Palo Alto Networks Portfolio & Strategy Overview 2019
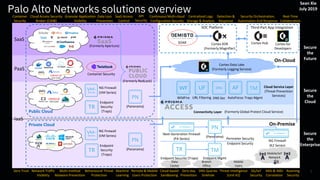
- 1. On-Premise On-Cloud Palo Alto Networks solutions overview 1 Next-Generation Firewall (PA Series) SaaS PaaS Private Cloud (Formerly Aperture) Cortex XDR (Formerly Magnifier) Cortex Data Lake (Formerly Logging Service) Endpoint Security (Traps) Public Cloud PN (Panorama) SOAR IaaS PN (Panorama) NG Firewall (VM Series) Cloud Service Layer (Threat Prevention Services) DNS SecURL FilteringWildFire AutoFocus TM Traps Mgmt Container Security (Formerly RedLock) Endpoint Security (Traps) NG Firewall (VM Series) Endpoint Security (Traps) Cortex Hub Cortex for Developers Third-Part App Integration Mobile/IoT Network SOC Platform NG Firewall (K2 Series) Perimeter Security Endpoint Security Data Center Branch Office Mobile Users (Formerly Global Protect Cloud Service)Connectivity Layer PN (Panorama) TM Endpoint Mgmt Behavioural Threat Protection Zero Trust Remote & Mobile Users Protection Data Loss Prevention Cloud Access Security Broker (CASB) Container Security SaaS Access Control 5G/IoT Security Centralized Logs Storage & Analysis Continuous Multi-cloud Configuration Security API Security IMSI & IMEI Correlation Cloud-based Sandboxing Zero-day Prevention Threat Intelligence (Unit 42) Machine Learning Detection & Response Real-Time Collaboration Security Orchestration, Automation And Response Secure the Enterprise Secure the Future Secure the Cloud Multi-method Malware Prevention Roaming Security Granular Application Visibility Network Traffic Visibility DNS Queries Sinkhole Sean Xie July 2019
- 2. Data Centre perimeter security – PA-Series NG firewall 2 Next-Gen FW vs. Traditional FW Next-Gen FW vs. UTM Next-Gen Firewall Traditional Firewall Application Awareness Identify application inside the port Only check IP address and port number Deep Packet Inspection Check payload Multi-functional (FW + IPS + AV + URL) Check packet header OSI Layer Layer 3 to 7 Layer 3 to 4 Next-Gen Firewall UTM Architecture Single-pass architecture Sequential inspection Performance Higher throughput rating Lower throughput rating Target Users From low-end to high- end enterprise Small and medium-sized businesses Palo Alto Next-Generation Firewall Key Differentiators App-ID User-ID Content-ID Scan the content Identify the user Identify the application Single-pass Architecture Applipedia
- 3. Auto scaling VM-Series NG firewall for AWS 3 INTERNET us-west-1 us-west-1cus-west-1a Subnet 10.10.51.0/24 Subnet 10.10.52.0/24 Web 2Web 1 Subnet 10.10.1.0/24 Subnet 10.10.2.0/24 Application Load Balancer ALB 1 per VPC Cloud Infrastructure Web us-west-1a Internet Gateway Router Network Load Balancer NLB AWS Region Availability Zone Subnet us-west-1 subnet x.x.x.x VPC VM-Series WebInstance Application Load Balancer ALB VM- Series App 2App 1 Web ASG App ASG AWS LambdaAWS CloudWatch VM- Series VM- Series Web 3 Network Load Balancer NLB 1 per Auto Scaling Group Web 4 VM- Series Auto Scaling PAN OS API App 3 Firewall ASG VM- Series Alarm Sessions Sessions AWS CloudFormation Template (CFT) AWS API Firewall Metrics
