Cryptography unit2.pptx
•Als PPTX, PDF herunterladen•
0 gefällt mir•12 views
Cryptography unit2
Melden
Teilen
Melden
Teilen
Empfohlen
Empfohlen
Welcome to the April edition of WIPAC Monthly, the magazine brought to you by Water Industry Process Automation & Control.
In this month's edition, along with the latest news from the industry we have articles on:
The use of artificial intelligence and self-service platforms to improve water sustainability
A feature article on measuring wastewater spills
An article on the National Underground Asset Register
Have a good month,
OliverWater Industry Process Automation & Control Monthly - April 2024

Water Industry Process Automation & Control Monthly - April 2024Water Industry Process Automation & Control
Weitere ähnliche Inhalte
Ähnlich wie Cryptography unit2.pptx
Ähnlich wie Cryptography unit2.pptx (20)
IMPLEMENTATION OF AES AS A CUSTOM HARDWARE USING NIOS II PROCESSOR

IMPLEMENTATION OF AES AS A CUSTOM HARDWARE USING NIOS II PROCESSOR
A VHDL Implemetation of the Advanced Encryption Standard-Rijndael.pdf

A VHDL Implemetation of the Advanced Encryption Standard-Rijndael.pdf
Security Analysis of AES and Enhancing its Security by Modifying S-Box with a...

Security Analysis of AES and Enhancing its Security by Modifying S-Box with a...
Enhanced Advanced Encryption Standard (E-AES): using ESET

Enhanced Advanced Encryption Standard (E-AES): using ESET
IJCER (www.ijceronline.com) International Journal of computational Engineerin...

IJCER (www.ijceronline.com) International Journal of computational Engineerin...
IJCER (www.ijceronline.com) International Journal of computational Engineerin...

IJCER (www.ijceronline.com) International Journal of computational Engineerin...
An Efficient VLSI Design of AES Cryptography Based on DNA TRNG Design

An Efficient VLSI Design of AES Cryptography Based on DNA TRNG Design
Kürzlich hochgeladen
Welcome to the April edition of WIPAC Monthly, the magazine brought to you by Water Industry Process Automation & Control.
In this month's edition, along with the latest news from the industry we have articles on:
The use of artificial intelligence and self-service platforms to improve water sustainability
A feature article on measuring wastewater spills
An article on the National Underground Asset Register
Have a good month,
OliverWater Industry Process Automation & Control Monthly - April 2024

Water Industry Process Automation & Control Monthly - April 2024Water Industry Process Automation & Control
Call Girl Aurangabad Indira Call Now: 8617697112 Aurangabad Escorts Booking Contact Details WhatsApp Chat: +91-8617697112 Aurangabad Escort Service includes providing maximum physical satisfaction to their clients as well as engaging conversation that keeps your time enjoyable and entertaining. Plus they look fabulously elegant; making an impressionable. Independent Escorts Aurangabad understands the value of confidentiality and discretion - they will go the extra mile to meet your needs. Simply contact them via text messaging or through their online profiles; they'd be more than delighted to accommodate any request or arrange a romantic date or fun-filled night together. We provide –(INDIRA) Call Girl Aurangabad Call Now 8617697112 Aurangabad Escorts 24x7

(INDIRA) Call Girl Aurangabad Call Now 8617697112 Aurangabad Escorts 24x7Call Girls in Nagpur High Profile Call Girls
Top Rated Pune Call Girls Budhwar Peth ⟟ 6297143586 ⟟ Call Me For Genuine Sex Service At Affordable Rate
Booking Contact Details
WhatsApp Chat: +91-6297143586
pune Escort Service includes providing maximum physical satisfaction to their clients as well as engaging conversation that keeps your time enjoyable and entertaining. Plus they look fabulously elegant; making an impressionable.
Independent Escorts pune understands the value of confidentiality and discretion - they will go the extra mile to meet your needs. Simply contact them via text messaging or through their online profiles; they'd be more than delighted to accommodate any request or arrange a romantic date or fun-filled night together.
We provide -
01-may-2024(v.n)
Top Rated Pune Call Girls Budhwar Peth ⟟ 6297143586 ⟟ Call Me For Genuine Se...

Top Rated Pune Call Girls Budhwar Peth ⟟ 6297143586 ⟟ Call Me For Genuine Se...Call Girls in Nagpur High Profile
Booking open Available Pune Call Girls Pargaon 6297143586 Call Hot Indian Girls Waiting For You To Fuck
Booking Contact Details
WhatsApp Chat: +91-6297143586
pune Escort Service includes providing maximum physical satisfaction to their clients as well as engaging conversation that keeps your time enjoyable and entertaining. Plus they look fabulously elegant; making an impressionable.
Independent Escorts pune understands the value of confidentiality and discretion - they will go the extra mile to meet your needs. Simply contact them via text messaging or through their online profiles; they'd be more than delighted to accommodate any request or arrange a romantic date or fun-filled night together.
We provide -
01-may-2024(v.n)
Booking open Available Pune Call Girls Pargaon 6297143586 Call Hot Indian Gi...

Booking open Available Pune Call Girls Pargaon 6297143586 Call Hot Indian Gi...Call Girls in Nagpur High Profile
Kürzlich hochgeladen (20)
Roadmap to Membership of RICS - Pathways and Routes

Roadmap to Membership of RICS - Pathways and Routes
Water Industry Process Automation & Control Monthly - April 2024

Water Industry Process Automation & Control Monthly - April 2024
(INDIRA) Call Girl Aurangabad Call Now 8617697112 Aurangabad Escorts 24x7

(INDIRA) Call Girl Aurangabad Call Now 8617697112 Aurangabad Escorts 24x7
The Most Attractive Pune Call Girls Budhwar Peth 8250192130 Will You Miss Thi...

The Most Attractive Pune Call Girls Budhwar Peth 8250192130 Will You Miss Thi...
Structural Analysis and Design of Foundations: A Comprehensive Handbook for S...

Structural Analysis and Design of Foundations: A Comprehensive Handbook for S...
VIP Call Girls Ankleshwar 7001035870 Whatsapp Number, 24/07 Booking

VIP Call Girls Ankleshwar 7001035870 Whatsapp Number, 24/07 Booking
Top Rated Pune Call Girls Budhwar Peth ⟟ 6297143586 ⟟ Call Me For Genuine Se...

Top Rated Pune Call Girls Budhwar Peth ⟟ 6297143586 ⟟ Call Me For Genuine Se...
Booking open Available Pune Call Girls Pargaon 6297143586 Call Hot Indian Gi...

Booking open Available Pune Call Girls Pargaon 6297143586 Call Hot Indian Gi...
Call for Papers - International Journal of Intelligent Systems and Applicatio...

Call for Papers - International Journal of Intelligent Systems and Applicatio...
Intze Overhead Water Tank Design by Working Stress - IS Method.pdf

Intze Overhead Water Tank Design by Working Stress - IS Method.pdf
BSides Seattle 2024 - Stopping Ethan Hunt From Taking Your Data.pptx

BSides Seattle 2024 - Stopping Ethan Hunt From Taking Your Data.pptx
Cryptography unit2.pptx
- 1. Unit 2:Symmetric key AlgorithmS
- 2. Unit 2:Symmetric key AlgorithmS
- 3. Unit 2:Symmetric key AlgorithmS
- 4. Unit 2:Symmetric key AlgorithmS
- 5. Unit 2:Symmetric key AlgorithmS Block Cipher principles: 1. Number of Rounds – The number of Rounds is regularly considered in design criteria, it just reflects the number of rounds to be suitable for an algorithm to make it more complex, in DES we have 16 rounds ensuring it to be more secure while in AES we have 10 rounds which makes it more secure. 2. Design of function F –The core part of the Feistel Block cipher structure is the Round Function. The complexity of cryptanalysis can be derived from the Round function i.e. the increasing level of complexity for the round function would be greatly contributing to an increase in complexity. To increase the complexity of the round function, the avalanche effect is also included in the round function, as the change of a single bit in plain text would produce a mischievous output due to the presence of avalanche effect.
- 6. Unit 2:Symmetric key AlgorithmS Block Cipher : PT CT 64 64 64 64 64 64 64 64 64 64 64 64 64 64 64 64 64 64 64 64 KEY 40,56,64,128,256 bits
- 7. Unit 2:Symmetric key AlgorithmS
- 8. Unit 2:Symmetric key AlgorithmS
- 9. Unit 2:Symmetric key AlgorithmS (DES)
- 10. Unit 2:Symmetric key AlgorithmS (DES)
- 11. Unit 2:Symmetric key AlgorithmS (DES)
- 12. Unit 2:Symmetric key AlgorithmS (DES)
- 13. Unit 2:Symmetric key AlgorithmS (DES)
- 14. Unit 2:Symmetric key AlgorithmS (DES)
- 15. Unit 2:Symmetric key AlgorithmS (DES)
- 16. Unit 2:Symmetric key AlgorithmS (DES) Expansion Permutation
- 17. Unit 2:Symmetric key AlgorithmS (DES)
- 18. Unit 2:Symmetric key AlgorithmS (DES)
- 19. Unit 2:Symmetric key AlgorithmS (DES)
- 20. Unit 2:Symmetric key AlgorithmS (DES)
- 21. Unit 2:Symmetric key AlgorithmS (DES)
- 22. Unit 2:Symmetric key AlgorithmS (DES)
- 23. Unit 2:Symmetric key AlgorithmS (DES)
- 24. Unit 2:Symmetric key AlgorithmS (AES)
- 25. Unit 2:Symmetric key AlgorithmS (AES)
- 26. Unit 2:Symmetric key AlgorithmS (AES)
- 27. Unit 2:Symmetric key AlgorithmS (AES)
- 28. Unit 2:Symmetric key AlgorithmS (AES)
- 29. Unit 2:Symmetric key AlgorithmS (AES)
- 30. Unit 2:Symmetric key AlgorithmS (AES)
- 31. Unit 2:Symmetric key AlgorithmS (AES)
- 32. Unit 2:Symmetric key AlgorithmS (AES)
- 33. Unit 2:Symmetric key AlgorithmS (AES)
- 34. Unit 2:Symmetric key AlgorithmS (AES Key expansion)
- 35. Unit 2:Symmetric key AlgorithmS (AES Key expansion)
- 36. Unit 2:Symmetric key AlgorithmS (AES Key expansion)
- 37. Unit 2:Symmetric key AlgorithmS (AES Key expansion)
- 38. Unit 2:Symmetric key AlgorithmS (AES Key expansion)
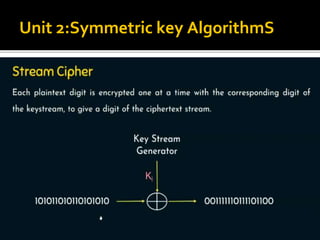
- 39. Unit 2:Symmetric key AlgorithmS (Block cipher operation)
- 40. Unit 2:Symmetric key AlgorithmS (Block cipher operation)
- 41. Unit 2:Symmetric key AlgorithmS (Block cipher operation)
- 42. Unit 2:Symmetric key AlgorithmS (Block cipher operation)
- 43. Unit 2:Symmetric key AlgorithmS (Block cipher operation)
- 44. Unit 2:Symmetric key AlgorithmS (Block cipher operation)
- 45. Unit 2:Symmetric key AlgorithmS (Block cipher operation)
- 46. Principles of Public key cryptography
- 47. Principles of Public key cryptography
- 48. Principles of Public key cryptography
- 49. Principles of Public key cryptography
- 50. Principles of Public key cryptography
- 51. Principles of Public key cryptography
- 52. RSA Algorithm