Provisioning Privacy for TIP Attribute in Trusted Third Party (TTP) Location Based Services (LBS) System
Currently, Location Based Services (LBS) System is rapidly growing due to radio communication services with wireless mobile devices having a positioning component in it. LBS System offers location-based services by knowing the actual user position. A mobile user uses LBS to access services relevant to their locations. In order to provide Point of Interest (POI), LBS confronts numerous privacy-related challenges. Conventionally, LBS systems are treat in three ways including Non-Trusted Third Party (NTTP), Trusted Third Party (TTP) and Mobile Peer-to-Peer (P2P). The current study emphasized the TTP based LBS system where the Location server does not provide full privacy to mobile users. In TTP based LBS system, a user’s privacy is concerned with personal identity, location information, and time information. In order to accomplish privacy under these concerns, state-of-the-art existing mechanisms have been reviewed. Hence, the aim to provide a promising roadmap to research and development communities for right selection of privacy approach has achieved by conducting a comparative survey of the TTP based approaches. Leading to these privacy attributes, current study addressed the privacy challenge by proposing a new privacy protection model named “Improved Dummy Position” (IDP) that protects TIP (Time, Identity, and Position) attributes under TTP LBS System. In order to validate the privacy level, a comparative analysis has been conduct by implementing the proposed IDP model in the simulation tool, Riverbed Modeler academic edition. The different scenarios of changing query transferring rate evaluate the performance of proposed model. Simulation results demonstrate that our IDP could be considered as a promising model to protect user’s TIP attributes in a TTP based LBS system due to better performance and improved privacy level. Further, the proposed model extensively compared with the existing work.
Empfohlen
Empfohlen
Weitere ähnliche Inhalte
Ähnlich wie Provisioning Privacy for TIP Attribute in Trusted Third Party (TTP) Location Based Services (LBS) System
Ähnlich wie Provisioning Privacy for TIP Attribute in Trusted Third Party (TTP) Location Based Services (LBS) System (20)
Mehr von Rida Qayyum
Mehr von Rida Qayyum (6)
Kürzlich hochgeladen
Kürzlich hochgeladen (20)
Provisioning Privacy for TIP Attribute in Trusted Third Party (TTP) Location Based Services (LBS) System
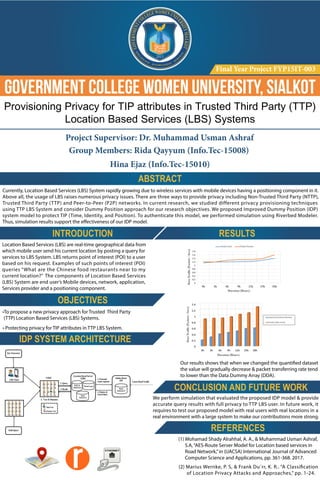
- 1. Government College Women University, Sialkot ABSTRACT INTRODUCTION OBJECTIVES IDP SYSTEM ARCHITECTURE RESULTS CONCLUSION AND FUTURE WORK REFERENCES Final Year Project FYP15IT-003 Provisioning Privacy for TIP attributes in Trusted Third Party (TTP) Location Based Services (LBS) Systems Project Supervisor: Dr. Muhammad Usman Ashraf Group Members: Rida Qayyum (Info.Tec-15008) Hina Ejaz (Info.Tec-15010) Currently, Location Based Services (LBS) System rapidly growing due to wireless services with mobile devices having a positioning component in it. Above all, the usage of LBS raises numerous privacy issues. There are three ways to provide privacy including Non-Trusted Third Party (NTTP), Trusted Third Party (TTP) and Peer-to-Peer (P2P) networks. In current research, we studied different privacy provisioning techniques using TTP LBS System and consider Dummy Position approach for our research objectives. We proposed Improved Dummy Position (IDP) system model to protect TIP (Time, Identity, and Position). To authenticate this model, we performed simulation using Riverbed Modeler. Thus, simulation results support the effectiveness of our IDP model. Location Based Services (LBS) are real-time geographical data from which mobile user send his current location by posting a query for services to LBS System. LBS returns point of interest (POI) to a user based on his request. Examples of such points of interest (POI) queries “What are the Chinese food restaurants near to my current location?” The components of Location Based Services (LBS) System are end user’s Mobile devices, network, application, Services provider and a positioning component. •To propose a new privacy approach for Trusted Third Party (TTP) Location Based Services (LBS) Systems. • Protecting privacy for TIP attributes in TTP LBS System. Our results shows that when we changed the quantified dataset the value will gradually decrease & packet transferring rate tend to lower than the Data Dummy Array (DDA). We perform simulation that evaluated the proposed IDP model & provide accurate query results with full privacy to TTP LBS user. In future work, it requires to test our proposed model with real users with real locations in a real environment with a large system to make our contributions more strong. (1) Mohamad Shady Alrahhal, A. A., & Muhammad Usman Ashraf, S.A,“AES-Route Server Model for Location based services in Road Network,”in (IJACSA) International Journal of Advanced Computer Science and Applications, pp. 361-368. 2017. (2) Marius Wernke, P. S, & Frank Du¨rr, K. R.. “A Classification of Location Privacy Attacks and Approaches,” pp. 1-24.