The List of Information Security & System Security International Conference
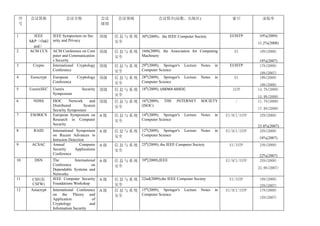
- 1. 序 会议简称 会议全称 会议 会议领域 会议简介(届数、出版社) 索引 录取率 号 级别 1 IEEE IEEE Symposium on Sec 顶级 信息与系统 30th(2009),the IEEE Computer Society EI/ISTP 10%(2009) S&P(Oakl urity and Privacy 安全 11.2%(2008) and) 2 ACM CCS ACM Conference on Com 顶级 信息与系统 16th(2009), the Association for Computing EI 18%(2008) puter and Communication 安全 Machinery s Security 18%(2007) 3 Crypto International Cryptology 顶级 信息与系统 29th(2009), Springer's Lecture Notes in EI/ISTP 17%(2008) Conference 安全 Computer Science 18%(2007) 4 Eurocrypt European Cryptology 顶级 信息与系统 28th(2009), Springer's Lecture Notes in EI 19%(2008) Conference 安全 Computer Science 19%(2008) 5 UsenixSEC Usenix Security 顶级 信息与系统 18th(2009), USENIX ASSOC ISTP 14.7%(2009) Symposium 安全 15.9%(2008) 6 NDSS ISOC Network and 顶级 信息与系统 16th(2009), THE INTERNET SOCIETY / 11.7%(2009) Distributed System 安全 (ISOC) Security Symposium 17.8%(2008) th 7 ESORICS European Symposium on A级 信息与系统 14 (2009), Springer's Lecture Notes in EI/SCI/ISTP 22%(2008) Research in Computer 安全 Computer Science Security 23.8%(2007) 8 RAID International Symposium A级 信息与系统 12th(2009), Springer's Lecture Notes in EI/SCI/ISTP 25%(2008) on Recent Advances in 安全 Computer Science Intrusion Detection 18%(2007) th 9 ACSAC Annual Computer A级 信息与系统 25 (2009), the IEEE Computer Society EI/ISTP 24%(2008) Security Applications 安全 Conference 22%(2007) 10 DSN The International A级 信息与系统 39th(2009),IEEE EI/SCI/ISTP 25%(2008) Conference on 安全 Dependable Systems and 22.6%(2007) Networks 11 CSF(原 IEEE Computer Security A级 信息与系统 22nd(2009),the IEEE Computer Society EI/ISTP 18%(2008) CSFW) Foundations Workshop 安全 25%(2007) 12 Asiacrypt International Conference A级 信息与系统 15th(2009), Springer's Lecture Notes in EI/SCI/ISTP 17%(2008) on the Theory and 安全 Computer Science Application of 15%(2007) Cryptology and Information Security
- 2. 13 AsiaCCS ACM Symposium on A级 信息与系统 4th(2009), the Association for Computing EI 22%(2008) Information, Computer 安全 Machinery and Communications 18%(2007) Security 14 ICICS International Conference A级 信息与系统 11th(2009), Springer's Lecture Notes in EI/SCI/ISTP 17.2%(2007) on Information and 安全 Computer Science 15%(2006) Communications Security 15 SecureCom IEEE Communications B级 信息与系统 5th(2009), the Association for Computing EI/ISTP 26%(2007) m Society/CreateNet 安全 Machinery Internation Conference on 25.4%(2006) Security and Privacy for Emerging Areas in Communication Networks 16 ACNS International Conference B级 信息与系统 6th(2009), Springer's Lecture Notes in EI/SCI/ISTP 22.9%(2008) on Applied Cryptography 安全 Computer Science and Network Security 12%(2007) 17 NSPW New Security Paradigms B级 信息与系统 18th(2009), the Association for Computing EI 32%(2006) Workshop 安全 Machinery 35%(2002) 18 ACISP Australasia Conference B级 信息与系统 14th(2009), Springer's Lecture Notes in EI 29%(2008) on Information Security 安全 Computer Science and Privacy 19 ISC Information Security B级 信息与系统 12th(2009), Springer's Lecture Notes in EI/ISTP 23%(2008) Conference 安全 Computer Science 25%(2007) 20 ICISC International Conference B级 信息与系统 12th(2009), Springer's Lecture Notes in EI/SCI/ISTP 22.8%(2007) on Information Security 安全 Computer Science and Cryptology 21 WSPEC Workshop on Security B级 信息与系统 / and Privacy in E- 安全 commerce 22 WiSe ACM Workshop on B级 信息与系统 5th ( 2006 ) , the Association for Computing EI 21%(2004) Wireless Security 安全 Machinery 24%(2003) 23 SASN ACM Workshop on B级 信息与系统 4th ( 2006 ) , the Association for Computing EI 19.7%(2003) Security of Ad-Hoc and 安全 Machinery Sensor Networks 24 WORM ACM Workshop on Rapid B级 信息与系统 5th(2007), the Association for Computing EI 24.3%(2005) Malcode 安全 Machinery 30%(2003)
- 3. 25 DRM ACM Workshop on B级 信息与系统 6th(2008), the Association for Computing EI 33%(2006) Digital Rights 安全 Machinery Management 26 SEC IFIP International B级 信息与系统 24th(2009), Springer SCI/ISTP 29%(2008) Information Security 安全 Conference 27 IWIA IEEE International B级 信息与系统 4th(2006), the IEEE Computer Society EI Information Assurance 安全 Workshop 28 SACMAT ACM Symposium on B级 信息与系统 14th(2009), the Association for Computing EI/SCI/ISTP 25%(2008) Access Control Models 安全 Machinery 35%(2007) and Technologies 29 DIMVA GI SIG SIDAR B级 信息与系统 6th ( 2009 ) , Springer's Lecture Notes in EI 31%(2008) Conference on Detection 安全 Computer Science of Intrusions and Malware 24.5%(2007) and Vulnerability Assessment 30 HotSec USENIX Workshop on B级 信息与系统 4th(2009), USENIX ASSOC / 19.6%(2006) Hot Topics in Security 安全 31 ISPEC Information Security B级 信息与系统 5th(2009), Springer's Lecture Notes in EI/SCI/ISTP 29%(2008) Practice and Experience 安全 Computer Science 33%(2005) Conference
