Beyond
•Als PPTX, PDF herunterladen•
0 gefällt mir•19 views
What to do after 90 days to improve cybersecurity
Melden
Teilen
Melden
Teilen
Empfohlen
Empfohlen
If you are looking to simplify IT management in your organization, then enterprise Operations Management Suite (OMS) is for you.
With OMS you will gain control over your Azure hybrid cloud with this cost-effective, all-in-one cloud IT management solution.
It delivers you:
Operational insights into your on premise and cloud applications and infrastructure
Solid Backup and Disaster recovery solution that is automated and easy to test
Compliant infrastructure with the latest industry security standards, update levels, and configuration best practices
In the webinar you will learn about:
Log Analytics and what it can accomplish
Backup and Automated Site Recovery
Identifying, assessing and mitigating security risks
What' coming next with the Solutions GalleryEffective Management of Azure through Operations Management Suite (OMS) Webinar

Effective Management of Azure through Operations Management Suite (OMS) WebinarSoftchoice Corporation
Weitere ähnliche Inhalte
Was ist angesagt?
If you are looking to simplify IT management in your organization, then enterprise Operations Management Suite (OMS) is for you.
With OMS you will gain control over your Azure hybrid cloud with this cost-effective, all-in-one cloud IT management solution.
It delivers you:
Operational insights into your on premise and cloud applications and infrastructure
Solid Backup and Disaster recovery solution that is automated and easy to test
Compliant infrastructure with the latest industry security standards, update levels, and configuration best practices
In the webinar you will learn about:
Log Analytics and what it can accomplish
Backup and Automated Site Recovery
Identifying, assessing and mitigating security risks
What' coming next with the Solutions GalleryEffective Management of Azure through Operations Management Suite (OMS) Webinar

Effective Management of Azure through Operations Management Suite (OMS) WebinarSoftchoice Corporation
Was ist angesagt? (15)
Rackspace Unlocked 2014 - Cyber-Duck's PCI Compliance Case Study

Rackspace Unlocked 2014 - Cyber-Duck's PCI Compliance Case Study
Effective Management of Azure through Operations Management Suite (OMS) Webinar

Effective Management of Azure through Operations Management Suite (OMS) Webinar
Flink Forward Berlin 2018: Yonatan Most & Avihai Berkovitz - "Anomaly Detecti...

Flink Forward Berlin 2018: Yonatan Most & Avihai Berkovitz - "Anomaly Detecti...
Combining logs, metrics, and traces for unified observability

Combining logs, metrics, and traces for unified observability
The New Remote Workforce & The Case for Hosting Your Sage Solution in the Cloud

The New Remote Workforce & The Case for Hosting Your Sage Solution in the Cloud
Elastic APM: Amping up your logs and metrics for the full picture

Elastic APM: Amping up your logs and metrics for the full picture
Combining Logs, Metrics, and Traces for Unified Observability

Combining Logs, Metrics, and Traces for Unified Observability
AWS Enterprise Summit London 2013 - Stephen Schmidt - AWS

AWS Enterprise Summit London 2013 - Stephen Schmidt - AWS
Keynote: Elastic Observability evolution and vision

Keynote: Elastic Observability evolution and vision
Ähnlich wie Beyond
Ähnlich wie Beyond (20)
Rencore Webinar: Advanced Security Management within Office 365 with Liam Cleary

Rencore Webinar: Advanced Security Management within Office 365 with Liam Cleary
Microsoft 365 Enterprise Security with E5 Overview

Microsoft 365 Enterprise Security with E5 Overview
Microsoft Information Protection: Your Security and Compliance Framework

Microsoft Information Protection: Your Security and Compliance Framework
Fundamentals of Microsoft 365 Security , Identity and Compliance

Fundamentals of Microsoft 365 Security , Identity and Compliance
Achieve Compliance with Security by Default and By Design

Achieve Compliance with Security by Default and By Design
Kürzlich hochgeladen
Kürzlich hochgeladen (20)
08448380779 Call Girls In Diplomatic Enclave Women Seeking Men

08448380779 Call Girls In Diplomatic Enclave Women Seeking Men
The Role of Taxonomy and Ontology in Semantic Layers - Heather Hedden.pdf

The Role of Taxonomy and Ontology in Semantic Layers - Heather Hedden.pdf
Axa Assurance Maroc - Insurer Innovation Award 2024

Axa Assurance Maroc - Insurer Innovation Award 2024
Powerful Google developer tools for immediate impact! (2023-24 C)

Powerful Google developer tools for immediate impact! (2023-24 C)
Understanding Discord NSFW Servers A Guide for Responsible Users.pdf

Understanding Discord NSFW Servers A Guide for Responsible Users.pdf
08448380779 Call Girls In Greater Kailash - I Women Seeking Men

08448380779 Call Girls In Greater Kailash - I Women Seeking Men
What Are The Drone Anti-jamming Systems Technology?

What Are The Drone Anti-jamming Systems Technology?
IAC 2024 - IA Fast Track to Search Focused AI Solutions

IAC 2024 - IA Fast Track to Search Focused AI Solutions
Apidays Singapore 2024 - Building Digital Trust in a Digital Economy by Veron...

Apidays Singapore 2024 - Building Digital Trust in a Digital Economy by Veron...
Automating Google Workspace (GWS) & more with Apps Script

Automating Google Workspace (GWS) & more with Apps Script
Presentation on how to chat with PDF using ChatGPT code interpreter

Presentation on how to chat with PDF using ChatGPT code interpreter
Strategies for Landing an Oracle DBA Job as a Fresher

Strategies for Landing an Oracle DBA Job as a Fresher
Beyond
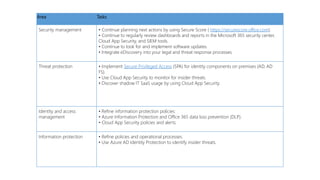
- 1. Area Tasks Security management • Continue planning next actions by using Secure Score ( https://securescore.office.com). • Continue to regularly review dashboards and reports in the Microsoft 365 security center, Cloud App Security, and SIEM tools. • Continue to look for and implement software updates. • Integrate eDiscovery into your legal and threat response processes. Threat protection • Implement Secure Privileged Access (SPA) for identity components on premises (AD, AD FS). • Use Cloud App Security to monitor for insider threats. • Discover shadow IT SaaS usage by using Cloud App Security. Identity and access management • Refine information protection policies: • Azure Information Protection and Office 365 data loss prevention (DLP). • Cloud App Security policies and alerts. Information protection • Refine policies and operational processes. • Use Azure AD Identity Protection to identify insider threats.
