Cobit v5 High Level Controls Topology
•
0 gefällt mir•39 views
Cobit v5 High Level Controls Topology
Melden
Teilen
Melden
Teilen
Downloaden Sie, um offline zu lesen
Empfohlen
Weitere ähnliche Inhalte
Was ist angesagt?
Was ist angesagt? (20)
Solving the Data Management Challenge for Healthcare

Solving the Data Management Challenge for Healthcare
Combining Patient Records, Genomic Data and Environmental Data to Enable Tran...

Combining Patient Records, Genomic Data and Environmental Data to Enable Tran...
Big Data Expo 2015 - Trillium software Big Data and the Data Quality

Big Data Expo 2015 - Trillium software Big Data and the Data Quality
Mergers, acquisitions, and partnerships dramatically reducing it consolidati...

Mergers, acquisitions, and partnerships dramatically reducing it consolidati...
Data Science & Analytics – New approaches and capabilities for driving busine...

Data Science & Analytics – New approaches and capabilities for driving busine...
Development and implementation of metrics for information security risk asses...

Development and implementation of metrics for information security risk asses...
Data Quality - Standards and Application to Open Data

Data Quality - Standards and Application to Open Data
Ähnlich wie Cobit v5 High Level Controls Topology
PPT TCA, SIGMA Workshop on Digital Auditing for SAIs, Skopje, November 2019 

PPT TCA, SIGMA Workshop on Digital Auditing for SAIs, Skopje, November 2019 Support for Improvement in Governance and Management SIGMA
Ähnlich wie Cobit v5 High Level Controls Topology (20)
Thierry Brunet - IT best practices & frameworks overview

Thierry Brunet - IT best practices & frameworks overview
Seminar IT Service Management pada Perhotelan 8 november 2013

Seminar IT Service Management pada Perhotelan 8 november 2013
Information Security Program & PCI Compliance Planning for your Business

Information Security Program & PCI Compliance Planning for your Business
PPT TCA, SIGMA Workshop on Digital Auditing for SAIs, Skopje, November 2019 

PPT TCA, SIGMA Workshop on Digital Auditing for SAIs, Skopje, November 2019
Mehr von Jason Rusch - CISSP CGEIT CISM CISA GNSA
Mehr von Jason Rusch - CISSP CGEIT CISM CISA GNSA (20)
Information_Governance_Risk_Compliance_Frameworks (v5)

Information_Governance_Risk_Compliance_Frameworks (v5)
Kürzlich hochgeladen
Kürzlich hochgeladen (20)
MONA 98765-12871 CALL GIRLS IN LUDHIANA LUDHIANA CALL GIRL

MONA 98765-12871 CALL GIRLS IN LUDHIANA LUDHIANA CALL GIRL
Value Proposition canvas- Customer needs and pains

Value Proposition canvas- Customer needs and pains
Best VIP Call Girls Noida Sector 40 Call Me: 8448380779

Best VIP Call Girls Noida Sector 40 Call Me: 8448380779
The Path to Product Excellence: Avoiding Common Pitfalls and Enhancing Commun...

The Path to Product Excellence: Avoiding Common Pitfalls and Enhancing Commun...
Understanding the Pakistan Budgeting Process: Basics and Key Insights

Understanding the Pakistan Budgeting Process: Basics and Key Insights
7.pdf This presentation captures many uses and the significance of the number...

7.pdf This presentation captures many uses and the significance of the number...
Ensure the security of your HCL environment by applying the Zero Trust princi...

Ensure the security of your HCL environment by applying the Zero Trust princi...
Enhancing and Restoring Safety & Quality Cultures - Dave Litwiller - May 2024...

Enhancing and Restoring Safety & Quality Cultures - Dave Litwiller - May 2024...
Call Girls In Holiday Inn Express Gurugram➥99902@11544 ( Best price)100% Genu...

Call Girls In Holiday Inn Express Gurugram➥99902@11544 ( Best price)100% Genu...
Call Girls in Delhi, Escort Service Available 24x7 in Delhi 959961-/-3876

Call Girls in Delhi, Escort Service Available 24x7 in Delhi 959961-/-3876
Lucknow 💋 Escorts in Lucknow - 450+ Call Girl Cash Payment 8923113531 Neha Th...

Lucknow 💋 Escorts in Lucknow - 450+ Call Girl Cash Payment 8923113531 Neha Th...
9599632723 Top Call Girls in Delhi at your Door Step Available 24x7 Delhi

9599632723 Top Call Girls in Delhi at your Door Step Available 24x7 Delhi
RSA Conference Exhibitor List 2024 - Exhibitors Data

RSA Conference Exhibitor List 2024 - Exhibitors Data
Call Girls Jp Nagar Just Call 👗 7737669865 👗 Top Class Call Girl Service Bang...

Call Girls Jp Nagar Just Call 👗 7737669865 👗 Top Class Call Girl Service Bang...
Call Girls In DLf Gurgaon ➥99902@11544 ( Best price)100% Genuine Escort In 24...

Call Girls In DLf Gurgaon ➥99902@11544 ( Best price)100% Genuine Escort In 24...
VIP Call Girls Gandi Maisamma ( Hyderabad ) Phone 8250192130 | ₹5k To 25k Wit...

VIP Call Girls Gandi Maisamma ( Hyderabad ) Phone 8250192130 | ₹5k To 25k Wit...
Cobit v5 High Level Controls Topology
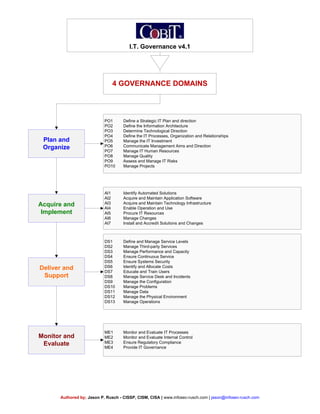
- 1. I.T. Governance v4.1 4 GOVERNANCE DOMAINS Monitor and Evaluate Acquire and Implement Plan and Organize Deliver and Support PO1 Define a Strategic IT Plan and direction PO2 Define the Information Architecture PO3 Determine Technological Direction PO4 Define the IT Processes, Organization and Relationships PO5 Manage the IT Investment PO6 Communicate Management Aims and Direction PO7 Manage IT Human Resources PO8 Manage Quality PO9 Assess and Manage IT Risks PO10 Manage Projects AI1 Identify Automated Solutions AI2 Acquire and Maintain Application Software AI3 Acquire and Maintain Technology Infrastructure AI4 Enable Operation and Use AI5 Procure IT Resources AI6 Manage Changes AI7 Install and Accredit Solutions and Changes ME1 Monitor and Evaluate IT Processes ME2 Monitor and Evaluate Internal Control ME3 Ensure Regulatory Compliance ME4 Provide IT Governance DS1 Define and Manage Service Levels DS2 Manage Third-party Services DS3 Manage Performance and Capacity DS4 Ensure Continuous Service DS5 Ensure Systems Security DS6 Identify and Allocate Costs DS7 Educate and Train Users DS8 Manage Service Desk and Incidents DS9 Manage the Configuration DS10 Manage Problems DS11 Manage Data DS12 Manage the Physical Environment DS13 Manage Operations Authored by; Jason P. Rusch - CISSP, CISM, CISA | www.infosec-rusch.com | jason@infosec-rusch.com
