Mobility And Mobile I Pv4
•Als PPT, PDF herunterladen•
1 gefällt mir•706 views
Unit 3 Of ACN
Melden
Teilen
Melden
Teilen
Weitere ähnliche Inhalte
Was ist angesagt?
Was ist angesagt? (20)
Performance of Various Mobile IP Protocols and Security Considerations

Performance of Various Mobile IP Protocols and Security Considerations
Tracing An IP Address or Domain Name by Raghu Khimani

Tracing An IP Address or Domain Name by Raghu Khimani
Andere mochten auch
Andere mochten auch (20)
Computer Security Lecture 3: Classical Encryption Techniques 2

Computer Security Lecture 3: Classical Encryption Techniques 2
Computer Security Lecture 2: Classical Encryption Techniques 1

Computer Security Lecture 2: Classical Encryption Techniques 1
Classical Encryption Techniques in Network Security

Classical Encryption Techniques in Network Security
IS Unit 1_Conventional Encryption_Classical Encryption Techniques

IS Unit 1_Conventional Encryption_Classical Encryption Techniques
Revista qué pasa ranking UNIVERSIDADES 2010. (1de2)

Revista qué pasa ranking UNIVERSIDADES 2010. (1de2)
Ähnlich wie Mobility And Mobile I Pv4
Ähnlich wie Mobility And Mobile I Pv4 (20)
Mehr von Ram Dutt Shukla
Mehr von Ram Dutt Shukla (20)
Kürzlich hochgeladen
+971581248768>> SAFE AND ORIGINAL ABORTION PILLS FOR SALE IN DUBAI AND ABUDHA...

+971581248768>> SAFE AND ORIGINAL ABORTION PILLS FOR SALE IN DUBAI AND ABUDHA...?#DUbAI#??##{{(☎️+971_581248768%)**%*]'#abortion pills for sale in dubai@
Driving Behavioral Change for Information Management through Data-Driven Gree...

Driving Behavioral Change for Information Management through Data-Driven Gree...Enterprise Knowledge
Kürzlich hochgeladen (20)
ProductAnonymous-April2024-WinProductDiscovery-MelissaKlemke

ProductAnonymous-April2024-WinProductDiscovery-MelissaKlemke
Tech Trends Report 2024 Future Today Institute.pdf

Tech Trends Report 2024 Future Today Institute.pdf
How to Troubleshoot Apps for the Modern Connected Worker

How to Troubleshoot Apps for the Modern Connected Worker
+971581248768>> SAFE AND ORIGINAL ABORTION PILLS FOR SALE IN DUBAI AND ABUDHA...

+971581248768>> SAFE AND ORIGINAL ABORTION PILLS FOR SALE IN DUBAI AND ABUDHA...
From Event to Action: Accelerate Your Decision Making with Real-Time Automation

From Event to Action: Accelerate Your Decision Making with Real-Time Automation
Powerful Google developer tools for immediate impact! (2023-24 C)

Powerful Google developer tools for immediate impact! (2023-24 C)
How to Troubleshoot Apps for the Modern Connected Worker

How to Troubleshoot Apps for the Modern Connected Worker
Driving Behavioral Change for Information Management through Data-Driven Gree...

Driving Behavioral Change for Information Management through Data-Driven Gree...
Strategies for Landing an Oracle DBA Job as a Fresher

Strategies for Landing an Oracle DBA Job as a Fresher
Scaling API-first – The story of a global engineering organization

Scaling API-first – The story of a global engineering organization
Tata AIG General Insurance Company - Insurer Innovation Award 2024

Tata AIG General Insurance Company - Insurer Innovation Award 2024
HTML Injection Attacks: Impact and Mitigation Strategies

HTML Injection Attacks: Impact and Mitigation Strategies
Workshop - Best of Both Worlds_ Combine KG and Vector search for enhanced R...

Workshop - Best of Both Worlds_ Combine KG and Vector search for enhanced R...
[2024]Digital Global Overview Report 2024 Meltwater.pdf![[2024]Digital Global Overview Report 2024 Meltwater.pdf](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![[2024]Digital Global Overview Report 2024 Meltwater.pdf](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
[2024]Digital Global Overview Report 2024 Meltwater.pdf
Apidays New York 2024 - The value of a flexible API Management solution for O...

Apidays New York 2024 - The value of a flexible API Management solution for O...
Mobility And Mobile I Pv4
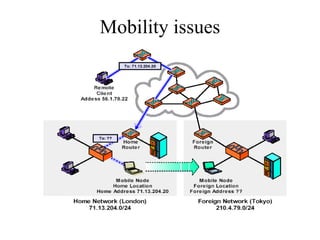
- 12. Mobile IP Mobility Agent Advertisement Extension Format
- 18. Mobile tunneling Triangle path
