The Enterprise Integrator - C4ISR
•
2 gefällt mir•2,869 views
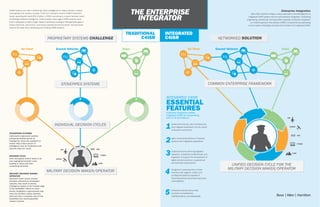
C4ISR systems are vital in delivering critical intelligence to military decision makers and operators for mission success. If the U.S. maintains current C4ISR investment levels, spending will reach $74.3 billion in 2024, according to a recent forecast report by Strategic Defense Intelligence. Unfortunately, many legacy C4ISR systems were built in stovepipes to fulfill a single mission requirement, leading to interoperability gaps in today’s technical, user-centric, and secure operational environments. Improvements need to be made when developing and fielding C4ISR systems.
Melden
Teilen
Melden
Teilen
Downloaden Sie, um offline zu lesen
Empfohlen
Weitere ähnliche Inhalte
Was ist angesagt?
Was ist angesagt? (20)
Driving the successful adoption of Microsoft Office 365

Driving the successful adoption of Microsoft Office 365
Windows 10 webinar: What’s new for IT pros Windows 10 v 1709

Windows 10 webinar: What’s new for IT pros Windows 10 v 1709
Securing your IT infrastructure with SOC-NOC collaboration TWP

Securing your IT infrastructure with SOC-NOC collaboration TWP
Revealing the State of Network Configuration Management & Automation in the E...

Revealing the State of Network Configuration Management & Automation in the E...
[INFOGRAPHIC] Accelerate Your Mobile Workforce with Citrix XenApp & XenDeskto...![[INFOGRAPHIC] Accelerate Your Mobile Workforce with Citrix XenApp & XenDeskto...](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![[INFOGRAPHIC] Accelerate Your Mobile Workforce with Citrix XenApp & XenDeskto...](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
[INFOGRAPHIC] Accelerate Your Mobile Workforce with Citrix XenApp & XenDeskto...
Cybersecurity | Very Good Security: SaaS Platform for Data Security

Cybersecurity | Very Good Security: SaaS Platform for Data Security
Partnership to Capture Indonesia ERP Cloud Trend Opportunities

Partnership to Capture Indonesia ERP Cloud Trend Opportunities
IRJET- SAAS Attacks Defense Mechanisms and Digital Forensic

IRJET- SAAS Attacks Defense Mechanisms and Digital Forensic
Andere mochten auch
Andere mochten auch (20)
Leveraging Advanced Analytics to Help Hospitals Measure Efficacy of Treatment...

Leveraging Advanced Analytics to Help Hospitals Measure Efficacy of Treatment...
Modern C4ISR Integrates, Innovates and Secures Military Networks

Modern C4ISR Integrates, Innovates and Secures Military Networks
Small Wars Journal_Identity and Biometrics Enabled Intelligence (BEI)_MAR_16

Small Wars Journal_Identity and Biometrics Enabled Intelligence (BEI)_MAR_16
Building and Managing Scalable Applications on AWS: 1 to 500K users

Building and Managing Scalable Applications on AWS: 1 to 500K users
Military_Intelligence_Professional_Bulletin_OCT_DEC_2015

Military_Intelligence_Professional_Bulletin_OCT_DEC_2015
Ähnlich wie The Enterprise Integrator - C4ISR
Session Three: Defence Authority for C4ISR

Session Three: Defence Authority for C4ISRRoyal United Services Institute for Defence and Security Studies
Deep Dive into Operational Technology Security - USCSI®.pdf

Deep Dive into Operational Technology Security - USCSI®.pdfUnited States Cybersecurity Institute (USCSI®)
Mr John Taylor - The ICT Transformation Challenge for a Transformed MOD

Mr John Taylor - The ICT Transformation Challenge for a Transformed MODRoyal United Services Institute for Defence and Security Studies
Ähnlich wie The Enterprise Integrator - C4ISR (20)
Agile and Open C4ISR Systems - Helping the Military Integrate, Innovate and S...

Agile and Open C4ISR Systems - Helping the Military Integrate, Innovate and S...
Agile and Open C4ISR Systems - Helping the Military Integrate, Innovate and S...

Agile and Open C4ISR Systems - Helping the Military Integrate, Innovate and S...
10. industrial networks safety and security tom hammond

10. industrial networks safety and security tom hammond
Secure architecture-industrial-control-systems-36327

Secure architecture-industrial-control-systems-36327
Sb securing-industrial-control-systems-with-fortinet

Sb securing-industrial-control-systems-with-fortinet
Deep Dive into Operational Technology Security - USCSI®.pdf

Deep Dive into Operational Technology Security - USCSI®.pdf
Mr John Taylor - The ICT Transformation Challenge for a Transformed MOD

Mr John Taylor - The ICT Transformation Challenge for a Transformed MOD
Reports on Industrial Control Systems’ Cyber Security

Reports on Industrial Control Systems’ Cyber Security
Mehr von Booz Allen Hamilton
Mehr von Booz Allen Hamilton (20)
You Can Hack That: How to Use Hackathons to Solve Your Toughest Challenges

You Can Hack That: How to Use Hackathons to Solve Your Toughest Challenges
Examining Flexibility in the Workplace for Working Moms

Examining Flexibility in the Workplace for Working Moms
Booz Allen's 10 Cyber Priorities for Boards of Directors

Booz Allen's 10 Cyber Priorities for Boards of Directors
Immersive Learning: The Future of Training is Here

Immersive Learning: The Future of Training is Here
Nuclear Promise: Reducing Cost While Improving Performance

Nuclear Promise: Reducing Cost While Improving Performance
Booz Allen Industrial Cybersecurity Threat Briefing

Booz Allen Industrial Cybersecurity Threat Briefing
Kürzlich hochgeladen
Kürzlich hochgeladen (20)
Web Form Automation for Bonterra Impact Management (fka Social Solutions Apri...

Web Form Automation for Bonterra Impact Management (fka Social Solutions Apri...
Powerful Google developer tools for immediate impact! (2023-24 C)

Powerful Google developer tools for immediate impact! (2023-24 C)
Apidays New York 2024 - The Good, the Bad and the Governed by David O'Neill, ...

Apidays New York 2024 - The Good, the Bad and the Governed by David O'Neill, ...
AWS Community Day CPH - Three problems of Terraform

AWS Community Day CPH - Three problems of Terraform
Why Teams call analytics are critical to your entire business

Why Teams call analytics are critical to your entire business
"I see eyes in my soup": How Delivery Hero implemented the safety system for ...

"I see eyes in my soup": How Delivery Hero implemented the safety system for ...
How to Troubleshoot Apps for the Modern Connected Worker

How to Troubleshoot Apps for the Modern Connected Worker
A Beginners Guide to Building a RAG App Using Open Source Milvus

A Beginners Guide to Building a RAG App Using Open Source Milvus
Apidays Singapore 2024 - Building Digital Trust in a Digital Economy by Veron...

Apidays Singapore 2024 - Building Digital Trust in a Digital Economy by Veron...
Strategize a Smooth Tenant-to-tenant Migration and Copilot Takeoff

Strategize a Smooth Tenant-to-tenant Migration and Copilot Takeoff
Polkadot JAM Slides - Token2049 - By Dr. Gavin Wood

Polkadot JAM Slides - Token2049 - By Dr. Gavin Wood
Boost Fertility New Invention Ups Success Rates.pdf

Boost Fertility New Invention Ups Success Rates.pdf
Apidays New York 2024 - Accelerating FinTech Innovation by Vasa Krishnan, Fin...

Apidays New York 2024 - Accelerating FinTech Innovation by Vasa Krishnan, Fin...
The Enterprise Integrator - C4ISR
- 1. C4ISR systems are vital in delivering critical intelligence to military decision makers and operators for mission success. If the U.S. maintains current C4ISR investment levels, spending will reach $74.3 billion in 2024, according to a recent forecast report by Strategic Defense Intelligence. Unfortunately, many legacy C4ISR systems were built in stovepipes to fulfill a single mission requirement, leading to interoperability gaps in today’s technical, user-centric, and secure operational environments. Improvements need to be made when developing and fielding C4ISR systems. INTEGRATED C4ISR TRADITIONAL C4ISR STOVEPIPED SYSTEMS Individually engineered systems producing isolated pieces of intelligence. Given the explosion in sensor data, critical pieces of intelligence may be overlooked and security risks can result. DECISION CYCLE Each stovepiped system leads to its own segregated decision cycle, leading to siloed and time consuming decisions. MILITARY DECISION MAKER/ OPERATOR Decisions made across mission domains, informed by stovepiped systems, may result in priority intelligence lapses at the forward edge of the battlefield. Failure to meet priority intelligence requirements may leave the decision maker/operator with less than a complete view of the battlefield that could jeopardize mission success. AIR SEA CYBER LAND SPACE INTEGRATED C4ISR ESSENTIAL FEATURESEnterprise Integration creates Integrated C4ISR by incorporating each of its five features: Government-owned, open architectures that integrate seamlessly into the overall enterprise environment. Agile, incremental delivery of modular systems with integrated capabilities. 1 2 Collective forums that bring together operators, acquisition professionals, and engineers to support the development of highly tailored solutions to operational and technical requirements. Designed-in cybersecurity to infuse solutions with organic, unified, and multilayered defense capable of thwarting attacks and preventing future vulnerabilities. Enterprise-oriented culture that promotes connectedness, interdependency, and adaptability. 3 4 5 Enterprise Integration Booz Allen Hamilton brings a unique approach to the development of Integrated C4ISR systems that we call Enterprise Integration. Combining engineering, operational, and acquisition expertise, Enterprise Integration is a holistic approach that delivers C4ISR’s full potential by addressing current system challenges and lays the foundation for Integrated C4ISR. PROPRIETARY SYSTEMS CHALLENGE STOVEPIPED SYSTEMS INDIVIDUAL DECISION CYCLES NETWORKED SOLUTION THE ENTERPRISE INTEGRATOR Air Fleet Ground Vehicles Ships Air Fleet Ground Vehicles Ships AIR SEA CYBER LAND SPACE MILITARY DECISION MAKER/OPERATOR UNIFIED DECISION CYCLE FOR THE MILITARY DECISION MAKER/OPERATOR COMMON ENTERPRISE FRAMEWORK
