What is a Rainbow Table?
•Als PPTX, PDF herunterladen•
2 gefällt mir•6,019 views
this presentation introduces you an advanced way of decryption of data
Melden
Teilen
Melden
Teilen
Empfohlen
Weitere ähnliche Inhalte
Was ist angesagt?
Was ist angesagt? (20)
Andere mochten auch
Andere mochten auch (11)
Password Storage And Attacking In PHP - PHP Argentina

Password Storage And Attacking In PHP - PHP Argentina
Mehr von Vahid Saffarian
Mehr von Vahid Saffarian (12)
Kürzlich hochgeladen
Kürzlich hochgeladen (20)
[2024]Digital Global Overview Report 2024 Meltwater.pdf![[2024]Digital Global Overview Report 2024 Meltwater.pdf](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![[2024]Digital Global Overview Report 2024 Meltwater.pdf](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
[2024]Digital Global Overview Report 2024 Meltwater.pdf
How to Remove Document Management Hurdles with X-Docs?

How to Remove Document Management Hurdles with X-Docs?
From Event to Action: Accelerate Your Decision Making with Real-Time Automation

From Event to Action: Accelerate Your Decision Making with Real-Time Automation
Neo4j - How KGs are shaping the future of Generative AI at AWS Summit London ...

Neo4j - How KGs are shaping the future of Generative AI at AWS Summit London ...
IAC 2024 - IA Fast Track to Search Focused AI Solutions

IAC 2024 - IA Fast Track to Search Focused AI Solutions
Swan(sea) Song – personal research during my six years at Swansea ... and bey...

Swan(sea) Song – personal research during my six years at Swansea ... and bey...
08448380779 Call Girls In Greater Kailash - I Women Seeking Men

08448380779 Call Girls In Greater Kailash - I Women Seeking Men
The 7 Things I Know About Cyber Security After 25 Years | April 2024

The 7 Things I Know About Cyber Security After 25 Years | April 2024
Transforming Data Streams with Kafka Connect: An Introduction to Single Messa...

Transforming Data Streams with Kafka Connect: An Introduction to Single Messa...
Kotlin Multiplatform & Compose Multiplatform - Starter kit for pragmatics

Kotlin Multiplatform & Compose Multiplatform - Starter kit for pragmatics
Tech-Forward - Achieving Business Readiness For Copilot in Microsoft 365

Tech-Forward - Achieving Business Readiness For Copilot in Microsoft 365
#StandardsGoals for 2024: What’s new for BISAC - Tech Forum 2024

#StandardsGoals for 2024: What’s new for BISAC - Tech Forum 2024
Scaling API-first – The story of a global engineering organization

Scaling API-first – The story of a global engineering organization
Injustice - Developers Among Us (SciFiDevCon 2024)

Injustice - Developers Among Us (SciFiDevCon 2024)
Breaking the Kubernetes Kill Chain: Host Path Mount

Breaking the Kubernetes Kill Chain: Host Path Mount
What is a Rainbow Table?
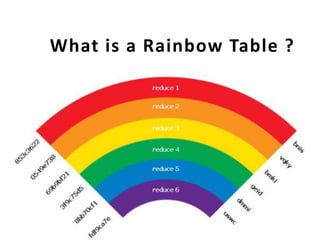
- 1. What is a Rainbow Table ?
- 2. A rainbow table is a precomputed table for reversing cryptographic hash functions, usually for cracking password hashes.
- 3. Tables are usually used in recovering a plaintext password up to a certain length consisting of a limited set of characters.
- 4. It is a practical example of a space/time trade- off, using more computer processing time at the cost of less storage when calculating a hash on every attempt, or less processing time and more storage when compared to a simple lookup table with one entry per hash.
- 6. Use of a key derivation function that employs a salt makes this attack infeasible.
- 7. Rainbow tables are an application of an earlier, simpler algorithm by Martin Hellman
