SIEM POC Assessment.pdf
•
0 gefällt mir•197 views
This is a sample table to consider for the evaluation of a SIEM when you are going to buy it.
Melden
Teilen
Melden
Teilen
Downloaden Sie, um offline zu lesen
Empfohlen
Weitere ähnliche Inhalte
Was ist angesagt?
Was ist angesagt? (20)
SOC: Use cases and are we asking the right questions?

SOC: Use cases and are we asking the right questions?
Security Operations Center (SOC) Essentials for the SME

Security Operations Center (SOC) Essentials for the SME
What We’ve Learned Building a Cyber Security Operation Center: du Case Study

What We’ve Learned Building a Cyber Security Operation Center: du Case Study
Effective Security Operation Center - present by Reza Adineh

Effective Security Operation Center - present by Reza Adineh
Effective Threat Hunting with Tactical Threat Intelligence

Effective Threat Hunting with Tactical Threat Intelligence
Security operations center-SOC Presentation-مرکز عملیات امنیت

Security operations center-SOC Presentation-مرکز عملیات امنیت
An introduction to SOC (Security Operation Center)

An introduction to SOC (Security Operation Center)
Ähnlich wie SIEM POC Assessment.pdf
Ähnlich wie SIEM POC Assessment.pdf (20)
RSA-Pivotal Security Big Data Reference Architecture

RSA-Pivotal Security Big Data Reference Architecture
Overall Security Process Review CISC 6621Agend.docx

Overall Security Process Review CISC 6621Agend.docx
Security Information Event Management Security Information Event Management

Security Information Event Management Security Information Event Management
SOC presentation- Building a Security Operations Center

SOC presentation- Building a Security Operations Center
Mehr von ReZa AdineH
Mehr von ReZa AdineH (10)
Cover of book Threat Intelligence for Threat Hunting;Written by Reza Adineh

Cover of book Threat Intelligence for Threat Hunting;Written by Reza Adineh
Next generation Security Operation Center; Written by Reza Adineh

Next generation Security Operation Center; Written by Reza Adineh
Review on Event Correlation- مروری بر روش های همبسته سازی در مدیریت رخداد

Review on Event Correlation- مروری بر روش های همبسته سازی در مدیریت رخداد
علت ناکامی بسیاری از پروژههای مرکزعملیاتامنیت چیست ؟

علت ناکامی بسیاری از پروژههای مرکزعملیاتامنیت چیست ؟
Security monitoring log management-describe logstash,kibana,elastic slidshare

Security monitoring log management-describe logstash,kibana,elastic slidshare
Kürzlich hochgeladen
(NEHA) Call Girls Katra Call Now 8617697112 Katra Escorts 24x7

(NEHA) Call Girls Katra Call Now 8617697112 Katra Escorts 24x7Call Girls in Nagpur High Profile Call Girls
Kürzlich hochgeladen (20)
Vip Model Call Girls (Delhi) Karol Bagh 9711199171✔️Body to body massage wit...

Vip Model Call Girls (Delhi) Karol Bagh 9711199171✔️Body to body massage wit...
Call Girls Bannerghatta Road Just Call 👗 7737669865 👗 Top Class Call Girl Ser...

Call Girls Bannerghatta Road Just Call 👗 7737669865 👗 Top Class Call Girl Ser...
(NEHA) Call Girls Katra Call Now 8617697112 Katra Escorts 24x7

(NEHA) Call Girls Katra Call Now 8617697112 Katra Escorts 24x7
Determinants of health, dimensions of health, positive health and spectrum of...

Determinants of health, dimensions of health, positive health and spectrum of...
Market Analysis in the 5 Largest Economic Countries in Southeast Asia.pdf

Market Analysis in the 5 Largest Economic Countries in Southeast Asia.pdf
Call me @ 9892124323 Cheap Rate Call Girls in Vashi with Real Photo 100% Secure

Call me @ 9892124323 Cheap Rate Call Girls in Vashi with Real Photo 100% Secure
BPAC WITH UFSBI GENERAL PRESENTATION 18_05_2017-1.pptx

BPAC WITH UFSBI GENERAL PRESENTATION 18_05_2017-1.pptx
Generative AI on Enterprise Cloud with NiFi and Milvus

Generative AI on Enterprise Cloud with NiFi and Milvus
Call Girls Hsr Layout Just Call 👗 7737669865 👗 Top Class Call Girl Service Ba...

Call Girls Hsr Layout Just Call 👗 7737669865 👗 Top Class Call Girl Service Ba...
Delhi Call Girls Punjabi Bagh 9711199171 ☎✔👌✔ Whatsapp Hard And Sexy Vip Call

Delhi Call Girls Punjabi Bagh 9711199171 ☎✔👌✔ Whatsapp Hard And Sexy Vip Call
Junnasandra Call Girls: 🍓 7737669865 🍓 High Profile Model Escorts | Bangalore...

Junnasandra Call Girls: 🍓 7737669865 🍓 High Profile Model Escorts | Bangalore...
Cheap Rate Call girls Sarita Vihar Delhi 9205541914 shot 1500 night

Cheap Rate Call girls Sarita Vihar Delhi 9205541914 shot 1500 night
SIEM POC Assessment.pdf
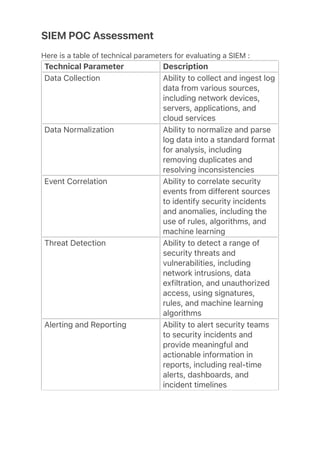
- 1. SIEM POC Assessment Here is a table of technical parameters for evaluating a SIEM : Technical Parameter Description Data Collection Ability to collect and ingest log data from various sources, including network devices, servers, applications, and cloud services Data Normalization Ability to normalize and parse log data into a standard format for analysis, including removing duplicates and resolving inconsistencies Event Correlation Ability to correlate security events from different sources to identify security incidents and anomalies, including the use of rules, algorithms, and machine learning Threat Detection Ability to detect a range of security threats and vulnerabilities, including network intrusions, data exfiltration, and unauthorized access, using signatures, rules, and machine learning algorithms Alerting and Reporting Ability to alert security teams to security incidents and provide meaningful and actionable information in reports, including real-time alerts, dashboards, and incident timelines Incident Response Ability to provide a streamlined and efficient process for incident response and escalation, including incident prioritization, assignment, and tracking
- 2. reports, including real-time alerts, dashboards, and incident timelines Incident Response Ability to provide a streamlined and efficient process for incident response and escalation, including incident prioritization, assignment, and tracking User Management Ability to control access and manage user accounts, permissions, and roles, including role-based access control and audit trails Data Privacy and Security Measures in place to protect the privacy and security of log data stored in the SIEM system, including encryption, access controls, and data retention policies Scalability and Performance Ability to scale to meet the demands of a large and complex network environment, including the ability to handle high volumes of log data and handle multiple concurrent users Integration with Other Security Tools Ability to integrate with other security tools and systems to provide a unified view of the organization's security posture, including security information and event management (SIEM), security orchestration, automation and response (SOAR), and security analytics tools This table provides a more comprehensive set of technical parameters for evaluating a SIEM during Proof of Concept (POC). Evaluating these parameters can provide a deeper understanding of the SIEM system's capabilities and help determine its suitability for full deployment in your organization's network environment.
- 3. Produced By: Reza Adineh Think Smarter, Stay Secure …
