ThreatMetrix Fraud Network Presentation
•Als PPTX, PDF herunterladen•
3 gefällt mir•1,867 views
Melden
Teilen
Melden
Teilen
Empfohlen
Weitere ähnliche Inhalte
Was ist angesagt?
Was ist angesagt? (11)
securing-consumer-portals-consumer-access-management-as-business-driver-and-p...

securing-consumer-portals-consumer-access-management-as-business-driver-and-p...
Weak Links: Cyber Attacks in the News & How to Protect Your Assets

Weak Links: Cyber Attacks in the News & How to Protect Your Assets
Andere mochten auch
Andere mochten auch (9)
Threatmetrix rスレットメトリックス・グローバル共有インテリジェンスによる VISA 顧客認証サービス(VCAS)のサポート

Threatmetrix rスレットメトリックス・グローバル共有インテリジェンスによる VISA 顧客認証サービス(VCAS)のサポート
Threatmetrix スレットメトリックス・グローバル共有インテリジェンスによる VISA 顧客認証サービス(VCAS)のサポート

Threatmetrix スレットメトリックス・グローバル共有インテリジェンスによる VISA 顧客認証サービス(VCAS)のサポート
AWS Enterprise Day | Securing your Web Applications in the Cloud

AWS Enterprise Day | Securing your Web Applications in the Cloud
Ähnlich wie ThreatMetrix Fraud Network Presentation
10 Essential Strategies to Safeguard Your Business from Credit Card Fraud 1.pdf

10 Essential Strategies to Safeguard Your Business from Credit Card Fraud 1.pdfMerchantech - Payment Processing Services
Ähnlich wie ThreatMetrix Fraud Network Presentation (20)
Verified Stripe Account Buy Verified Stripe Account

Verified Stripe Account Buy Verified Stripe Account
Trading Online – Getting started and how to grow your business

Trading Online – Getting started and how to grow your business
Ultimate Guide on Card Not Present (CNP) Fraud.pptx

Ultimate Guide on Card Not Present (CNP) Fraud.pptx
3 Ways Fraudsters Compromise AP Security and Controls and How You Can Mitigat...

3 Ways Fraudsters Compromise AP Security and Controls and How You Can Mitigat...
10 Essential Strategies to Safeguard Your Business from Credit Card Fraud 1.pdf

10 Essential Strategies to Safeguard Your Business from Credit Card Fraud 1.pdf
Kürzlich hochgeladen
Kürzlich hochgeladen (20)
08448380779 Call Girls In Friends Colony Women Seeking Men

08448380779 Call Girls In Friends Colony Women Seeking Men
IAC 2024 - IA Fast Track to Search Focused AI Solutions

IAC 2024 - IA Fast Track to Search Focused AI Solutions
Injustice - Developers Among Us (SciFiDevCon 2024)

Injustice - Developers Among Us (SciFiDevCon 2024)
08448380779 Call Girls In Civil Lines Women Seeking Men

08448380779 Call Girls In Civil Lines Women Seeking Men
Automating Business Process via MuleSoft Composer | Bangalore MuleSoft Meetup...

Automating Business Process via MuleSoft Composer | Bangalore MuleSoft Meetup...
Swan(sea) Song – personal research during my six years at Swansea ... and bey...

Swan(sea) Song – personal research during my six years at Swansea ... and bey...
WhatsApp 9892124323 ✓Call Girls In Kalyan ( Mumbai ) secure service

WhatsApp 9892124323 ✓Call Girls In Kalyan ( Mumbai ) secure service
Tech-Forward - Achieving Business Readiness For Copilot in Microsoft 365

Tech-Forward - Achieving Business Readiness For Copilot in Microsoft 365
The 7 Things I Know About Cyber Security After 25 Years | April 2024

The 7 Things I Know About Cyber Security After 25 Years | April 2024
[2024]Digital Global Overview Report 2024 Meltwater.pdf![[2024]Digital Global Overview Report 2024 Meltwater.pdf](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![[2024]Digital Global Overview Report 2024 Meltwater.pdf](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
[2024]Digital Global Overview Report 2024 Meltwater.pdf
Transforming Data Streams with Kafka Connect: An Introduction to Single Messa...

Transforming Data Streams with Kafka Connect: An Introduction to Single Messa...
08448380779 Call Girls In Diplomatic Enclave Women Seeking Men

08448380779 Call Girls In Diplomatic Enclave Women Seeking Men
ThreatMetrix Fraud Network Presentation
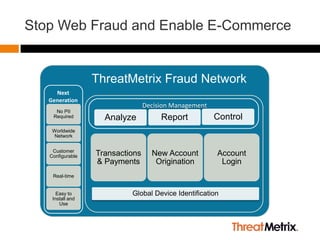
- 1. Stop Web Fraud and Enable E-Commerce ThreatMetrix Fraud Network Next Generation
- 2. Detect Stolen and Hijacked Credentials Transactions New Accounts Logins Identity Velocity Device Anomaly Access Anomaly
- 3. Authenticate New and Returning Customers Transactions New Accounts Logins
- 4. ThreatMetrix Customer Problems Transactions New Accounts Login Account Hijack Prevention Compromised Device Detection Synthetic and Stolen Identity Protection Chargeback and Loss Prevention Financial Services Gaming & Currency CPA & Alt payments Social Networks Merchants & Online Services Fraud Management is Strategic to Business Operations
- 9. Out of Band & Two Factor Authentication inconvenient or impracticalIntelligence trapped within departments & organizations
- 16. Protect BrandNon-invasive, Real-time, Enterprise & Global Intelligence, with no PII Leakage
- 17. ThreatMetrix Fraud Network Transactions New Accounts Logins Secure Web API: Transaction Details & AnonymizedCredentials SaaS Portal (Analyze, Report, Control) Real-time Rules Engine with Behavior & Pattern Matching Transaction Intelligence Network Global Device Identification
- 20. Proxy Piercing & Botnet detection
- 22. High speed matching/storage framework on commodity hardware
- 23. Packet Signature Detection combined with context data
- 24. Scalable, secure Inter-process communication platform
