Melden
Teilen
Weitere ähnliche Inhalte
Was ist angesagt?
Was ist angesagt? (20)
VPN, Its Types,VPN Protocols,Configuration and Benefits

VPN, Its Types,VPN Protocols,Configuration and Benefits
Andere mochten auch
Andere mochten auch (16)
Chapter 3: Block Ciphers and the Data Encryption Standard

Chapter 3: Block Ciphers and the Data Encryption Standard
The evolution of mobile technologies 1 g to 4g to lte

The evolution of mobile technologies 1 g to 4g to lte
Ähnlich wie Virtual Private Network
Ähnlich wie Virtual Private Network (20)
Kürzlich hochgeladen
Driving Behavioral Change for Information Management through Data-Driven Gree...

Driving Behavioral Change for Information Management through Data-Driven Gree...Enterprise Knowledge
+971581248768>> SAFE AND ORIGINAL ABORTION PILLS FOR SALE IN DUBAI AND ABUDHA...

+971581248768>> SAFE AND ORIGINAL ABORTION PILLS FOR SALE IN DUBAI AND ABUDHA...?#DUbAI#??##{{(☎️+971_581248768%)**%*]'#abortion pills for sale in dubai@
Kürzlich hochgeladen (20)
Apidays New York 2024 - The value of a flexible API Management solution for O...

Apidays New York 2024 - The value of a flexible API Management solution for O...
Driving Behavioral Change for Information Management through Data-Driven Gree...

Driving Behavioral Change for Information Management through Data-Driven Gree...
Mastering MySQL Database Architecture: Deep Dive into MySQL Shell and MySQL R...

Mastering MySQL Database Architecture: Deep Dive into MySQL Shell and MySQL R...
Tech Trends Report 2024 Future Today Institute.pdf

Tech Trends Report 2024 Future Today Institute.pdf
TrustArc Webinar - Stay Ahead of US State Data Privacy Law Developments

TrustArc Webinar - Stay Ahead of US State Data Privacy Law Developments
Handwritten Text Recognition for manuscripts and early printed texts

Handwritten Text Recognition for manuscripts and early printed texts
Exploring the Future Potential of AI-Enabled Smartphone Processors

Exploring the Future Potential of AI-Enabled Smartphone Processors
Apidays New York 2024 - Scaling API-first by Ian Reasor and Radu Cotescu, Adobe

Apidays New York 2024 - Scaling API-first by Ian Reasor and Radu Cotescu, Adobe
Workshop - Best of Both Worlds_ Combine KG and Vector search for enhanced R...

Workshop - Best of Both Worlds_ Combine KG and Vector search for enhanced R...
Apidays Singapore 2024 - Building Digital Trust in a Digital Economy by Veron...

Apidays Singapore 2024 - Building Digital Trust in a Digital Economy by Veron...
Strategize a Smooth Tenant-to-tenant Migration and Copilot Takeoff

Strategize a Smooth Tenant-to-tenant Migration and Copilot Takeoff
Bajaj Allianz Life Insurance Company - Insurer Innovation Award 2024

Bajaj Allianz Life Insurance Company - Insurer Innovation Award 2024
+971581248768>> SAFE AND ORIGINAL ABORTION PILLS FOR SALE IN DUBAI AND ABUDHA...

+971581248768>> SAFE AND ORIGINAL ABORTION PILLS FOR SALE IN DUBAI AND ABUDHA...
How to Troubleshoot Apps for the Modern Connected Worker

How to Troubleshoot Apps for the Modern Connected Worker
Virtual Private Network
- 2. Flow of presentation Defining VPN Characteristics Types of VPN VPN Technologies Benefits of VPN Tradeoffs in VPN
- 3. What is VPN? A VPN is a private network that uses a public network (usually the Internet) to connect remote sites or users together.
- 6. User VPN Remote vpn client Internet Tunnel formation Two way communication Vpn gateway Organization n User−to−LAN connection used by a company that has employees who need to connect to the private network from various remote locations.
- 7. Site VPN Internet Tunnel formation Two way communication Vpn gateway Organization n Remote site Through the use of dedicated equipment and large-scale encryption, a company can connect multiple fixed sites over a public network such as the Internet. Each site needs only a local connection to the same public network
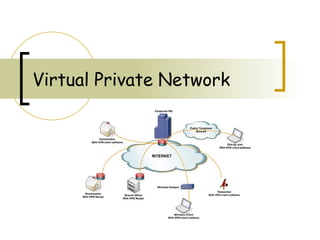
- 8. User and site vpn connection
- 11. Tradeoffs of VPN internet Internal network User computer Vpn channel Trojan horse sends traffic to internal n over VPN Vpn Server Attacker communicates with the trojan horse via the internet TCPP stack VPN s Trojan horse
- 12. Submitted by- Ashish Goel Shippi chandak Sujata Shreya Tanu venus