herunterladen•
3 gefällt mir•1,867 views
Melden
Teilen
Melden
Teilen
Empfohlen
Weitere ähnliche Inhalte
Was ist angesagt?
Was ist angesagt? (11)
securing-consumer-portals-consumer-access-management-as-business-driver-and-p...

securing-consumer-portals-consumer-access-management-as-business-driver-and-p...
Weak Links: Cyber Attacks in the News & How to Protect Your Assets

Weak Links: Cyber Attacks in the News & How to Protect Your Assets
Andere mochten auch
Andere mochten auch (9)
Threatmetrix rスレットメトリックス・グローバル共有インテリジェンスによる VISA 顧客認証サービス(VCAS)のサポート

Threatmetrix rスレットメトリックス・グローバル共有インテリジェンスによる VISA 顧客認証サービス(VCAS)のサポート
Threatmetrix スレットメトリックス・グローバル共有インテリジェンスによる VISA 顧客認証サービス(VCAS)のサポート

Threatmetrix スレットメトリックス・グローバル共有インテリジェンスによる VISA 顧客認証サービス(VCAS)のサポート
AWS Enterprise Day | Securing your Web Applications in the Cloud

AWS Enterprise Day | Securing your Web Applications in the Cloud
Ähnlich wie ThreatMetrix Fraud Network Presentation
10 Essential Strategies to Safeguard Your Business from Credit Card Fraud 1.pdf

10 Essential Strategies to Safeguard Your Business from Credit Card Fraud 1.pdfMerchantech - Payment Processing Services
Ähnlich wie ThreatMetrix Fraud Network Presentation (20)
Verified Stripe Account Buy Verified Stripe Account

Verified Stripe Account Buy Verified Stripe Account
Trading Online – Getting started and how to grow your business

Trading Online – Getting started and how to grow your business
Ultimate Guide on Card Not Present (CNP) Fraud.pptx

Ultimate Guide on Card Not Present (CNP) Fraud.pptx
3 Ways Fraudsters Compromise AP Security and Controls and How You Can Mitigat...

3 Ways Fraudsters Compromise AP Security and Controls and How You Can Mitigat...
10 Essential Strategies to Safeguard Your Business from Credit Card Fraud 1.pdf

10 Essential Strategies to Safeguard Your Business from Credit Card Fraud 1.pdf
Kürzlich hochgeladen
Kürzlich hochgeladen (20)
How to Troubleshoot Apps for the Modern Connected Worker

How to Troubleshoot Apps for the Modern Connected Worker
Connector Corner: Accelerate revenue generation using UiPath API-centric busi...

Connector Corner: Accelerate revenue generation using UiPath API-centric busi...
Boost Fertility New Invention Ups Success Rates.pdf

Boost Fertility New Invention Ups Success Rates.pdf
Navigating the Deluge_ Dubai Floods and the Resilience of Dubai International...

Navigating the Deluge_ Dubai Floods and the Resilience of Dubai International...
EMPOWERMENT TECHNOLOGY GRADE 11 QUARTER 2 REVIEWER

EMPOWERMENT TECHNOLOGY GRADE 11 QUARTER 2 REVIEWER
2024: Domino Containers - The Next Step. News from the Domino Container commu...

2024: Domino Containers - The Next Step. News from the Domino Container commu...
Apidays New York 2024 - Accelerating FinTech Innovation by Vasa Krishnan, Fin...

Apidays New York 2024 - Accelerating FinTech Innovation by Vasa Krishnan, Fin...
Apidays New York 2024 - The value of a flexible API Management solution for O...

Apidays New York 2024 - The value of a flexible API Management solution for O...
TrustArc Webinar - Unlock the Power of AI-Driven Data Discovery

TrustArc Webinar - Unlock the Power of AI-Driven Data Discovery
ProductAnonymous-April2024-WinProductDiscovery-MelissaKlemke

ProductAnonymous-April2024-WinProductDiscovery-MelissaKlemke
ICT role in 21st century education and its challenges

ICT role in 21st century education and its challenges
"I see eyes in my soup": How Delivery Hero implemented the safety system for ...

"I see eyes in my soup": How Delivery Hero implemented the safety system for ...
Cloud Frontiers: A Deep Dive into Serverless Spatial Data and FME

Cloud Frontiers: A Deep Dive into Serverless Spatial Data and FME
Strategize a Smooth Tenant-to-tenant Migration and Copilot Takeoff

Strategize a Smooth Tenant-to-tenant Migration and Copilot Takeoff
Modular Monolith - a Practical Alternative to Microservices @ Devoxx UK 2024

Modular Monolith - a Practical Alternative to Microservices @ Devoxx UK 2024
ThreatMetrix Fraud Network Presentation
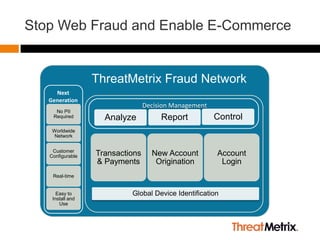
- 1. Stop Web Fraud and Enable E-Commerce ThreatMetrix Fraud Network Next Generation
- 2. Detect Stolen and Hijacked Credentials Transactions New Accounts Logins Identity Velocity Device Anomaly Access Anomaly
- 3. Authenticate New and Returning Customers Transactions New Accounts Logins
- 4. ThreatMetrix Customer Problems Transactions New Accounts Login Account Hijack Prevention Compromised Device Detection Synthetic and Stolen Identity Protection Chargeback and Loss Prevention Financial Services Gaming & Currency CPA & Alt payments Social Networks Merchants & Online Services Fraud Management is Strategic to Business Operations
- 9. Out of Band & Two Factor Authentication inconvenient or impracticalIntelligence trapped within departments & organizations
- 16. Protect BrandNon-invasive, Real-time, Enterprise & Global Intelligence, with no PII Leakage
- 17. ThreatMetrix Fraud Network Transactions New Accounts Logins Secure Web API: Transaction Details & AnonymizedCredentials SaaS Portal (Analyze, Report, Control) Real-time Rules Engine with Behavior & Pattern Matching Transaction Intelligence Network Global Device Identification
- 20. Proxy Piercing & Botnet detection
- 22. High speed matching/storage framework on commodity hardware
- 23. Packet Signature Detection combined with context data
- 24. Scalable, secure Inter-process communication platform
