Remote Work Fuels Zero Trust Growth
•
0 gefällt mir•176 views
See what Ping’s Executive Survey reveals about the security impacts of the shift to remote work.
Melden
Teilen
Melden
Teilen
Downloaden Sie, um offline zu lesen
Empfohlen
Empfohlen
Weitere ähnliche Inhalte
Was ist angesagt?
Was ist angesagt? (20)
Gerent spotlight - Reinventing the Insurance Customer Journey

Gerent spotlight - Reinventing the Insurance Customer Journey
Accelerating Growth with Data-Driven Customer Experience

Accelerating Growth with Data-Driven Customer Experience
Accenture Communications Industry 2021 - Connectivity Optimizer

Accenture Communications Industry 2021 - Connectivity Optimizer
Accenture Federal Technology Vision 2020: FIVE TRENDS DEFINING POST-DIGITAL G...

Accenture Federal Technology Vision 2020: FIVE TRENDS DEFINING POST-DIGITAL G...
Gartner Webinars: Top 5 Post-COVID Workforce Planning 

Gartner Webinars: Top 5 Post-COVID Workforce Planning
Digital Transformation ROI Survey From Wipro Digital

Digital Transformation ROI Survey From Wipro Digital
Cb insights the-future-according-to-andreessen-horowitz

Cb insights the-future-according-to-andreessen-horowitz
Medicare-Aged Users Want a Digital Experience and Tools

Medicare-Aged Users Want a Digital Experience and Tools
Customer Experience in Insurance: Insurer Strategies, Plans and Progress

Customer Experience in Insurance: Insurer Strategies, Plans and Progress
NYC Companies See the Value of Emerging Tech, But Are They Ready?

NYC Companies See the Value of Emerging Tech, But Are They Ready?
Ähnlich wie Remote Work Fuels Zero Trust Growth
Through “Authentication Solution Providers 2019” issue, Insights Success takes an initiative in addressing some of the finest organizations who stand forth in delivering best authentication solutions at one’s door.
The 10 most trusted authentication solution providers 2018

The 10 most trusted authentication solution providers 2018Insights success media and technology pvt ltd
Ähnlich wie Remote Work Fuels Zero Trust Growth (20)
Why Zero Trust Architecture Will Become the New Normal in 2021

Why Zero Trust Architecture Will Become the New Normal in 2021
India's Leading Cyber Security Companies to Watch.pdf

India's Leading Cyber Security Companies to Watch.pdf
How Aligned Are IT, Employees and Security Practices in Today's Mobile World?

How Aligned Are IT, Employees and Security Practices in Today's Mobile World?
CompTIA - IT Security Sales Practices in the Channel 

CompTIA - IT Security Sales Practices in the Channel
CIO Agenda 2015 - Flipping Into Digital Leadership

CIO Agenda 2015 - Flipping Into Digital Leadership
SVB Cybersecurity Impact on Innovation Report - Overview

SVB Cybersecurity Impact on Innovation Report - Overview
The 10 most trusted authentication solution providers 2018

The 10 most trusted authentication solution providers 2018
Mehr von Ping Identity
Mehr von Ping Identity (20)
Security Practices: The Generational Gap | Infographic

Security Practices: The Generational Gap | Infographic
Hybrid IAM: Fuelling Agility in the Cloud Transformation Journey | Gartner IA...

Hybrid IAM: Fuelling Agility in the Cloud Transformation Journey | Gartner IA...
LES ATTITUDES DES CONSOMMATEURS À L’ÈRE DES CYBERATTAQUES

LES ATTITUDES DES CONSOMMATEURS À L’ÈRE DES CYBERATTAQUES
WIE TICKEN VERBRAUCHER IM ZEITALTER DER DATENSCHUTZVERLETZUNGEN?

WIE TICKEN VERBRAUCHER IM ZEITALTER DER DATENSCHUTZVERLETZUNGEN?
Consumer Attitudes in a Post-breach Era: The Geographical Gap

Consumer Attitudes in a Post-breach Era: The Geographical Gap
Standard Based API Security, Access Control and AI Based Attack - API Days Pa...

Standard Based API Security, Access Control and AI Based Attack - API Days Pa...
ATTITUDES DES CONSOMMATEURS A L’ERE DES PIRATAGES LE CONFLIT DE GENERATIONS

ATTITUDES DES CONSOMMATEURS A L’ERE DES PIRATAGES LE CONFLIT DE GENERATIONS
2018 Survey: Consumer Attitudes in a Post-Breach Era - The Generational Gap

2018 Survey: Consumer Attitudes in a Post-Breach Era - The Generational Gap
WIE TICKEN VERBRAUCHER IM ZEITALTER DER DATENSCHUTZVERLETZUNGEN? ALLES EINE F...

WIE TICKEN VERBRAUCHER IM ZEITALTER DER DATENSCHUTZVERLETZUNGEN? ALLES EINE F...
Fishing for a CIAM Platform? 11 Question to Ask Before You Buy

Fishing for a CIAM Platform? 11 Question to Ask Before You Buy
Criteria for Effective Modern IAM Strategies (Gartner IAM 2018)

Criteria for Effective Modern IAM Strategies (Gartner IAM 2018)
Webinar: Three Steps to Transform Your Mobile App into a Security Factor

Webinar: Three Steps to Transform Your Mobile App into a Security Factor
Kürzlich hochgeladen
Kürzlich hochgeladen (20)
Introduction to Multilingual Retrieval Augmented Generation (RAG)

Introduction to Multilingual Retrieval Augmented Generation (RAG)
How to Troubleshoot Apps for the Modern Connected Worker

How to Troubleshoot Apps for the Modern Connected Worker
Emergent Methods: Multi-lingual narrative tracking in the news - real-time ex...

Emergent Methods: Multi-lingual narrative tracking in the news - real-time ex...
Apidays New York 2024 - The Good, the Bad and the Governed by David O'Neill, ...

Apidays New York 2024 - The Good, the Bad and the Governed by David O'Neill, ...
Strategize a Smooth Tenant-to-tenant Migration and Copilot Takeoff

Strategize a Smooth Tenant-to-tenant Migration and Copilot Takeoff
TrustArc Webinar - Unlock the Power of AI-Driven Data Discovery

TrustArc Webinar - Unlock the Power of AI-Driven Data Discovery
Web Form Automation for Bonterra Impact Management (fka Social Solutions Apri...

Web Form Automation for Bonterra Impact Management (fka Social Solutions Apri...
Biography Of Angeliki Cooney | Senior Vice President Life Sciences | Albany, ...

Biography Of Angeliki Cooney | Senior Vice President Life Sciences | Albany, ...
Polkadot JAM Slides - Token2049 - By Dr. Gavin Wood

Polkadot JAM Slides - Token2049 - By Dr. Gavin Wood
Finding Java's Hidden Performance Traps @ DevoxxUK 2024

Finding Java's Hidden Performance Traps @ DevoxxUK 2024
Why Teams call analytics are critical to your entire business

Why Teams call analytics are critical to your entire business
Apidays New York 2024 - Accelerating FinTech Innovation by Vasa Krishnan, Fin...

Apidays New York 2024 - Accelerating FinTech Innovation by Vasa Krishnan, Fin...
Apidays New York 2024 - APIs in 2030: The Risk of Technological Sleepwalk by ...

Apidays New York 2024 - APIs in 2030: The Risk of Technological Sleepwalk by ...
Six Myths about Ontologies: The Basics of Formal Ontology

Six Myths about Ontologies: The Basics of Formal Ontology
Connector Corner: Accelerate revenue generation using UiPath API-centric busi...

Connector Corner: Accelerate revenue generation using UiPath API-centric busi...
Remote Work Fuels Zero Trust Growth
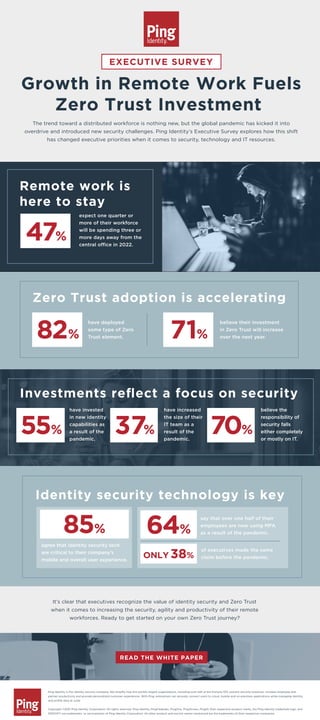
- 1. Growth in Remote Work Fuels Zero Trust Investment EXECUTIVE SURVEY Remote work is here to stay 47% expect one quarter or more of their workforce will be spending three or more days away from the central office in 2022. The trend toward a distributed workforce is nothing new, but the global pandemic has kicked it into overdrive and introduced new security challenges. Ping Identity’s Executive Survey explores how this shift has changed executive priorities when it comes to security, technology and IT resources. It’s clear that executives recognize the value of identity security and Zero Trust when it comes to increasing the security, agility and productivity of their remote workforces. Ready to get started on your own Zero Trust journey? Zero Trust adoption is accelerating 82% have deployed some type of Zero Trust element. believe their investment in Zero Trust will increase over the next year. 71% Investments reflect a focus on security 55% have invested in new identity capabilities as a result of the pandemic. 37% have increased the size of their IT team as a result of the pandemic. 70% believe the responsibility of security falls either completely or mostly on IT. Identity security technology is key 85% agree that identity security tech are critical to their company’s mobile and overall user experience. ONLY 38% of executives made the same claim before the pandemic. 64% say that over one half of their employees are now using MFA as a result of the pandemic. READ THE WHITE PAPER Ping Identity is the identity security company. We simplify how the world's largest organizations, including over half of the Fortune 100, prevent security breaches, increase employee and partner productivity and provide personalized customer experiences. With Ping, enterprises can securely connect users to cloud, mobile and on-premises applications while managing identity and profile data at scale. Copyright ©2021 Ping Identity Corporation. All rights reserved. Ping Identity, PingFederate, PingOne, PingAccess, PingID, their respective product marks, the Ping Identity trademark logo, and IDENTIFY are trademarks, or servicemarks of Ping Identity Corporation. All other product and service names mentioned are the trademarks of their respective companies.
