AMP Helps Cisco IT Catch 50% More Malware threats
•
2 gefällt mir•4,934 views
These statistics show how the Email Security Appliance with Advanced Malware Protection allows Cisco IT to realize its comprehensive threat-centric email security strategy. Learn more: http://cs.co/9000BD620
Melden
Teilen
Melden
Teilen
Downloaden Sie, um offline zu lesen
Empfohlen
Empfohlen
Weitere ähnliche Inhalte
Andere mochten auch
Andere mochten auch (13)
Infographic: Security for Mobile Service Providers

Infographic: Security for Mobile Service Providers
Identify Zero-Day Breaches with Cognitive Threat Analytics on Cisco Web Secur...

Identify Zero-Day Breaches with Cognitive Threat Analytics on Cisco Web Secur...
Cisco ISE Reduces the Attack Surface by Controlling Access

Cisco ISE Reduces the Attack Surface by Controlling Access
Ähnlich wie AMP Helps Cisco IT Catch 50% More Malware threats
Ähnlich wie AMP Helps Cisco IT Catch 50% More Malware threats (9)
CompTIA IT Employment Tracker - August 2016 release

CompTIA IT Employment Tracker - August 2016 release
How to Spot and Combat a Phishing Attack - Cyber Security Webinar | ControlScan

How to Spot and Combat a Phishing Attack - Cyber Security Webinar | ControlScan
Mehr von Cisco Security
Mehr von Cisco Security (17)
Incident Response Services Template - Cisco Security

Incident Response Services Template - Cisco Security
Infonetics Network and Content Security Vendor Scorecard

Infonetics Network and Content Security Vendor Scorecard
Gartner Newsletter: Cisco TrustSec Deployed Across Enterprise Campus, Branch ...

Gartner Newsletter: Cisco TrustSec Deployed Across Enterprise Campus, Branch ...
The Evolution of and Need for Secure Network Access

The Evolution of and Need for Secure Network Access
City of Tomorrow Builds in Next-Generation Security

City of Tomorrow Builds in Next-Generation Security
Laser Pioneer Secures Network End-to-End to Protect Assets

Laser Pioneer Secures Network End-to-End to Protect Assets
Leveraging Context-Aware Security to Safeguard Patient Data

Leveraging Context-Aware Security to Safeguard Patient Data
Secure, Automated Network Access for Any Device on Campus

Secure, Automated Network Access for Any Device on Campus
AMP Helps Cisco IT Catch 50% More Malware threats
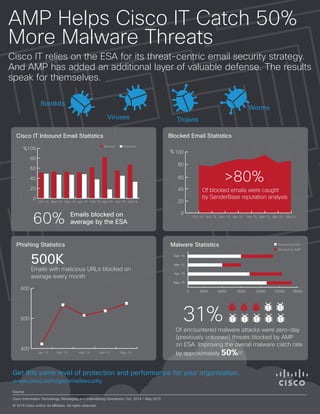
- 1. AMP Helps Cisco IT Catch 50% More Malware Threats Cisco IT relies on the ESA for its threat-centric email security strategy. And AMP has added an additional layer of valuable defense. The results speak for themselves. Source Cisco Information Technology, Messaging and Calendaring Operations. Oct. 2014 – May 2015 © 2015 Cisco and/or its affiliates. All rights reserved. www.cisco.com/go/emailsecurity Get this same level of protection and performance for your organization. Cisco IT Inbound Email Statistics Phishing Statistics Emails blocked on average by the ESA60% 0 20 40 60 80 100 Oct-14 Nov-14 Dec-14 Jan-15 Feb-15 Mar-15 Apr-15 May15 % Blocked Delivered Malware Statistics 31% 0 3000 6000 9000 12000 1800015000 Feb-15 Mar-15 Apr-15 May-15 Blocked by AMP 400 500 600 Jan-15 Feb-15 Mar-15 Apr-15 May-15 500K Emails with malicious URLs blocked on average every month Rootkits Viruses Trojans Worms 0 20 40 60 80 100% Oct-14 Nov-14 Dec-14 Jan-15 Feb-15 Mar-15 Apr-15 May15 Blocked Email Statistics >80% Of blocked emails were caught by SenderBase reputation analysis Of encountered malware attacks were zero-day (previously unknown) threats blocked by AMP on ESA. Improving the overall malware catch rate by approximately 50%!!!. Blocked by ESA
