The State of Network Security 2014
•
1 gefällt mir•276 views
The document discusses the key findings of a survey on network security in 2014. Some of the main points include: 1) Over 60% of organizations said that time-consuming manual processes, lack of visibility into security policies, and poor change management were their greatest challenges in managing network security. 2) Around two-thirds of organizations said that over 60% of firewall rule changes are made to enable business application connectivity. 3) Adoption of next-generation firewalls is becoming more mainstream, but cloud adoption among organizations is still relatively low, with only 16% hosting the majority of their applications in a private cloud.
Melden
Teilen
Melden
Teilen
Downloaden Sie, um offline zu lesen
Empfohlen
Transform Your Security Operations with Security Automation and Orchestration

Transform Your Security Operations with Security Automation and OrchestrationEnterprise Management Associates
Weitere ähnliche Inhalte
Was ist angesagt?
Transform Your Security Operations with Security Automation and Orchestration

Transform Your Security Operations with Security Automation and OrchestrationEnterprise Management Associates
Was ist angesagt? (20)
To Catch a Phish, or: Why You Must Automate Email Security 

To Catch a Phish, or: Why You Must Automate Email Security
Outside the (Black) Box: Protecting Core Operations in Energy

Outside the (Black) Box: Protecting Core Operations in Energy
High Performance Security Report - High Technology

High Performance Security Report - High Technology
Leaders & Laggards: The Latest Findings from the Ponemon Institute’s Study on...

Leaders & Laggards: The Latest Findings from the Ponemon Institute’s Study on...
Transform Your Security Operations with Security Automation and Orchestration

Transform Your Security Operations with Security Automation and Orchestration
Infographic: Bringing Your Cloud Visibility Back Into Focus

Infographic: Bringing Your Cloud Visibility Back Into Focus
Security from Compliance or Compliance from Security?--Metrics are the key

Security from Compliance or Compliance from Security?--Metrics are the key
SOC Services- Enhancing Organization's Cyber & Digital Security Posture

SOC Services- Enhancing Organization's Cyber & Digital Security Posture
Andere mochten auch
Andere mochten auch (13)
Developing a school-led Learning Away camping residential

Developing a school-led Learning Away camping residential
Camping residential programmes - a low cost alternative (South Hetton Learnin...

Camping residential programmes - a low cost alternative (South Hetton Learnin...
Long-term Effects of Exercise on High-density Lipoprotein Cholesterol Levels

Long-term Effects of Exercise on High-density Lipoprotein Cholesterol Levels
Ähnlich wie The State of Network Security 2014
Ähnlich wie The State of Network Security 2014 (20)
Examining the Impact of Security Management on the Business (Infographic)

Examining the Impact of Security Management on the Business (Infographic)
SVB Cybersecurity Impact on Innovation Report - Overview

SVB Cybersecurity Impact on Innovation Report - Overview
Perception Gaps in Cyber Resilience: What Are Your Blind Spots?

Perception Gaps in Cyber Resilience: What Are Your Blind Spots?
“The Impact of Mobile Devices on Information Security: A Survey of IT and Sec...

“The Impact of Mobile Devices on Information Security: A Survey of IT and Sec...
The top challenges to expect in network security in 2019 survey report 

The top challenges to expect in network security in 2019 survey report
The Stand Against Cyber Criminals Lawyers, Take The Stand Against Cyber Crimi...

The Stand Against Cyber Criminals Lawyers, Take The Stand Against Cyber Crimi...
Mehr von AlgoSec
Mehr von AlgoSec (20)
best practices-managing_security_in_the hybrid cloud

best practices-managing_security_in_the hybrid cloud
compliance made easy. pass your audits stress-free webinar

compliance made easy. pass your audits stress-free webinar
2021 02-17 v mware-algo-sec securely accelerate your digital transformation w...

2021 02-17 v mware-algo-sec securely accelerate your digital transformation w...
Compliance made easy. Pass your audits stress-free.

Compliance made easy. Pass your audits stress-free.
Cloud migrations made simpler safe secure and successful migrations

Cloud migrations made simpler safe secure and successful migrations
Build and enforce defense in depth - an algo sec-cisco tetration webinar

Build and enforce defense in depth - an algo sec-cisco tetration webinar
Radically reduce firewall rules with application-driven rule recertification

Radically reduce firewall rules with application-driven rule recertification
2020 09-30 overcoming the challenges of managing a hybrid environment - aws a...

2020 09-30 overcoming the challenges of managing a hybrid environment - aws a...
2020 04-07 webinar slides -turning network security alerts into action change...

2020 04-07 webinar slides -turning network security alerts into action change...
Cessation of Misconfigurations: Common Network Misconfiguration Risks & How t...

Cessation of Misconfigurations: Common Network Misconfiguration Risks & How t...
Put out audit security fires, pass audits -every time 

Put out audit security fires, pass audits -every time
Cisco ACI & Hybrid Networks - Breaking Down Silos with Central Policy Management

Cisco ACI & Hybrid Networks - Breaking Down Silos with Central Policy Management
2019 08-13 selecting the right security policy management solution

2019 08-13 selecting the right security policy management solution
2019 06-26 effective multi-vendor management -fortinet algo sec webinar final

2019 06-26 effective multi-vendor management -fortinet algo sec webinar final
Cisco Firepower Migration | Cisco and AlgoSec Joint Webinar

Cisco Firepower Migration | Cisco and AlgoSec Joint Webinar
2019 02-20 micro-segmentation based network security strategies (yoni geva)

2019 02-20 micro-segmentation based network security strategies (yoni geva)
Kürzlich hochgeladen
Kürzlich hochgeladen (20)
ICT role in 21st century education and its challenges

ICT role in 21st century education and its challenges
Apidays New York 2024 - Passkeys: Developing APIs to enable passwordless auth...

Apidays New York 2024 - Passkeys: Developing APIs to enable passwordless auth...
TrustArc Webinar - Unlock the Power of AI-Driven Data Discovery

TrustArc Webinar - Unlock the Power of AI-Driven Data Discovery
Apidays New York 2024 - The Good, the Bad and the Governed by David O'Neill, ...

Apidays New York 2024 - The Good, the Bad and the Governed by David O'Neill, ...
Connector Corner: Accelerate revenue generation using UiPath API-centric busi...

Connector Corner: Accelerate revenue generation using UiPath API-centric busi...
Apidays New York 2024 - Accelerating FinTech Innovation by Vasa Krishnan, Fin...

Apidays New York 2024 - Accelerating FinTech Innovation by Vasa Krishnan, Fin...
Strategize a Smooth Tenant-to-tenant Migration and Copilot Takeoff

Strategize a Smooth Tenant-to-tenant Migration and Copilot Takeoff
Apidays New York 2024 - The value of a flexible API Management solution for O...

Apidays New York 2024 - The value of a flexible API Management solution for O...
Apidays New York 2024 - Scaling API-first by Ian Reasor and Radu Cotescu, Adobe

Apidays New York 2024 - Scaling API-first by Ian Reasor and Radu Cotescu, Adobe
Cloud Frontiers: A Deep Dive into Serverless Spatial Data and FME

Cloud Frontiers: A Deep Dive into Serverless Spatial Data and FME
Introduction to Multilingual Retrieval Augmented Generation (RAG)

Introduction to Multilingual Retrieval Augmented Generation (RAG)
Cloud Frontiers: A Deep Dive into Serverless Spatial Data and FME

Cloud Frontiers: A Deep Dive into Serverless Spatial Data and FME
Spring Boot vs Quarkus the ultimate battle - DevoxxUK

Spring Boot vs Quarkus the ultimate battle - DevoxxUK
Modular Monolith - a Practical Alternative to Microservices @ Devoxx UK 2024

Modular Monolith - a Practical Alternative to Microservices @ Devoxx UK 2024
Vector Search -An Introduction in Oracle Database 23ai.pptx

Vector Search -An Introduction in Oracle Database 23ai.pptx
The State of Network Security 2014
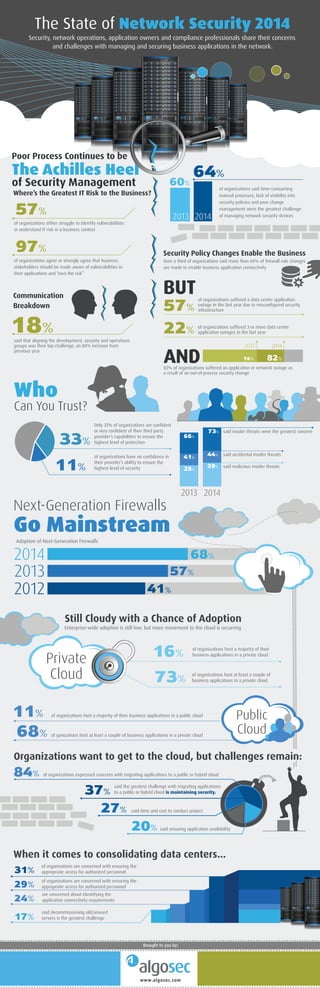
- 1. The State of Network Security 2014 Security, network operations, application owners and compliance professionals share their concerns and challenges with managing and securing business applications in the network. www.algosec.com Brought to you by: Poor Process Continues to be The Achilles Heel of Security Management Next-Generation Firewalls Go Mainstream Still Cloudy with a Chance of Adoption Organizations want to get to the cloud, but challenges remain: When it comes to consolidating data centers… Adoption of Next-Generation Firewalls Private Cloud Where’s the Greatest IT Risk to the Business? Communication Breakdown Security Policy Changes Enable the Business BUT AND of organizations said time-consuming manual processes, lack of visibility into security policies and poor change management were the greatest challenge of managing network security devices 60% 64% 20142013 of organizations either struggle to identify vulnerabilities or understand IT risk in a business context Over a third of organizations said more than 60% of firewall rule changes are made to enable business application connectivity 57% 97% of organizations agree or strongly agree that business stakeholders should be made aware of vulnerabilities in their applications and “own the risk” 18%said that aligning the development, security and operations groups was their top challenge, an 80% increase from previous year Enterprise-wide adoption is still low, but more movement to the cloud is occurring of organizations suffered a data center application outage in the last year due to misconfigured security infrastructure 82% of organizations suffered an application or network outage as a result of an out-of-process security change 57% of organizations suffered 3 or more data center application outages in the last year22% 82%76% 20142013 of organizations host a majority of their business applications in a private cloud16% Who Can You Trust? Only 33% of organizations are confident or very confident of their third party provider’s capabilities to ensure the highest level of protection of organizations have no confidence in their provider’s ability to ensure the highest level of security 33% 11% said insider threats were the greatest concern said accidental insider threats said malicious insider threats 73% 68% 66% 2014 2014 2013 2013 41% 29% 25% of organizations host at least a couple of business applications in a private cloud73% of organizations host a majority of their business applications in a public cloud11% of ganizations host at least a couple of business applications in a private cloud of organizations expressed concerns with migrating applications to a public or hybrid cloud of organizations are concerned with ensuring the appropriate access for authorized personnel said the greatest challenge with migrating applications to a public or hybrid cloud is maintaining security. 68% 84% 31% of organizations are concerned with ensuring the appropriate access for authorized personnel29% 37% said time and cost to conduct project said ensuring application availability 27% 20% 44% 57% 2012 41% Public Cloud 38% are concerned about identifying the application connectivity requirements24% said decommissioning old/unused servers is the greatest challenge17%
