A Brief History of Electronic Signatures
•
1 gefällt mir•1,528 views
This year, June 30th marks the 15th anniversary of The Electronic Signatures in Global and National Commerce Act, a piece of legislation passed to facilitate the use of electronic records and signatures in domestic and foreign commerce. This infographic gives a brief history of electronic signatures, which have (technically) been used since the mid 1800's!
Melden
Teilen
Melden
Teilen
Downloaden Sie, um offline zu lesen
Empfohlen
Empfohlen
Weitere ähnliche Inhalte
Was ist angesagt?
Was ist angesagt? (20)
The greatest IoT sales slidedeck every created (2nd version)

The greatest IoT sales slidedeck every created (2nd version)
Legal and ethical issues associated with modern technologies

Legal and ethical issues associated with modern technologies
Ähnlich wie A Brief History of Electronic Signatures
Ähnlich wie A Brief History of Electronic Signatures (20)
Global E-signature Laws at a Glance | DrySign By Exela

Global E-signature Laws at a Glance | DrySign By Exela
electronic transactions law lecture series: lecture 1 introduction

electronic transactions law lecture series: lecture 1 introduction
Signing away evolving law of electronic signatures & paperless office

Signing away evolving law of electronic signatures & paperless office
Digital Signatures: The Law and Best Practices for Compliance

Digital Signatures: The Law and Best Practices for Compliance
Countries that have made electronic signatures legal

Countries that have made electronic signatures legal
The Electronic Commerce Act and its Implementing Rules and Regulations

The Electronic Commerce Act and its Implementing Rules and Regulations
Cyber Law & Crime (Information Technology Act, 2000)

Cyber Law & Crime (Information Technology Act, 2000)
Digital identity theft remedial efforts case of uganda_ruyooka

Digital identity theft remedial efforts case of uganda_ruyooka
Uganda cyber laws _ isaca workshop_kampala_by Ruyooka

Uganda cyber laws _ isaca workshop_kampala_by Ruyooka
Mehr von Nitro, Inc.
Mehr von Nitro, Inc. (9)
Customer Survey Proves IT Satisfaction in Key Performance Areas

Customer Survey Proves IT Satisfaction in Key Performance Areas
Sustainability in the New World of Content and Documents

Sustainability in the New World of Content and Documents
Security in the New World of Content and Documents

Security in the New World of Content and Documents
Thriving in the New World of Content and Documents

Thriving in the New World of Content and Documents
Nitro Infographic: Are Your Document Practices Slowing Down Your Productivity?

Nitro Infographic: Are Your Document Practices Slowing Down Your Productivity?
The Paperless Office: Why it Hasn't Happened, and Why It's Going To

The Paperless Office: Why it Hasn't Happened, and Why It's Going To
How Your Document Habits are Destroying Productivity 

How Your Document Habits are Destroying Productivity
Breaking Bad Habits: Escape the Document Productivity Drain

Breaking Bad Habits: Escape the Document Productivity Drain
Kürzlich hochgeladen
Enterprise Knowledge’s Urmi Majumder, Principal Data Architecture Consultant, and Fernando Aguilar Islas, Senior Data Science Consultant, presented "Driving Behavioral Change for Information Management through Data-Driven Green Strategy" on March 27, 2024 at Enterprise Data World (EDW) in Orlando, Florida.
In this presentation, Urmi and Fernando discussed a case study describing how the information management division in a large supply chain organization drove user behavior change through awareness of the carbon footprint of their duplicated and near-duplicated content, identified via advanced data analytics. Check out their presentation to gain valuable perspectives on utilizing data-driven strategies to influence positive behavioral shifts and support sustainability initiatives within your organization.
In this session, participants gained answers to the following questions:
- What is a Green Information Management (IM) Strategy, and why should you have one?
- How can Artificial Intelligence (AI) and Machine Learning (ML) support your Green IM Strategy through content deduplication?
- How can an organization use insights into their data to influence employee behavior for IM?
- How can you reap additional benefits from content reduction that go beyond Green IM?
Driving Behavioral Change for Information Management through Data-Driven Gree...

Driving Behavioral Change for Information Management through Data-Driven Gree...Enterprise Knowledge
Kürzlich hochgeladen (20)
08448380779 Call Girls In Greater Kailash - I Women Seeking Men

08448380779 Call Girls In Greater Kailash - I Women Seeking Men
Automating Google Workspace (GWS) & more with Apps Script

Automating Google Workspace (GWS) & more with Apps Script
The 7 Things I Know About Cyber Security After 25 Years | April 2024

The 7 Things I Know About Cyber Security After 25 Years | April 2024
08448380779 Call Girls In Diplomatic Enclave Women Seeking Men

08448380779 Call Girls In Diplomatic Enclave Women Seeking Men
2024: Domino Containers - The Next Step. News from the Domino Container commu...

2024: Domino Containers - The Next Step. News from the Domino Container commu...
Understanding Discord NSFW Servers A Guide for Responsible Users.pdf

Understanding Discord NSFW Servers A Guide for Responsible Users.pdf
Strategies for Landing an Oracle DBA Job as a Fresher

Strategies for Landing an Oracle DBA Job as a Fresher
08448380779 Call Girls In Civil Lines Women Seeking Men

08448380779 Call Girls In Civil Lines Women Seeking Men
Driving Behavioral Change for Information Management through Data-Driven Gree...

Driving Behavioral Change for Information Management through Data-Driven Gree...
Powerful Google developer tools for immediate impact! (2023-24 C)

Powerful Google developer tools for immediate impact! (2023-24 C)
Tech Trends Report 2024 Future Today Institute.pdf

Tech Trends Report 2024 Future Today Institute.pdf
TrustArc Webinar - Stay Ahead of US State Data Privacy Law Developments

TrustArc Webinar - Stay Ahead of US State Data Privacy Law Developments
Raspberry Pi 5: Challenges and Solutions in Bringing up an OpenGL/Vulkan Driv...

Raspberry Pi 5: Challenges and Solutions in Bringing up an OpenGL/Vulkan Driv...
A Brief History of Electronic Signatures
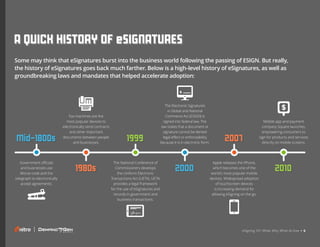
- 1. eSigning 101: What, Why, When & How • 6 A QUICK HISTORY OF eSIGNATURES Some may think that eSignatures burst into the business world following the passing of ESIGN. But really, the history of eSignatures goes back much farther. Below is a high-level history of eSignatures, as well as groundbreaking laws and mandates that helped accelerate adoption: Mid-1800s Government officials and businesses use Morse code and the telegraph to electronically accept agreements. 1980s Fax machines are the most popular devices to electronically send contracts and other important documents between people and businesses. 1999 The National Conference of Commissioners develops the Uniform Electronic Transactions Act (UETA). UETA provides a legal framework for the use of eSignatures and records in government and business transactions. 2000 The Electronic Signatures in Global and National Commerce Act (ESIGN) is signed into federal law. The law states that a document or signature cannot be denied legal effect or enforceability because it is in electronic form. 2007 Apple releases the iPhone, which becomes one of the world’s most popular mobile devices. Widespread adoption of touchscreen devices is increasing demand for allowing eSigning on the go. 2010 Mobile app and payment company Square launches, empowering consumers to sign for products and services directly on mobile screens. eSigning 101: What, Why, When & How • 6
