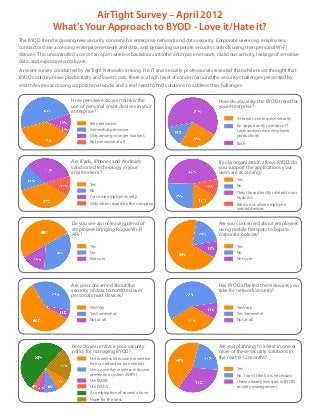
BYOD (Bring your own device) comparison by Safetica Benelux
- 1. AirTight Survey – April 2012 What’s Your Approach to BYOD - Love it/Hate it? The BYOD trend is causing new security concerns for enterprise network and data security. Corporate users (e.g. employees, contractors) are accessing enterprise network and data, and bypassing corporate security controls using their personal Wi-Fi devices. This uncontrolled access can open wireless backdoors into the enterprise network, malicious activity, leakage of sensitive data, and exposure to malware. A recent survey conducted by AirTight Networks among 316 IT and Security professionals revealed that while most thought that BYOD could increase productivity and lower costs, there is a high level of concern around the security challenges presented by smart devices accessing corporate networks and a real need to find solutions to address the challenges. How pervasive do you think is the How do you view the BYOD trend for use of personal smart devices in your your enterprise? enterprise? A threat to enterprise security Very pervasive An opportunity to reduce IT Somewhat pervasive costs and increase employee Only among younger workers productivity Not pervasive at all Both Are iPads, iPhones and Androids If your organization allows BYOD, do sanctioned technology in your you support the applications your environment? users are accessing? Yes Yes No No Only those directly related to our For some employees only business Only when issued by the company We do not allow employee owned devices Do you see an increasing trend of Are you concerned about employees employees bringing Rogue Wi-Fi using mobile hotspots to bypass APs? corporate policies? Yes Yes No No Not sure Not sure Are you concerned about the Has BYOD affected the measures you security of data transmitted over take for network security? personal smart devices? Yes Very Yes Very Yes Somewhat Yes Somewhat Not at all Not at all How do you enforce your security Are you planning to invest in one or policy for managing BYOD? more of these security solutions in Use wireless intrusion prevention the next 6-12 months? from an infrastructure vendor Use an overlay wireless intrusion Yes prevention system (WIPS) No, I don’t think it is necessary Use MDM I have already invested in BYOD Use NACS security management A combination of several above Hope for the best
- 2. BYOD Security Threats and Mitigation Strategies The deluge of personal devices in the enterprise makes it critical to choose the right combination of solutions for protecting your network and managing your devices. Malware As the BYOD tide rises, organizations will need to embrace various smartphones and tablets for the enterprise applications, while at the same time tackling the security challenges from consumerization. On one hand, it is necessary to ensure that the IT assigned authorized smart mobile devices are free of malware and that these devices and the data on them can be centrally managed and monitored by IT. On the other hand, IT will be required to deal with unmanaged personal mobile devices attempting to access the corporate IT assets, since such personal mobile devices may not be within IT’s device management reach. Remote Wiping Additionally, increased consumerization of the smart mobile devices may also heighten the risk of rogue Wi-Fi connections on the enterprise premises. As a result, an all-encompassing approach to BYOD security will entail protection of IT assigned devices, gatekeeping the unmanaged mobile devices, and blocking rogue Wi-Fi connections. Security systems are available today which address different parts of the BYOD security problem. The right combination of these security systems can be useful for a comprehensive BYOD security. Network Security Controls Unmanaged Devices Intrusion Security Control Wi-Fi WIPS NAC Enterprise Requirement Infra. Wi-Fi Gatekeeping unmanaged mobile devices Detect and block rogue access points Block extrusions thru external Wi-Fi/personal hotspots Finer inline policy enforcement on traffic Authorized Devices Extrusion Wi-Fi Infrastructure: APs and Controllers WIPS: Wireless Intrusion Prevention NAC: Network Access Control Device and Apps Security Controls Security Control Requirement MDM + OS Device management, anti-malware, remote wiping, application security The Global Leader in Wireless Security Solutions AirTight Networks, Inc. 339 N. Bernardo Avenue #200, Mountain View, CA 94043 T +1.877.424.7844 T 650.961.1111 F 650.961.1169 www.airtightnetworks.com
