More Related Content
What's hot (20)
VPN, Its Types,VPN Protocols,Configuration and Benefits

VPN, Its Types,VPN Protocols,Configuration and Benefits
Viewers also liked
Viewers also liked (16)
Chapter 3: Block Ciphers and the Data Encryption Standard

Chapter 3: Block Ciphers and the Data Encryption Standard
The evolution of mobile technologies 1 g to 4g to lte

The evolution of mobile technologies 1 g to 4g to lte
Similar to Virtual Private Network
Similar to Virtual Private Network (20)
Recently uploaded
Recently uploaded (20)
Frisco Automating Purchase Orders with MuleSoft IDP- May 10th, 2024.pptx.pdf

Frisco Automating Purchase Orders with MuleSoft IDP- May 10th, 2024.pptx.pdf
Continuing Bonds Through AI: A Hermeneutic Reflection on Thanabots

Continuing Bonds Through AI: A Hermeneutic Reflection on Thanabots
The Zero-ETL Approach: Enhancing Data Agility and Insight

The Zero-ETL Approach: Enhancing Data Agility and Insight
Observability Concepts EVERY Developer Should Know (DevOpsDays Seattle)

Observability Concepts EVERY Developer Should Know (DevOpsDays Seattle)
Human Expert Website Manual WCAG 2.0 2.1 2.2 Audit - Digital Accessibility Au...

Human Expert Website Manual WCAG 2.0 2.1 2.2 Audit - Digital Accessibility Au...
State of the Smart Building Startup Landscape 2024!

State of the Smart Building Startup Landscape 2024!
Navigating the Large Language Model choices_Ravi Daparthi

Navigating the Large Language Model choices_Ravi Daparthi
Stronger Together: Developing an Organizational Strategy for Accessible Desig...

Stronger Together: Developing an Organizational Strategy for Accessible Desig...
How to Check CNIC Information Online with Pakdata cf

How to Check CNIC Information Online with Pakdata cf
WebRTC and SIP not just audio and video @ OpenSIPS 2024

WebRTC and SIP not just audio and video @ OpenSIPS 2024
AI+A11Y 11MAY2024 HYDERBAD GAAD 2024 - HelloA11Y (11 May 2024)

AI+A11Y 11MAY2024 HYDERBAD GAAD 2024 - HelloA11Y (11 May 2024)
UiPath manufacturing technology benefits and AI overview

UiPath manufacturing technology benefits and AI overview
Harnessing Passkeys in the Battle Against AI-Powered Cyber Threats.pptx

Harnessing Passkeys in the Battle Against AI-Powered Cyber Threats.pptx
ChatGPT and Beyond - Elevating DevOps Productivity

ChatGPT and Beyond - Elevating DevOps Productivity
JavaScript Usage Statistics 2024 - The Ultimate Guide

JavaScript Usage Statistics 2024 - The Ultimate Guide
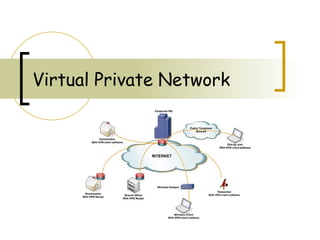
Virtual Private Network
- 2. Flow of presentation Defining VPN Characteristics Types of VPN VPN Technologies Benefits of VPN Tradeoffs in VPN
- 3. What is VPN? A VPN is a private network that uses a public network (usually the Internet) to connect remote sites or users together.
- 6. User VPN Remote vpn client Internet Tunnel formation Two way communication Vpn gateway Organization n User−to−LAN connection used by a company that has employees who need to connect to the private network from various remote locations.
- 7. Site VPN Internet Tunnel formation Two way communication Vpn gateway Organization n Remote site Through the use of dedicated equipment and large-scale encryption, a company can connect multiple fixed sites over a public network such as the Internet. Each site needs only a local connection to the same public network
- 8. User and site vpn connection
- 11. Tradeoffs of VPN internet Internal network User computer Vpn channel Trojan horse sends traffic to internal n over VPN Vpn Server Attacker communicates with the trojan horse via the internet TCPP stack VPN s Trojan horse
- 12. Submitted by- Ashish Goel Shippi chandak Sujata Shreya Tanu venus