Enterprise API Security & Data Loss Prevention - Intel
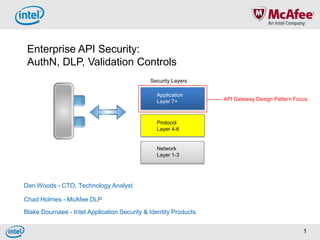
- 1. Enterprise API Security: AuthN, DLP, Validation Controls Security Layers Application Layer 7+ API Gateway Design Pattern Focus Protocol Layer 4-6 Network Layer 1-3 Dan Woods - CTO, Technology Analyst Chad Holmes - McAfee DLP Blake Dournaee - Intel Application Security & Identity Products 1
- 2. Today’s Agenda • Why are APIs en vogue • API Security Layers - What applies today? • Why Threat Protection & DLP are Important • Blending API Gateway & DLP Deployments Agenda • Example technical solution flows 2
- 3. Dan Woods CTO, Technology Analyst 3
- 4. Who is Dan Woods? Over a Dozen Books on Enterprise Architecture 4
- 5. APIs are In Vogue According to Programmable Web 5
- 6. API Security Layers to Consider Token Authentication of Payload • Users and data • OAuth AuthN at time of app handshake • X509 Cert, SAML, SSL Datacenter Data Users Authorization • XACML • Decoupled from app point of use Trust Control Perimeter Defense Perimeter Defense: • Combat DNS, code injection, malware, data leaks • Countermeasures- Data validation, input validation, pattern-based Consume Expose scanning, heuristics, anti-virus, and malware Service/API Level • Centralized, monitored access to code • Versioning & change control policy Coordinated management of these security concerns across departments, developers, and architects is problematic 6
- 7. Five Enterprise API Usage Patterns • Supporting Partners with APIs and Web Services • Supporting Mobile Use of Enterprise Services • Controlling Use of Cloud Infrastructure as a Service • Controlling and Securing Platform as a Service Applications • Supporting Use of Valuable Data in the Cloud 7
- 8. Supporting Mobile Use of Enterprise Services 8
- 9. Controlling Use of Cloud Infrastructure as a Service 9
- 10. Chad Holmes Enterprise Security Architect McAfee DLP 10
- 11. Data Protection Challenges Regulated Data Enabling Business 2.0 Sensitive Data • Comply with multiple • Support supply chain • Protect intellectual regulations & partner integration property • Reduce costs • Support safe, flexible • Maintain competitive associated with audit use of business data advantage • Protect reputation & • Enable safe, two-way, • Ensure appropriate reduce penalties B2B/C communication chain of custody 11
- 12. The Reason for a Data Loss Program Verizon Data Breach Investigations Report 12
- 13. Verticals Ahead Of The DLP Wave REGULATION SECRET DATA 13
- 14. Data Types per Verticals Health Codes Patient Records Drug Formulas REGULATION MRI Images Social Security Numbers Account Numbers Routing Numbers Revenue CCN Employee Data Gov. Forms Source code Gov. ID Numbers CCN Government Secrets Pipelines Docs Control Data Design Schemas SECRET DATA Power and Performance Data Source code Source code Trade Secrets Designs Employee Data Patents Price Lists 14
- 15. Data Types per Data Loss Percentage Verizon Data Breach Investigations Report 15
- 16. Framing The Data Loss Problem Data Types Data Loss Vectors Solution Data-in-Motion Network Email Web Post Network IM Chat Data-at-Rest File Share Network & Database Desktop Endpoint Laptop Data-in-Use Removable Printer Screen Clipboard Endpoint Media 16
- 17. McAfee Data Loss Prevention Solution Data-At-Rest Egress Point Data-In-Motion Data-In-Use Span/Tap McAfee DLP Endpoint Connected or Disconnected McAfee DLP Discover McAfee DLP Monitor McAfee DLP Prevent PC/Laptop McAfee Web Gateway McAfee Email Gateway Protection Rules File Shares Databases McAfee ePO/Manager Management Data Connection Server Farm 17
- 18. Gateway Design Pattern Native mobile Enterprise Gateway – Security Decoupling Application applications and partner services When • Architectural best practice for exposing and consuming API communication • Product agnostic • Relies on indirection to solve security, performance and management problems • Applies nicely for app to app traffic All problems in computer science can be solved by another level of indirection - David Wheeler "...except for the problem of too many layers of indirection.“ – Kevlin Henny 18
- 19. Blake Dournaee Product Management Intel Application Security & Identity Products 19
- 20. Mobile-enabling a legacy SOAP service in 6 steps 20
- 21. Mobile-enabling a legacy SOAP service in 6 steps Receive REST call Structural and semantic threats Throttle and rate shape OAuth authentication and ID extraction REST to SOAP Augment and Transform Invoke legacy SOAP backend Structural and semantic threats Trap data leaks and Malware back to the client 21
- 22. Example: API Authentication with OAuth Policy-Driven Security • Reduces coding • Improves consistency • Centralizes policies • Improves security • Enterprise grade 22
- 23. Service Gateway: Delivers API Gateway Pattern Service API Data Mediation Security Transformation Enterprise “Very Strong Developer – Focused Product” - Analyst -Analyst Review Any Protocol Offload Security Certifications Codeless Policy Design • OWASP top 10 • Common Criteria EAL 4+ • Route Services • REST, SOAP, JSON • • ID Brokering DOD STIG PKI • Complex Exception • XML, non XML • Message & transport • HSM PKI Key Storage Handling • Http, FTP, TCP • Attachment Scanning • Tamper proof hardware • Configuration not code • DOS & Malware • Cavium Crypto 23
- 24. Modern SaaS Application Architecture with API Gateway 24
- 25. New API White Paper 50% Coupon Code for On-demand API Dan’s API Strategy Webinars Guide (ebook) Discount code: ADAPSTG shop.oreilly.com www.cloudsecurity.intel.com www.mcafee.com/cloudsecurity 25
Hinweis der Redaktion
- Title: Enterprise API Best Practices (John) – ~15 slides – Talk for 25-30 minutes I. API Evolution – Where did they come from? (6-8 slides) a. APIs evolved from SOA as services b. Now they are pervasive – REST/JSON is king c. 2011 API growth was huge – what will 2012 look like? d. API business model slides – which types of businesses benefit the most from APIs? (Blake to help with this) e. Comparison to website – APIs are the new “website” II. Categories: Open APIs versus Private APIs (4 slides) a. Open APIs focus on developer on-boarding and platform enablement – name examples b. Private APIs (Enterprise APIs) focus on security, scalability, and availability – name examples of these (if you have some) c. For Enterprise APIs, developer on-boarding is less of an issueIII. Hosted vs On-Premise (1-2 slides) a. What are the pros and cons of hosting an API through an enabler service (Mashery/APIgee) versus doing it yourself.b. Hosted – Good for open APIs, as the developer community is more importantc. On-Premise – Good for private/enterprise grade APIs, as security and scalability are paramount (Blake) – 8 to 10 slides – Talk for 10-15 minutes III. Enterprise Use cases – Types of things an Enterprise wants to do (1-2 slides)IV. The value of the gateway pattern – abstraction (consuming APIs) and security (protecting APIs) – (2 slides)V. Security overview – threats, trust, anti-malware, data loss prevention (1 slide)VI. Intel Expressway Product Pitch (2 slides)VII. Customer Examples (2 slides)
- An authenticated client can still pose a threat. Attacks such as denial-of-service, code injection, malware, and data leaks must all be accounted for when designing an Enterprise API strategy. Tactics such as data validation, input validation, pattern-based scanning, heuristics, anti-virus s
- When it comes to DLP Challenges.. I normally see There are three main pillars in Data Protection that an organization looksfor a DLP solution to resolve.. One is meeting Regulations that are being force down on them… Helping them to automate and resolve the auditing burdomNext, it to enable business units and functions.. , They need to protect their data but at the same time still maintain business needs and requirements Third is around the core piece of DLP which is the Data, How to protect the sensitive data at all times no matter what type of data it is.. If it is PHI, PII, IP or what…
- The first step in fixing your data loss problem is to frame it in a way that encompasses everything– all data types and all potential vectors of leakage. Understanding this framework is a fundamental part of understanding your data.(Explain DiM, DaR, DiU, examples and the solution for each vector)
