Symantec Technical Services Infographic
•
0 gefällt mir•204 views
Infographic created for Symantec Technical Services. Better prepare, design, deploy, operate and optimize your security solutions.
Melden
Teilen
Melden
Teilen
Downloaden Sie, um offline zu lesen
Empfohlen
Weitere ähnliche Inhalte
Mehr von Ideba
Mehr von Ideba (20)
Greenway Health Primary Care Internists Case Study

Greenway Health Primary Care Internists Case Study
Greenway Health Valley Day and Night Clinic Case Study

Greenway Health Valley Day and Night Clinic Case Study
Kürzlich hochgeladen
Enterprise Knowledge’s Urmi Majumder, Principal Data Architecture Consultant, and Fernando Aguilar Islas, Senior Data Science Consultant, presented "Driving Behavioral Change for Information Management through Data-Driven Green Strategy" on March 27, 2024 at Enterprise Data World (EDW) in Orlando, Florida.
In this presentation, Urmi and Fernando discussed a case study describing how the information management division in a large supply chain organization drove user behavior change through awareness of the carbon footprint of their duplicated and near-duplicated content, identified via advanced data analytics. Check out their presentation to gain valuable perspectives on utilizing data-driven strategies to influence positive behavioral shifts and support sustainability initiatives within your organization.
In this session, participants gained answers to the following questions:
- What is a Green Information Management (IM) Strategy, and why should you have one?
- How can Artificial Intelligence (AI) and Machine Learning (ML) support your Green IM Strategy through content deduplication?
- How can an organization use insights into their data to influence employee behavior for IM?
- How can you reap additional benefits from content reduction that go beyond Green IM?
Driving Behavioral Change for Information Management through Data-Driven Gree...

Driving Behavioral Change for Information Management through Data-Driven Gree...Enterprise Knowledge
Kürzlich hochgeladen (20)
Mastering MySQL Database Architecture: Deep Dive into MySQL Shell and MySQL R...

Mastering MySQL Database Architecture: Deep Dive into MySQL Shell and MySQL R...
How to Troubleshoot Apps for the Modern Connected Worker

How to Troubleshoot Apps for the Modern Connected Worker
Strategies for Landing an Oracle DBA Job as a Fresher

Strategies for Landing an Oracle DBA Job as a Fresher
Apidays New York 2024 - The value of a flexible API Management solution for O...

Apidays New York 2024 - The value of a flexible API Management solution for O...
How to Troubleshoot Apps for the Modern Connected Worker

How to Troubleshoot Apps for the Modern Connected Worker
Understanding Discord NSFW Servers A Guide for Responsible Users.pdf

Understanding Discord NSFW Servers A Guide for Responsible Users.pdf
Boost PC performance: How more available memory can improve productivity

Boost PC performance: How more available memory can improve productivity
Driving Behavioral Change for Information Management through Data-Driven Gree...

Driving Behavioral Change for Information Management through Data-Driven Gree...
The 7 Things I Know About Cyber Security After 25 Years | April 2024

The 7 Things I Know About Cyber Security After 25 Years | April 2024
Scaling API-first – The story of a global engineering organization

Scaling API-first – The story of a global engineering organization
[2024]Digital Global Overview Report 2024 Meltwater.pdf![[2024]Digital Global Overview Report 2024 Meltwater.pdf](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![[2024]Digital Global Overview Report 2024 Meltwater.pdf](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
[2024]Digital Global Overview Report 2024 Meltwater.pdf
Strategize a Smooth Tenant-to-tenant Migration and Copilot Takeoff

Strategize a Smooth Tenant-to-tenant Migration and Copilot Takeoff
TrustArc Webinar - Unlock the Power of AI-Driven Data Discovery

TrustArc Webinar - Unlock the Power of AI-Driven Data Discovery
Connector Corner: Accelerate revenue generation using UiPath API-centric busi...

Connector Corner: Accelerate revenue generation using UiPath API-centric busi...
Workshop - Best of Both Worlds_ Combine KG and Vector search for enhanced R...

Workshop - Best of Both Worlds_ Combine KG and Vector search for enhanced R...
Apidays New York 2024 - Scaling API-first by Ian Reasor and Radu Cotescu, Adobe

Apidays New York 2024 - Scaling API-first by Ian Reasor and Radu Cotescu, Adobe
Advantages of Hiring UIUX Design Service Providers for Your Business

Advantages of Hiring UIUX Design Service Providers for Your Business
Symantec Technical Services Infographic
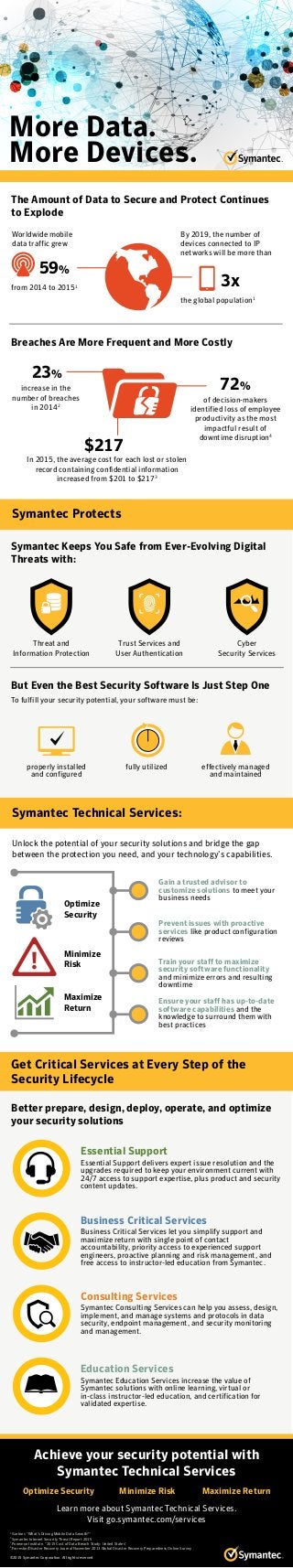
- 1. More Data. More Devices. Breaches Are More Frequent and More Costly But Even the Best Security Software Is Just Step One Better prepare, design, deploy, operate, and optimize your security solutions Symantec Keeps You Safe from Ever-Evolving Digital Threats with: Symantec Technical Services: Symantec Protects Get Critical Services at Every Step of the Security Lifecycle 3xfrom 2014 to 20151 the global population1 To fulfill your security potential, your software must be: Unlock the potential of your security solutions and bridge the gap between the protection you need, and your technology’s capabilities. 59% effectively managed and maintained fully utilizedproperly installed and configured Gain a trusted advisor to customize solutions to meet your business needs Prevent issues with proactive services like product configuration reviews Train your staff to maximize security software functionality and minimize errors and resulting downtime Ensure your staff has up-to-date software capabilities and the knowledge to surround them with best practices Achieve your security potential with Symantec Technical Services Learn more about Symantec Technical Services. Visit go.symantec.com/services Optimize Security Minimize Risk Maximize Return 1 Gartner, “What’s Driving Mobile Data Growth?” 2 Symantec Internet Security Threat Report 2015 3 Ponemon Institute, “2015 Cost of Data Breach Study: United States” 4 Forrester/Disaster Recovery Journal November 2013 Global Disaster Recovery Preparedness Online Survey ©2015 Symantec Corporation. All rights reserved. The Amount of Data to Secure and Protect Continues to Explode Worldwide mobile data traffic grew By 2019, the number of devices connected to IP networks will be more than increase in the number of breaches in 20142 23% In 2015, the average cost for each lost or stolen record containing confidential information increased from $201 to $2173 $217 72% of decision-makers identified loss of employee productivity as the most impactful result of downtime disruption4 Trust Services and User Authentication Threat and Information Protection Cyber Security Services Maximize Return Essential Support Essential Support delivers expert issue resolution and the upgrades required to keep your environment current with 24/7 access to support expertise, plus product and security content updates. Business Critical Services Business Critical Services let you simplify support and maximize return with single point of contact accountability, priority access to experienced support engineers, proactive planning and risk management, and free access to instructor-led education from Symantec. Consulting Services Symantec Consulting Services can help you assess, design, implement, and manage systems and protocols in data security, endpoint management, and security monitoring and management. Education Services Symantec Education Services increase the value of Symantec solutions with online learning, virtual or in-class instructor-led education, and certification for validated expertise. Optimize Security Minimize Risk
