Malware and the Cost of Inactivity
•
11 gefällt mir•8,794 views
This document summarizes cybersecurity statistics from several reports published between 2013-2015. It finds that the average cost of a data breach rose to $5.9 million in 2014, with retail, financial services and healthcare being hit hardest. Mobile malware targeting Android devices increased, with web, network and email as the top infection vectors. The document also reports that 99% of cyberattacks are not detected in a timely manner, with over 2 years sometimes passing before a breach is discovered.
Melden
Teilen
Melden
Teilen
Downloaden Sie, um offline zu lesen
Empfohlen
Weitere ähnliche Inhalte
Was ist angesagt?
Was ist angesagt? (20)
Resolution - Security - Cisco Advanced Malware Protection for Endpoints - Fea...

Resolution - Security - Cisco Advanced Malware Protection for Endpoints - Fea...
Four Network Security Challenges for the Cloud Generation

Four Network Security Challenges for the Cloud Generation
Pen testing and how does it help strengthen cybersecurity

Pen testing and how does it help strengthen cybersecurity
Containing the outbreak: The healthcare security pandemic

Containing the outbreak: The healthcare security pandemic
Istr number 23 internet security threat repor 2018 symantec

Istr number 23 internet security threat repor 2018 symantec
Trend micro research covid19 threat brief summary 27 mar

Trend micro research covid19 threat brief summary 27 mar
Andere mochten auch
Andere mochten auch (18)
Infographic: Security for Mobile Service Providers

Infographic: Security for Mobile Service Providers
Cisco ISE Reduces the Attack Surface by Controlling Access

Cisco ISE Reduces the Attack Surface by Controlling Access
Modern Prospecting Techniques for Connecting with Prospects (from Sales Hacke...

Modern Prospecting Techniques for Connecting with Prospects (from Sales Hacke...
Class 1: Email Marketing Certification course: Email Marketing and Your Business

Class 1: Email Marketing Certification course: Email Marketing and Your Business
3 Proven Sales Email Templates Used by Successful Companies

3 Proven Sales Email Templates Used by Successful Companies
Identify Zero-Day Breaches with Cognitive Threat Analytics on Cisco Web Secur...

Identify Zero-Day Breaches with Cognitive Threat Analytics on Cisco Web Secur...
10 Things You Didn’t Know About Mobile Email from Litmus & HubSpot

10 Things You Didn’t Know About Mobile Email from Litmus & HubSpot
Ähnlich wie Malware and the Cost of Inactivity
Ähnlich wie Malware and the Cost of Inactivity (20)
Symantec's Internet Security Threat Report for the Government Sector

Symantec's Internet Security Threat Report for the Government Sector
Protect Your Enterprise - Check Point SandBlast Mobile

Protect Your Enterprise - Check Point SandBlast Mobile
Internet Security Threat Report 2014 :: Volume 19 Appendices - The hardcore n...

Internet Security Threat Report 2014 :: Volume 19 Appendices - The hardcore n...
Symantec Website Security Threat Report 2014 - RapidSSLOnline

Symantec Website Security Threat Report 2014 - RapidSSLOnline
Key Findings from the 2015 IBM Cyber Security Intelligence Index

Key Findings from the 2015 IBM Cyber Security Intelligence Index
PandaLabs Reveals its Predictions for Cybersecurity Trends in 2018

PandaLabs Reveals its Predictions for Cybersecurity Trends in 2018
5 Ways to Get Even More from Your IBM Security QRadar Investment in 2016

5 Ways to Get Even More from Your IBM Security QRadar Investment in 2016
5 Ways to Get Even More from Your IBM Security QRadar Investment in 2016

5 Ways to Get Even More from Your IBM Security QRadar Investment in 2016
Best practices for_implementing_security_awareness_training

Best practices for_implementing_security_awareness_training
Mehr von Cisco Security
Mehr von Cisco Security (20)
Incident Response Services Template - Cisco Security

Incident Response Services Template - Cisco Security
Infonetics Network and Content Security Vendor Scorecard

Infonetics Network and Content Security Vendor Scorecard
Gartner Newsletter: Cisco TrustSec Deployed Across Enterprise Campus, Branch ...

Gartner Newsletter: Cisco TrustSec Deployed Across Enterprise Campus, Branch ...
The Evolution of and Need for Secure Network Access

The Evolution of and Need for Secure Network Access
City of Tomorrow Builds in Next-Generation Security

City of Tomorrow Builds in Next-Generation Security
Laser Pioneer Secures Network End-to-End to Protect Assets

Laser Pioneer Secures Network End-to-End to Protect Assets
Leveraging Context-Aware Security to Safeguard Patient Data

Leveraging Context-Aware Security to Safeguard Patient Data
Kürzlich hochgeladen
Kürzlich hochgeladen (20)
Neo4j - How KGs are shaping the future of Generative AI at AWS Summit London ...

Neo4j - How KGs are shaping the future of Generative AI at AWS Summit London ...
Automating Business Process via MuleSoft Composer | Bangalore MuleSoft Meetup...

Automating Business Process via MuleSoft Composer | Bangalore MuleSoft Meetup...
08448380779 Call Girls In Diplomatic Enclave Women Seeking Men

08448380779 Call Girls In Diplomatic Enclave Women Seeking Men
The 7 Things I Know About Cyber Security After 25 Years | April 2024

The 7 Things I Know About Cyber Security After 25 Years | April 2024
Kotlin Multiplatform & Compose Multiplatform - Starter kit for pragmatics

Kotlin Multiplatform & Compose Multiplatform - Starter kit for pragmatics
The Codex of Business Writing Software for Real-World Solutions 2.pptx

The Codex of Business Writing Software for Real-World Solutions 2.pptx
Transcript: #StandardsGoals for 2024: What’s new for BISAC - Tech Forum 2024

Transcript: #StandardsGoals for 2024: What’s new for BISAC - Tech Forum 2024
FULL ENJOY 🔝 8264348440 🔝 Call Girls in Diplomatic Enclave | Delhi

FULL ENJOY 🔝 8264348440 🔝 Call Girls in Diplomatic Enclave | Delhi
Presentation on how to chat with PDF using ChatGPT code interpreter

Presentation on how to chat with PDF using ChatGPT code interpreter
Factors to Consider When Choosing Accounts Payable Services Providers.pptx

Factors to Consider When Choosing Accounts Payable Services Providers.pptx
Beyond Boundaries: Leveraging No-Code Solutions for Industry Innovation

Beyond Boundaries: Leveraging No-Code Solutions for Industry Innovation
Enhancing Worker Digital Experience: A Hands-on Workshop for Partners

Enhancing Worker Digital Experience: A Hands-on Workshop for Partners
Breaking the Kubernetes Kill Chain: Host Path Mount

Breaking the Kubernetes Kill Chain: Host Path Mount
How to Troubleshoot Apps for the Modern Connected Worker

How to Troubleshoot Apps for the Modern Connected Worker
Azure Monitor & Application Insight to monitor Infrastructure & Application

Azure Monitor & Application Insight to monitor Infrastructure & Application
[2024]Digital Global Overview Report 2024 Meltwater.pdf![[2024]Digital Global Overview Report 2024 Meltwater.pdf](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![[2024]Digital Global Overview Report 2024 Meltwater.pdf](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
[2024]Digital Global Overview Report 2024 Meltwater.pdf
Malware and the Cost of Inactivity
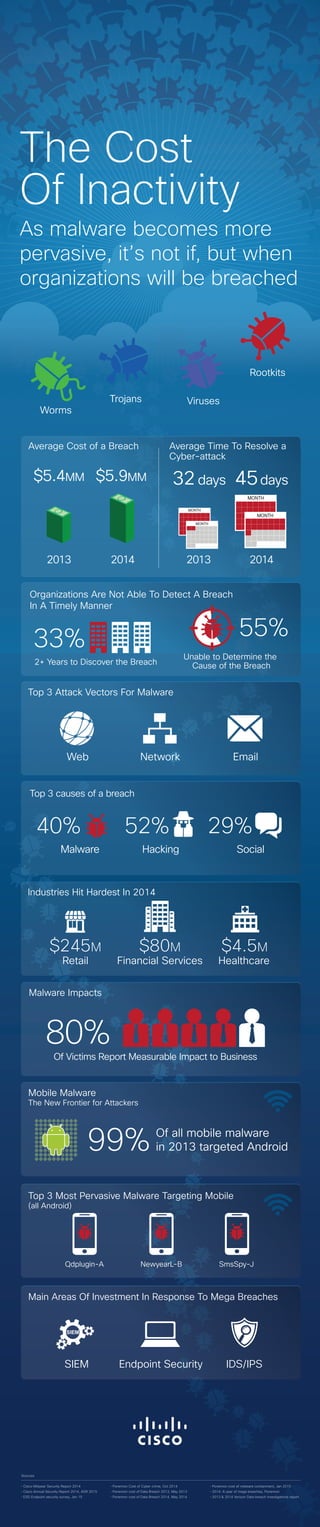
- 1. Sources • Cisco Midyear Security Report 2014 • Cisco Annual Security Report 2014, ASR 2015 • ESG Endpoint security survey, Jan 15 • Ponemon Cost of Cyber crime, Oct 2014 • Ponemon cost of Data Breach 2013, May 2013 • Ponemon cost of Data Breach 2014, May 2014 • Ponemon cost of malware containment, Jan 2015 • 2014: A year of mega breaches, Ponemon • 2013 & 2014 Verizon Data breach investigations report Mobile Malware The New Frontier for Attackers 20142013 20142013 $5.9MM$5.4MM 32days Worms Trojans Viruses Rootkits Top 3 Attack Vectors For Malware Web Network Email Qdplugin-A NewyearL-B SmsSpy-J Top 3 Most Pervasive Malware Targeting Mobile (all Android) Industries Hit Hardest In 2014 Retail $245M $80M $4.5M Financial Services Healthcare Main Areas Of Investment In Response To Mega Breaches SIEM Endpoint Security IDS/IPS Average Cost of a Breach Average Time To Resolve a Cyber-attack 99% MONTH MONTH MONTH MONTH 45days Organizations Are Not Able To Detect A Breach In A Timely Manner 2+ Years to Discover the Breach 33% 55% Unable to Determine the Cause of the Breach Of all mobile malware in 2013 targeted Android Malware Impacts Of Victims Report Measurable Impact to Business 80% The Cost Of Inactivity As malware becomes more pervasive, it’s not if, but when organizations will be breached Top 3 causes of a breach Malware Hacking Social 40% 52% 29%
