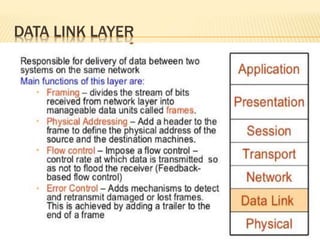
Data link layer
- 2. IEEE STANDARDS FOR LAN
- 3. IEEE STANDARDS FOR LAN LLC LLC stands for logical link control. LLC is the upper sub layer of the data link layer. It act as a interface between the media access control sub layer and the network layer.LLC basic function are flow control, error control, and framing.LLC also provides SAP services in OSI model SAP Sap stands for Service Access Point. In data link protocol LLC provides SAP services. A Service Access Point (SAP) is an identifying label for network endpoints used in Open Systems Interconnection (OSI) networking
- 4. IEEE STANDARDS FOR LAN MAC The MAC layer is responsible for moving data packets to and from one Network Interface Card (NIC) to another across a shared channel
- 5. IEEE 802.3 MAC FRAME Function of the physical layer Encoding / Decoding of signals Preamble generation/removal (for bit level synchronization) Bit transmission / reception Include specification of the transmission / medium. Function of the medium access control (MAC) layer On transmission, assemble data into a frame with address and error detection field On reception, dis assemble frame and perform address recognition and error detection. Govern access to the LAN transmission medium
- 6. IEEE 802.3 MAC FRAME Function of the logical link control LLC Provide an interface to higher layer and perform flow and error control.
- 9. STANDARD ETHERNET The original Ethernet was created in 1976 at Xerox,s palo alto Research center (PARC). Since then it has gone throw four generations.
- 10. WAN PROTOCOLS Leased lines two types of WAN encapsulation protocols 1) HDLC 2) PPP HDLC stands for High level data link control is a bit oriented synchronous data link layer protocol. Developed by the international organization for standards. HDLC main goal is to delivering data across the link without any errors HDLC uses synchronous transmission.
- 11. HDLC PROTOCOLS HDLC need to determine if the data passed the link without any errors HDLC discard the frame if error occurs To achieve this main goal HDLC defines framing
- 12. PPP PROTOCOLS Comparing the basics PPP behaves much like HDLC. PPP does discard error frames that do not pass the FCS checks. Additionally PPP uses a 2 byte protocol called Type Field Due to this 2 byte protocol called Type Field any vendor that conforms to the PPP standard can communicate with other vendor product. So when connecting a Cisco router to another vendors router over a PPP serial link, PPP is the data link layer protocol choice. This is why PPP has become the most popular and feature rich of WAN data link layer protocol.
- 13. FRAME RELAY Frame relay network are multi-access networks, which means that more then two devises can attached to the network. For Frame relay service a leased line installed between each router and a nearby frame relay switch, these links are called Access Links instead of extending from one router to other each leased lines are run from one router to a frame relay switch.
- 14. DIFFERENCE BETWEEN FRAME RELAY & PPP The difference between Frame relay and ppp links is that the equipment in the Telco actually examines the data frame sent by the router . Frame relay defines its own data link header and tailer . Each frame relay header hold an holds an address field called a data link connection identifier (DLCI)
- 15. IPV4 ADDRESSES If a devise want to communicate using TCP/IP it needs an IP Address. An IP address consist of a 32 bit number An IPv4 address is a address that uniquely and universally defines the connections of a devise ( for example a computer and a router) to the internet. 168.1.1.1 is an IP address written in dotted decimal
- 16. IPV4 ADDRESSES The actual Binary version is 168.1.1.1 10101000 . 00000001 . 00010110 . 10101100 Each decimal number in IP address is called an octet 168. 1. 1. 1 1st Octet 2nd Octet 3rd Octet 4th Octet 1 Octet = 1 Byte = 8 bits 4 Octets = 32 Bits IP address The address space (Range) of IPv4 2^32 = 4,294,967,296.
- 17. CLASSFUL ADDRESSES In classful address, the address space is divided into five classes: Class A, Class B, Class C, Class D and Class E. Range of IP Classes are Class A 0-127 1.0.0.0 to 126.0.0.0 Class B 128-191 128.0.0.0 to 191.255.0.0 Class C 192-223 192.0.0.0 to 223.255.255.0 Class D 224-239 224.0.0.0 to 239.255.255.255 Class E 240- 255 240.0.0.0 to
- 18. CLASSFUL ADDRESSES IP defines three different networks classes for addresses used by individual hosts address called Uni cast addresses Uni cast IP addresses are Class A Uni Cast Class B Uni Cast Class C Uni Cast TCP/IP defines Class D Multicast Class E Experimental
- 19. IP ADDRESSES The organization in charge of universal IP address assignment is the Internet corporation for assigned Network Numbers ( ICANN ) Administratively a central authority assigned Class A, B and C networks to companies. Class A Large Networks Class B Medium Networks Class C Small Networks
- 20. IP ADDRESSES Network and Host Part in IP Addresses Classes in binary and dotted decimal notation.
- 21. PUBLIC AND PRIVATE ADDRESSES There are two types of addresses employed on the Internet, public addresses and private addresses . Public IP Address A public IP address is the address that is assigned to a computing device to allow direct access over the Internet. A web server, email server and any server device directly accessible from the Internet are candidate for a public IP address. A public IP address is globally unique, and can only be assigned to a unique device. Private IP Address A private IP address is the address space allocated by Inter NIC to allow organizations to create their own private network. The computers, tablets and Smartphone's sitting behind your home, and the personal computers within an
- 22. SUBNETTING Creates multiple logical networks that exist within a single Class A, B, or C network. If you do not subnet, you will only be able to use one network from your Class A, B, or C network, which is unrealistic Each data link on a network must have a unique network ID, with every node on that link being a member of the same network
- 23. BENEFITS OF SUBNETTING 1) Reduced network traffic 2) Optimized network performance 3) Simplified management 4) Facilitated spanning of large geographical distances
- 24. CIDR Classless Interdomain Routing Improve address space utilization Routing scalability in the Internet For example, if an ISP owns network 172.16.0.0/16, then the ISP can offer 172.16.1.0/24, 172.16.2.0/24,and so on to customers. Yet, when advertising to other providers, the ISP only needs to advertise 172.16.0.0/16