#AntimalwareDay: The ESET Celebration of the Origins of Computer Defense in November 3
•
1 gefällt mir•2,626 views
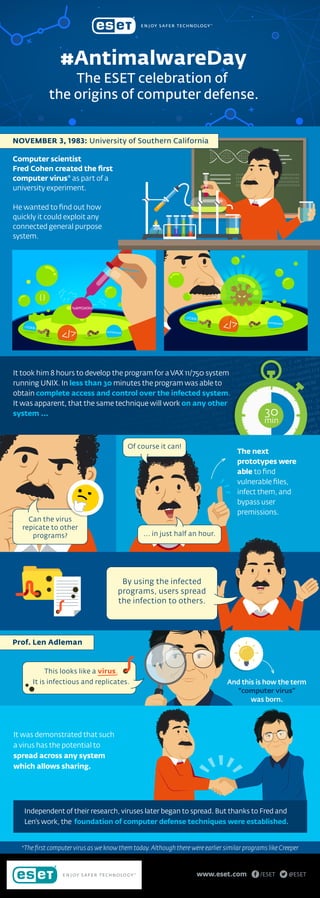
On November 3, 1983, Frederick Cohen, a student at the engineering school of the University of Southern California (USC), was sure that a malicious program could be used to exploit any connected system, but he wondered how long it would take for the code to do so. He prepared a prototype that – after eight hours of hard work on a VAX 11/750 system running Unix – was ready to be shown at the weekly security seminar he attended. It was his lecturer, Leonard Adleman, who baptized that program as a computer virus. Read more about #AntimalwareDay on WeLiveSecurity.com: https://goo.gl/QCSnc5
Melden
Teilen
Melden
Teilen
Weitere ähnliche Inhalte
Was ist angesagt?
Was ist angesagt? (8)
Ähnlich wie #AntimalwareDay: The ESET Celebration of the Origins of Computer Defense in November 3
Ähnlich wie #AntimalwareDay: The ESET Celebration of the Origins of Computer Defense in November 3 (20)
Biologically inspired defenses against computer viruses

Biologically inspired defenses against computer viruses
Mehr von ESET
Mehr von ESET (20)
How to implement a robust information security management system?

How to implement a robust information security management system?
AVAR Sydney 2014: Lemming Aid and Kool Aid: Helping the Community to Help Its...

AVAR Sydney 2014: Lemming Aid and Kool Aid: Helping the Community to Help Its...
ESET Quick Guide to the EU General Data Protection Regulation

ESET Quick Guide to the EU General Data Protection Regulation
Unpack your troubles*: .NET packer tricks and countermeasures

Unpack your troubles*: .NET packer tricks and countermeasures
ESET: #DoMore With Our Comprehensive Range of Business Products

ESET: #DoMore With Our Comprehensive Range of Business Products
ESET: Delivering Benefits to Medium and Large Businesses

ESET: Delivering Benefits to Medium and Large Businesses
Learn more about ESET and our soulutions for mobile platforms

Learn more about ESET and our soulutions for mobile platforms
Kürzlich hochgeladen
Hot Sexy call girls in Patel Nagar🔝 9953056974 🔝 escort Service

Hot Sexy call girls in Patel Nagar🔝 9953056974 🔝 escort Service9953056974 Low Rate Call Girls In Saket, Delhi NCR
Global Identity Enrolment and Verification Pro Solution - Cizo Technology Ser...

Global Identity Enrolment and Verification Pro Solution - Cizo Technology Ser...Cizo Technology Services
Kürzlich hochgeladen (20)
Tech Tuesday - Mastering Time Management Unlock the Power of OnePlan's Timesh...

Tech Tuesday - Mastering Time Management Unlock the Power of OnePlan's Timesh...
Hot Sexy call girls in Patel Nagar🔝 9953056974 🔝 escort Service

Hot Sexy call girls in Patel Nagar🔝 9953056974 🔝 escort Service
What is Advanced Excel and what are some best practices for designing and cre...

What is Advanced Excel and what are some best practices for designing and cre...
Global Identity Enrolment and Verification Pro Solution - Cizo Technology Ser...

Global Identity Enrolment and Verification Pro Solution - Cizo Technology Ser...
How to submit a standout Adobe Champion Application

How to submit a standout Adobe Champion Application
Taming Distributed Systems: Key Insights from Wix's Large-Scale Experience - ...

Taming Distributed Systems: Key Insights from Wix's Large-Scale Experience - ...
Recruitment Management Software Benefits (Infographic)

Recruitment Management Software Benefits (Infographic)
SpotFlow: Tracking Method Calls and States at Runtime

SpotFlow: Tracking Method Calls and States at Runtime
A healthy diet for your Java application Devoxx France.pdf

A healthy diet for your Java application Devoxx France.pdf
Introduction Computer Science - Software Design.pdf

Introduction Computer Science - Software Design.pdf
Catch the Wave: SAP Event-Driven and Data Streaming for the Intelligence Ente...

Catch the Wave: SAP Event-Driven and Data Streaming for the Intelligence Ente...
Unveiling Design Patterns: A Visual Guide with UML Diagrams

Unveiling Design Patterns: A Visual Guide with UML Diagrams
Alluxio Monthly Webinar | Cloud-Native Model Training on Distributed Data

Alluxio Monthly Webinar | Cloud-Native Model Training on Distributed Data
#AntimalwareDay: The ESET Celebration of the Origins of Computer Defense in November 3
- 1. { } </> </CODE> %APPDATA% AUTORUN.INF </> </CODE> AUTORUN.INF #AntimalwareDay The ESET celebration of the origins of computer defense. 30 min It took him 8 hours to develop the program for aVAX 11/750 system running UNIX. In less than 30 minutes the program was able to obtain complete access and control over the infected system. It was apparent, that the same technique will work on any other system ... Computer scientist Fred Cohen created the first computer virus* as part of a university experiment. He wanted to find out how quickly it could exploit any connected general purpose system. NOVEMBER 3, 1983: University of Southern California Can the virus repicate to other programs? Of course it can! ... in just half an hour. The next prototypes were able to find vulnerable files, infect them, and bypass user premissions. And this is how the term “computer virus” was born. It was demonstrated that such a virus has the potential to spread across any system which allows sharing. The first computer virus as we know them today.Although there were earlier similar programs like Creeper www.eset.com @ESET/ESET This looks like a virus. It is infectious and replicates. Prof. Len Adleman Independent of their research, viruses later began to spread. But thanks to Fred and Len's work, the foundation of computer defense techniques were established. By using the infected programs, users spread the infection to others.
